Hi everyone,
Before we start with the news, I’d like to thank you for your donations and for your support!
We received donations from more than a thousand people in December! I know I talked about this before, but I’ll do it again because this number of donors in a single month is unprecedented. I like to imagine that many people gathered together at the same time just to support our project. It’s humbling and incredibly motivating. I feel really proud of this community and delighted to see how happy you are with our work. Thank you so much to all of you!
Mint 22.3
Linux Mint 22.3 was a very good release. It came out later than we anticipated, but it was very well received. The beta phase was longer than usual, but it allowed us to gather feedback, address many issues, and review some of the choices made during that time, in particular around the newly introduced Cinnamon menu and keyboard layout/IM (Input Method) configuration.
Keyboard Layouts and IM
Work continues on improving input methods. It came to our attention that some users like to use layouts which do not match their physical keyboard when using IM. I spoke with someone who writes in both French and Japanese. I do this myself on an ANSI keyboard using French/US and Mozc. He has different keyboards on different machines, some ISO/French, some Japanese, and he doesn’t care about the physical layout. He just wants the logical layout to be French when writing French and Japanese when using Mozc.
This isn’t something we anticipated, but we want to support it going forward. We’re working on making it possible to set a specific keyboard layout when configuring an input method.
Forums
I’d like to apologize to our forum users for how slow and unreliable the forums were last month. The volume of traffic we receive is extremely high, and it’s mostly coming from AIs, bots, scripts, and web crawlers. It got to the point where our server couldn’t cope and people weren’t able to use the forums.
In addition to the Sucuri WAF, it took us a while to come up with an efficient way to filter bad traffic. If you’re getting 403 errors from the forums right now, please make sure your browser is up to date.
We upgraded the server to give it 10× the CPU capacity and twice the bandwidth.
Users and Account Details
For some reason most Linux desktop environments have come up with their own tools for user administration and account details. It’s a pity because this is typically an area which belongs to distributions and which cannot be and certainly isn’t properly handled by desktops. As a result these tools lack support for a lot of new use cases and they’re not well maintained.
In the next release, the Administration Tool (mintsysadm) will handle user administration and account details in editions where the desktop tools can be hidden.
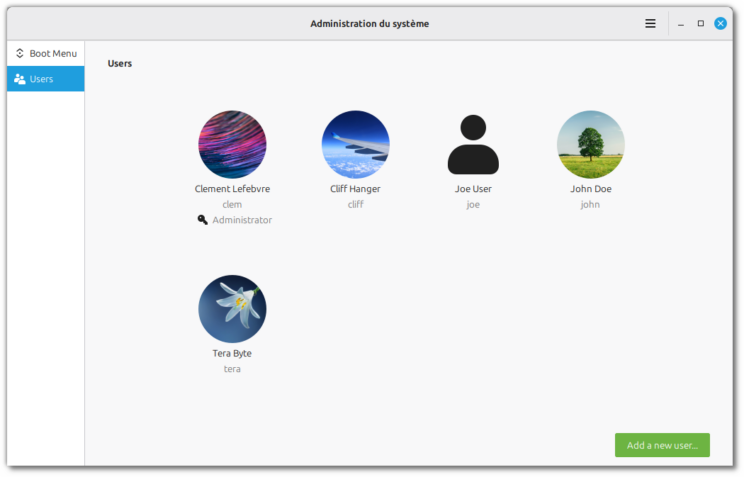
User management in mintsysadm focuses on the most common tasks. Once a user is set up, that user can set up a password and finalize the account without admin intervention. Home directory encryption, which until now was only supported during the OS installation, is fully supported during the creation of new user accounts.
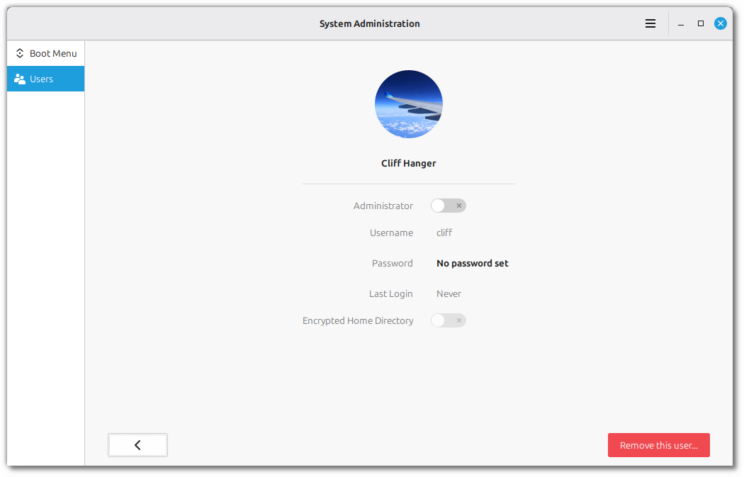
Webcams are fully supported when taking selfies (i.e. you can see yourself before taking the snap, and decide whether to mirror the webcam or not).
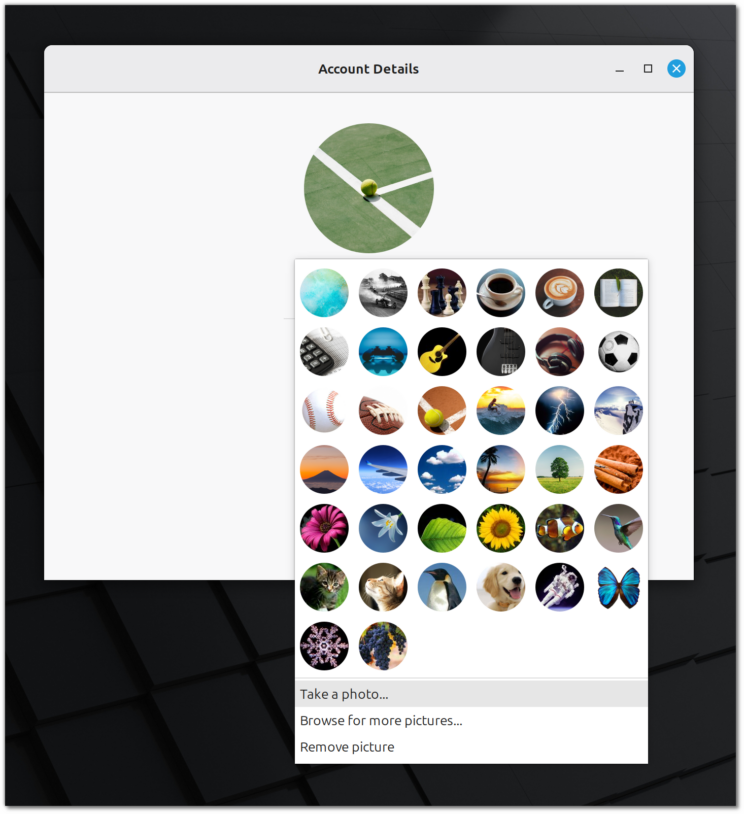
Avatars come with full HiDPI support and look crisp on modern hardware.
Cinnamon Screensaver and Wayland
The Cinnamon screensaver only works in X11. It’s a standalone application which runs in its own process and uses the GTK toolkit. X11 is responsible for making sure it sits on top of Cinnamon’s window manager and hides the windows when the screen is locked.
One of the goals for the next Linux Mint release is to implement a new screensaver which will:
- Replace the existing one
- Work in both Wayland and X11
- Be natively rendered by Cinnamon’s window manager (compositor)
The benefits are significant:
- Smoother transition/animation during screen lock
- Better integrated look and feel (We’ll be using the same toolkit as the one made for the panel, menus, applets)
- Full Wayland support (This is the last missing piece of the puzzle for Cinnamon to fully support Wayland)
This is one of the big things we’re working on right now. I’m not showing you pictures yet until this is ready 
Wayland support so far has been “experimental”. Once all the pieces are in place, we can support it and start testing it as a potential solution. We know there are pros and cons to X11 and Wayland, and we want to support both. Supporting Wayland doesn’t mean we’ll start using it by default, but it makes it a possibility. As always, we’ll end up using what works best for most users.
Longer Development Cycle
If we look back at the last ten years and the projects we invested resources in, we see two things. Well, I see two things anyway, I hope you’ll agree 
I think one of our strengths is that we’re doing things incrementally and changing things slowly. We are introducing change and sometimes it annoys some of our users, but we’re doing it in a way that doesn’t radically affect who we are or the user experience we provide.
Another important strength of ours, as I see it, is that we value our independence and we are able to react and develop our own solutions when we’re not happy with the alternative. We made some bold moves in the past, sticking to LTS, rejecting Snap, developing alternatives to a new GNOME that didn’t feel like GNOME, and I’m really glad we did. These decisions weren’t easy to make and some of them cost a huge amount of time and resources to implement. But looking back, I think they were key. I think we’re first and foremost an operating system: a product, a user experience. We’re also a “distribution”, but we’re not just a distribution.
Whether we “distribute” (for instance with KDE) or we actively develop solutions (for instance with XApp and Cinnamon), we spend a lot of time in release management. Releasing often is important because it means we get a lot of feedback and bug reports when we introduce changes. We follow the same process over and over again. It’s a process that works very well and it produces these incremental improvements release after release. But it takes a lot of time, and it caps our ambition when it comes to development. With a release every six months plus LMDE, we spend more time testing, fixing, and releasing than developing.
We’re thinking about changing that and adopting a longer development cycle. As it happens, our next release will be based on a new LTS and we just ran out of codenames 
Stay tuned, we’ll have more information on this. Obviously the codenames strategy doesn’t matter much, but we are very interested in adopting a longer development cycle.
Sponsorships:
Linux Mint is proudly sponsored by:
Gold Sponsors:


Silver Sponsors:


 |
Bronze Sponsors:






 |
Donations in December:
A total of $47,312 were raised thanks to the generous contributions of 1,393 donors:
 $1000 (8th donation), Gerald L.
$1000 (8th donation), Gerald L.
 $382 (2nd donation), Walter G.
$382 (2nd donation), Walter G.
 $380 (5th donation), Secret Adventures Kauai
$380 (5th donation), Secret Adventures Kauai
 $371 (6th donation), Soldev sàrl
$371 (6th donation), Soldev sàrl
 $360 (2nd donation), IURII M. K.
$360 (2nd donation), IURII M. K.
 $318 (16th donation), Jiří B.
$318 (16th donation), Jiří B.
 $318 (5th donation), Pieter S.
$318 (5th donation), Pieter S.
 $300 (29th donation), John Mc aka “Land Research Project“
$300 (29th donation), John Mc aka “Land Research Project“
 $300, Anonymous
$300, Anonymous
 $265, Dr. M. K.
$265, Dr. M. K.
 $250 (4th donation), William P.
$250 (4th donation), William P.
 $218 (6th donation), Michael M.
$218 (6th donation), Michael M.
 $212 (8th donation), Marcus H.
$212 (8th donation), Marcus H.
 $212 (6th donation), Wolfgang S.
$212 (6th donation), Wolfgang S.
 $212 (2nd donation), Lutz K.
$212 (2nd donation), Lutz K.
 $212 (2nd donation), Marco Q.
$212 (2nd donation), Marco Q.
 $212, Christian B.
$212, Christian B.
 $200 (19th donation), Tomasz E.
$200 (19th donation), Tomasz E.
 $200 (2nd donation), Gail N.
$200 (2nd donation), Gail N.
 $200, Bob Lee
$200, Bob Lee
 $200, dana C.
$200, dana C.
 $200, Nathan E.
$200, Nathan E.
 $200, P. K.
$200, P. K.
 $200, Thomas J. P.
$200, Thomas J. P.
 $159, Linux-Café Stuttgart Kaltental
$159, Linux-Café Stuttgart Kaltental
 $150 (5th donation), Lee R.
$150 (5th donation), Lee R.
 $150, Janette J.
$150, Janette J.
 $127 (2nd donation), Andre V.
$127 (2nd donation), Andre V.
 $127, Andreas L.
$127, Andreas L.
 $127, Christoph S.
$127, Christoph S.
 $125 (7th donation), Alex O.
$125 (7th donation), Alex O.
 $125, Ian C.
$125, Ian C.
 $120 (2nd donation), Evan R.
$120 (2nd donation), Evan R.
 $120, M.S.
$120, M.S.
 $116 (2nd donation), Thomas M.
$116 (2nd donation), Thomas M.
 $106 (16th donation), Torsten P.
$106 (16th donation), Torsten P.
 $106 (11th donation), Karl H.
$106 (11th donation), Karl H.
 $106 (7th donation), Marek Stapff
$106 (7th donation), Marek Stapff
 $106 (3rd donation), Jukka H.
$106 (3rd donation), Jukka H.
 $106 (3rd donation), TURBOKAN_TR
$106 (3rd donation), TURBOKAN_TR
 $106 (2nd donation), Dirk H.
$106 (2nd donation), Dirk H.
 $106 (2nd donation), Laurens R.
$106 (2nd donation), Laurens R.
 $106 (2nd donation), Malte F.
$106 (2nd donation), Malte F.
 $106 (2nd donation), Michael M.
$106 (2nd donation), Michael M.
 $106, Alenka S.
$106, Alenka S.
 $106, Andrea B.
$106, Andrea B.
 $106, Andreas F. M.
$106, Andreas F. M.
 $106, David G.
$106, David G.
 $106, DR. B. R.
$106, DR. B. R.
 $106, Jens D.
$106, Jens D.
 $106, Jesper R. aka “Kaptajn”
$106, Jesper R. aka “Kaptajn”
 $106, Jörg B.
$106, Jörg B.
 $106, Lars K.
$106, Lars K.
 $106, Lars K.
$106, Lars K.
 $106, Manuel H.
$106, Manuel H.
 $106, Oliver K.
$106, Oliver K.
 $106, Patrick B.
$106, Patrick B.
 $106, Roland L.
$106, Roland L.
 $106, Stefan P.
$106, Stefan P.
 $106, Thomas J.
$106, Thomas J.
 $106, tim H.
$106, tim H.
 $106, tobiasblaser.ch GmbH
$106, tobiasblaser.ch GmbH
 $106, VITTORINO D.
$106, VITTORINO D.
 $106, Yvonne T.
$106, Yvonne T.
 $106, ZDENĚK ČERVENKA aka “neo75”
$106, ZDENĚK ČERVENKA aka “neo75”
 $100 (15th donation), Mountain Computers, Inc aka “MTNCOMP aka GGPCTU“
$100 (15th donation), Mountain Computers, Inc aka “MTNCOMP aka GGPCTU“
 $100 (15th donation), James F.
$100 (15th donation), James F.
 $100 (12th donation), Michael S.
$100 (12th donation), Michael S.
 $100 (11th donation), Richard H.
$100 (11th donation), Richard H.
 $100 (5th donation), Jan A.
$100 (5th donation), Jan A.
 $100 (5th donation), JimQ
$100 (5th donation), JimQ
 $100 (5th donation), Matt S.
$100 (5th donation), Matt S.
 $100 (5th donation), Michel R.
$100 (5th donation), Michel R.
 $100 (4th donation), Larry M.
$100 (4th donation), Larry M.
 $100 (3rd donation), Andreas K.
$100 (3rd donation), Andreas K.
 $100 (3rd donation), James M.
$100 (3rd donation), James M.
 $100 (3rd donation), John M.
$100 (3rd donation), John M.
 $100 (3rd donation), Kirby S.
$100 (3rd donation), Kirby S.
 $100 (3rd donation), Robert S.
$100 (3rd donation), Robert S.
 $100 (2nd donation), Snap Programming and Development LLC
$100 (2nd donation), Snap Programming and Development LLC
 $100 (2nd donation), Janice H.
$100 (2nd donation), Janice H.
 $100 (2nd donation), Patrick A.
$100 (2nd donation), Patrick A.
 $100 (2nd donation), Peter W.
$100 (2nd donation), Peter W.
 $100 (2nd donation), Steve
$100 (2nd donation), Steve
 $100 (2nd donation), Tim H.
$100 (2nd donation), Tim H.
 $100, Adam M.
$100, Adam M.
 $100, Brandon T.
$100, Brandon T.
 $100, Bruno H.
$100, Bruno H.
 $100, Charles C.
$100, Charles C.
 $100, David C.
$100, David C.
 $100, Gary E.
$100, Gary E.
 $100, Jim W.
$100, Jim W.
 $100, John D.
$100, John D.
 $100, John L.
$100, John L.
 $100, Kevin J.
$100, Kevin J.
 $100, Kyle C.
$100, Kyle C.
 $100, Mario D.
$100, Mario D.
 $100, NILS K.
$100, NILS K.
 $100, Ted F.
$100, Ted F.
 $100, thomas K.
$100, thomas K.
 $100, William B.
$100, William B.
 $84 (3rd donation), Jean-françois G.
$84 (3rd donation), Jean-françois G.
 $84, Claudia D.
$84, Claudia D.
 $75, Hayden J.
$75, Hayden J.
 $75, Thomas C.
$75, Thomas C.
 $75, Vincent N. M.
$75, Vincent N. M.
 $74 (7th donation), Jean-baptiste P.
$74 (7th donation), Jean-baptiste P.
 $74, Theoharis T.
$74, Theoharis T.
 $73 (2nd donation), Tim D.
$73 (2nd donation), Tim D.
 $71, Peter C.S. Scholtens
$71, Peter C.S. Scholtens
 $63 (4th donation), Edoardo R.
$63 (4th donation), Edoardo R.
 $63 (3rd donation), Katharina G.
$63 (3rd donation), Katharina G.
 $63, Christian S.
$63, Christian S.
 $63, Lukas Z.
$63, Lukas Z.
 $63, Tony J.
$63, Tony J.
 $60 (7th donation), David K.
$60 (7th donation), David K.
 $60, Michael J. L.
$60, Michael J. L.
 $58 (2nd donation), Wolfgang Vee aka “elch01”
$58 (2nd donation), Wolfgang Vee aka “elch01”
 $57 (4th donation), VVV
$57 (4th donation), VVV
 $53 (27th donation), Hans J.
$53 (27th donation), Hans J.
 $53 (24th donation), Bjarne K.
$53 (24th donation), Bjarne K.
 $53 (24th donation), Naoise G. aka “Gaff”
$53 (24th donation), Naoise G. aka “Gaff”
 $53 (19th donation), Paul S. E. aka “Paul”
$53 (19th donation), Paul S. E. aka “Paul”
 $53 (17th donation), Christian G. aka “Chrissy”
$53 (17th donation), Christian G. aka “Chrissy”
 $53 (14th donation), Jyrki A.
$53 (14th donation), Jyrki A.
 $53 (12th donation), More Linux
$53 (12th donation), More Linux
 $53 (11th donation), Martin R.
$53 (11th donation), Martin R.
 $53 (10th donation), Jürgen F.
$53 (10th donation), Jürgen F.
 $53 (9th donation), Jose L. D.
$53 (9th donation), Jose L. D.
 $53 (8th donation), Armin F.
$53 (8th donation), Armin F.
 $53 (7th donation), Christian T.
$53 (7th donation), Christian T.
 $53 (7th donation), erwn16 aka “erwn”
$53 (7th donation), erwn16 aka “erwn”
 $53 (7th donation), Luis R.
$53 (7th donation), Luis R.
 $53 (7th donation), Marco van den Berg
$53 (7th donation), Marco van den Berg
 $53 (6th donation), akaIDIOT
$53 (6th donation), akaIDIOT
 $53 (6th donation), Anton M.
$53 (6th donation), Anton M.
 $53 (6th donation), Colin H.
$53 (6th donation), Colin H.
 $53 (6th donation), Florian L.
$53 (6th donation), Florian L.
 $53 (6th donation), PulpKult
$53 (6th donation), PulpKult
 $53 (6th donation), Wielant B.
$53 (6th donation), Wielant B.
 $53 (5th donation), Athanasios M.
$53 (5th donation), Athanasios M.
 $53 (5th donation), Marius M.
$53 (5th donation), Marius M.
 $53 (5th donation), Peter G.
$53 (5th donation), Peter G.
 $53 (5th donation), Stefan G.
$53 (5th donation), Stefan G.
 $53 (4th donation), Alexandre H.
$53 (4th donation), Alexandre H.
 $53 (4th donation), Andreas N.
$53 (4th donation), Andreas N.
 $53 (4th donation), Hans-peter M.
$53 (4th donation), Hans-peter M.
 $53 (4th donation), Ian C.
$53 (4th donation), Ian C.
 $53 (4th donation), Pascal B.
$53 (4th donation), Pascal B.
 $53 (4th donation), Vincent
$53 (4th donation), Vincent
 $53 (4th donation), Wolfgang W.
$53 (4th donation), Wolfgang W.
 $53 (3rd donation), Arie N.
$53 (3rd donation), Arie N.
 $53 (3rd donation), Benoît H.
$53 (3rd donation), Benoît H.
 $53 (3rd donation), Hubert S.
$53 (3rd donation), Hubert S.
 $53 (3rd donation), Kai K.
$53 (3rd donation), Kai K.
 $53 (3rd donation), Kati S.
$53 (3rd donation), Kati S.
 $53 (3rd donation), Ludovic M.
$53 (3rd donation), Ludovic M.
 $53 (3rd donation), Martin M.
$53 (3rd donation), Martin M.
 $53 (3rd donation), Peter B.
$53 (3rd donation), Peter B.
 $53 (3rd donation), Reinhard B.
$53 (3rd donation), Reinhard B.
 $53 (3rd donation), Salvatore C.
$53 (3rd donation), Salvatore C.
 $53 (3rd donation), Sebastian Münch
$53 (3rd donation), Sebastian Münch
 $53 (2nd donation), Andreas B.
$53 (2nd donation), Andreas B.
 $53 (2nd donation), C. J.
$53 (2nd donation), C. J.
 $53 (2nd donation), Claudia H.
$53 (2nd donation), Claudia H.
 $53 (2nd donation), Dominik S.
$53 (2nd donation), Dominik S.
 $53 (2nd donation), Eckart H.
$53 (2nd donation), Eckart H.
 $53 (2nd donation), G.J. Doornink
$53 (2nd donation), G.J. Doornink
 $53 (2nd donation), Hans S.
$53 (2nd donation), Hans S.
 $53 (2nd donation), Hendrik S.
$53 (2nd donation), Hendrik S.
 $53 (2nd donation), Herbert Jan K.
$53 (2nd donation), Herbert Jan K.
 $53 (2nd donation), Holger S.
$53 (2nd donation), Holger S.
 $53 (2nd donation), Klaus S.
$53 (2nd donation), Klaus S.
 $53 (2nd donation), Markus S.
$53 (2nd donation), Markus S.
 $53 (2nd donation), Michael V.
$53 (2nd donation), Michael V.
 $53 (2nd donation), Paolo Z.
$53 (2nd donation), Paolo Z.
 $53 (2nd donation), Peter K.
$53 (2nd donation), Peter K.
 $53 (2nd donation), Philippe E.
$53 (2nd donation), Philippe E.
 $53 (2nd donation), Raymond L.
$53 (2nd donation), Raymond L.
 $53 (2nd donation), Robert G.
$53 (2nd donation), Robert G.
 $53 (2nd donation), Ronny J.
$53 (2nd donation), Ronny J.
 $53 (2nd donation), Seb aka “mr.pip”
$53 (2nd donation), Seb aka “mr.pip”
 $53 (2nd donation), Silvan S.
$53 (2nd donation), Silvan S.
 $53 (2nd donation), Simon W.
$53 (2nd donation), Simon W.
 $53 (2nd donation), Stefan A.
$53 (2nd donation), Stefan A.
 $53 (2nd donation), Stefan G.
$53 (2nd donation), Stefan G.
 $53 (2nd donation), Thomas K.
$53 (2nd donation), Thomas K.
 $53 (2nd donation), Volker W.
$53 (2nd donation), Volker W.
 $53, Andre M.
$53, Andre M.
 $53, Andrea B.
$53, Andrea B.
 $53, Andreas Z.
$53, Andreas Z.
 $53, AndyNL
$53, AndyNL
 $53, Armin S.
$53, Armin S.
 $53, Austin J. S.
$53, Austin J. S.
 $53, BOGDAN C. C.
$53, BOGDAN C. C.
 $53, Camille P.
$53, Camille P.
 $53, canitzp
$53, canitzp
 $53, Christian K.
$53, Christian K.
 $53, Christian S.
$53, Christian S.
 $53, Christophe B.
$53, Christophe B.
 $53, Daniel
$53, Daniel
 $53, Dario R.
$53, Dario R.
 $53, Darshaka P.
$53, Darshaka P.
 $53, Detlef H.
$53, Detlef H.
 $53, Di G. L.
$53, Di G. L.
 $53, di G. L.
$53, di G. L.
 $53, didier M.
$53, didier M.
 $53, Dieter H.
$53, Dieter H.
 $53, Dirk Annema
$53, Dirk Annema
 $53, Dirk M.
$53, Dirk M.
 $53, Dominik B.
$53, Dominik B.
 $53, Egmont S.
$53, Egmont S.
 $53, Emile T.
$53, Emile T.
 $53, EUGENIO B.
$53, EUGENIO B.
 $53, Fabian S.
$53, Fabian S.
 $53, Finley M.
$53, Finley M.
 $53, Florian K.
$53, Florian K.
 $53, Frank
$53, Frank
 $53, Frank H.
$53, Frank H.
 $53, Frank S.
$53, Frank S.
 $53, Gerald K.
$53, Gerald K.
 $53, Giancarlo G.
$53, Giancarlo G.
 $53, Gilles
$53, Gilles
 $53, Gisela T.
$53, Gisela T.
 $53, Isolde M. B.
$53, Isolde M. B.
 $53, Ivo H.
$53, Ivo H.
 $53, Jan G.
$53, Jan G.
 $53, jan V.
$53, jan V.
 $53, Javier G. V.
$53, Javier G. V.
 $53, Jens W.
$53, Jens W.
 $53, Jim R.
$53, Jim R.
 $53, Joachim S.
$53, Joachim S.
 $53, Joao M. aka “DeLinuxCo”
$53, Joao M. aka “DeLinuxCo”
 $53, Johannes G.
$53, Johannes G.
 $53, Johannes W.
$53, Johannes W.
 $53, Jon B.
$53, Jon B.
 $53, Julian H.
$53, Julian H.
 $53, Jürgen W.
$53, Jürgen W.
 $53, Klaus S.
$53, Klaus S.
 $53, Knut G.
$53, Knut G.
 $53, Krings D.
$53, Krings D.
 $53, Lars P.
$53, Lars P.
 $53, LAURA N.
$53, LAURA N.
 $53, Leendert-Jan F.
$53, Leendert-Jan F.
 $53, Marco O.
$53, Marco O.
 $53, Marianne R.
$53, Marianne R.
 $53, Markus N.
$53, Markus N.
 $53, Martin .
$53, Martin .
 $53, Massimo L.
$53, Massimo L.
 $53, Matjaz C. aka “TitoJBroz”
$53, Matjaz C. aka “TitoJBroz”
 $53, MIchael B.
$53, MIchael B.
 $53, Michael S.
$53, Michael S.
 $53, Michele M.
$53, Michele M.
 $53, Mike L.
$53, Mike L.
 $53, Milan M.
$53, Milan M.
 $53, Musie B.
$53, Musie B.
 $53, Oliver P.
$53, Oliver P.
 $53, one2seven GmbH
$53, one2seven GmbH
 $53, OSL Learning & Media Ltd
$53, OSL Learning & Media Ltd
 $53, Peter Z.
$53, Peter Z.
 $53, Ralf F.
$53, Ralf F.
 $53, Ralph G.
$53, Ralph G.
 $53, razes G.
$53, razes G.
 $53, Rickard S.
$53, Rickard S.
 $53, Robert S.
$53, Robert S.
 $53, Roland G
$53, Roland G
 $53, Roland K.
$53, Roland K.
 $53, RONALD O.
$53, RONALD O.
 $53, Ronald S.
$53, Ronald S.
 $53, Sebastian K.
$53, Sebastian K.
 $53, Simon P.
$53, Simon P.
 $53, Sooom.de / Thomas Schäfer
$53, Sooom.de / Thomas Schäfer
 $53, Stefan H.
$53, Stefan H.
 $53, Stefan K.
$53, Stefan K.
 $53, Stefan Z.
$53, Stefan Z.
 $53, Sven D.
$53, Sven D.
 $53, Sven N.
$53, Sven N.
 $53, Thierry V.
$53, Thierry V.
 $53, thomas K.
$53, thomas K.
 $53, Thomas P.
$53, Thomas P.
 $53, Tilen B.
$53, Tilen B.
 $53, tomas M.
$53, tomas M.
 $53, Tomi G.
$53, Tomi G.
 $53, Uwe G.
$53, Uwe G.
 $53, Ville O.
$53, Ville O.
 $53, W.H.MOLLOY
$53, W.H.MOLLOY
 $53, Waldemar S.
$53, Waldemar S.
 $53, William M.
$53, William M.
 $53, Wolf K.
$53, Wolf K.
 $53, Wolfgang S.
$53, Wolfgang S.
 $53, Yannick B.
$53, Yannick B.
 $51 (23rd donation), Adam K.
$51 (23rd donation), Adam K.
 $50 (15th donation), Mothy
$50 (15th donation), Mothy
 $50 (12th donation), Anthony C. aka “Ciak”
$50 (12th donation), Anthony C. aka “Ciak”
 $50 (11th donation), Christophe Caillé aka “KKY”
$50 (11th donation), Christophe Caillé aka “KKY”
 $50 (11th donation), Stuart B.
$50 (11th donation), Stuart B.
 $50 (10th donation), William G.
$50 (10th donation), William G.
 $50 (9th donation), Stacey F.
$50 (9th donation), Stacey F.
 $50 (8th donation), Brian S.
$50 (8th donation), Brian S.
 $50 (8th donation), GELvdH
$50 (8th donation), GELvdH
 $50 (6th donation), Chris C.
$50 (6th donation), Chris C.
 $50 (6th donation), Harrison W.
$50 (6th donation), Harrison W.
 $50 (6th donation), Kurt T.
$50 (6th donation), Kurt T.
 $50 (6th donation), Stephen C.
$50 (6th donation), Stephen C.
 $50 (5th donation), Don aka “Don“
$50 (5th donation), Don aka “Don“
 $50 (5th donation), Doug S.
$50 (5th donation), Doug S.
 $50 (5th donation), Guillermo A.
$50 (5th donation), Guillermo A.
 $50 (4th donation), Brian B.
$50 (4th donation), Brian B.
 $50 (4th donation), Chad B.
$50 (4th donation), Chad B.
 $50 (4th donation), David Diaz
$50 (4th donation), David Diaz
 $50 (4th donation), Evan S.
$50 (4th donation), Evan S.
 $50 (4th donation), Ivan D.
$50 (4th donation), Ivan D.
 $50 (4th donation), John D.
$50 (4th donation), John D.
 $50 (4th donation), Julie A G.
$50 (4th donation), Julie A G.
 $50 (4th donation), Khalid T. aka “k9750”
$50 (4th donation), Khalid T. aka “k9750”
 $50 (4th donation), Peter C.
$50 (4th donation), Peter C.
 $50 (4th donation), Robert L.
$50 (4th donation), Robert L.
 $50 (3rd donation), Alan G.
$50 (3rd donation), Alan G.
 $50 (3rd donation), Alejandro R.
$50 (3rd donation), Alejandro R.
 $50 (3rd donation), Dan B.
$50 (3rd donation), Dan B.
 $50 (3rd donation), David B.
$50 (3rd donation), David B.
 $50 (3rd donation), Dominic M.
$50 (3rd donation), Dominic M.
 $50 (3rd donation), Eddie B.
$50 (3rd donation), Eddie B.
 $50 (3rd donation), Josh G.
$50 (3rd donation), Josh G.
 $50 (3rd donation), Mark M.
$50 (3rd donation), Mark M.
 $50 (3rd donation), Michael M.
$50 (3rd donation), Michael M.
 $50 (3rd donation), P D.
$50 (3rd donation), P D.
 $50 (3rd donation), Peter L.
$50 (3rd donation), Peter L.
 $50 (3rd donation), Sharon S.
$50 (3rd donation), Sharon S.
 $50 (2nd donation), Allan C.
$50 (2nd donation), Allan C.
 $50 (2nd donation), Bruce L.
$50 (2nd donation), Bruce L.
 $50 (2nd donation), Christopher D.
$50 (2nd donation), Christopher D.
 $50 (2nd donation), Eugene W.
$50 (2nd donation), Eugene W.
 $50 (2nd donation), John B.
$50 (2nd donation), John B.
 $50 (2nd donation), Michael H.
$50 (2nd donation), Michael H.
 $50 (2nd donation), Rusty D.
$50 (2nd donation), Rusty D.
 $50 (2nd donation), Shawn S.
$50 (2nd donation), Shawn S.
 $50 (2nd donation), Stefan D.
$50 (2nd donation), Stefan D.
 $50, Adriaan V.
$50, Adriaan V.
 $50, anonymouns
$50, anonymouns
 $50, Anonymous
$50, Anonymous
 $50, Brad S.
$50, Brad S.
 $50, Charles L.
$50, Charles L.
 $50, Curtis M.
$50, Curtis M.
 $50, Dana H.
$50, Dana H.
 $50, David L. B.
$50, David L. B.
 $50, David N.
$50, David N.
 $50, Denny F.
$50, Denny F.
 $50, Diego S.
$50, Diego S.
 $50, Doug S.
$50, Doug S.
 $50, Douglas B.
$50, Douglas B.
 $50, Evan S.
$50, Evan S.
 $50, Felix C.
$50, Felix C.
 $50, Garry G.
$50, Garry G.
 $50, George W.
$50, George W.
 $50, James W.
$50, James W.
 $50, Jason E.
$50, Jason E.
 $50, john B.
$50, john B.
 $50, Joshua H.
$50, Joshua H.
 $50, Josiah H.
$50, Josiah H.
 $50, Kai H.
$50, Kai H.
 $50, Kathleen K.
$50, Kathleen K.
 $50, Keir J.
$50, Keir J.
 $50, Kurt K.
$50, Kurt K.
 $50, Loren D.
$50, Loren D.
 $50, Mark M.
$50, Mark M.
 $50, Michael C.
$50, Michael C.
 $50, Michael L.
$50, Michael L.
 $50, Michael S.
$50, Michael S.
 $50, Mitchell W.
$50, Mitchell W.
 $50, Nathan
$50, Nathan
 $50, Nickolas B.
$50, Nickolas B.
 $50, Phillips H.
$50, Phillips H.
 $50, Piotr S.
$50, Piotr S.
 $50, Praneeth
$50, Praneeth
 $50, Randy L. aka “R.D.”
$50, Randy L. aka “R.D.”
 $50, Ricardo P.
$50, Ricardo P.
 $50, Riley W.
$50, Riley W.
 $50, Robert B.
$50, Robert B.
 $50, Robert G.
$50, Robert G.
 $50, Robert S.
$50, Robert S.
 $50, Ron F.
$50, Ron F.
 $50, Rose P.
$50, Rose P.
 $50, Shaun J. V. N.
$50, Shaun J. V. N.
 $50, Shawn H.
$50, Shawn H.
 $50, Stanley V.
$50, Stanley V.
 $50, THOMAS R.
$50, THOMAS R.
 $50, wayne G.
$50, wayne G.
 $49 (9th donation), GASHIGULLIN D.
$49 (9th donation), GASHIGULLIN D.
 $48 (6th donation), Ingo S.
$48 (6th donation), Ingo S.
 $47, Ronny K.
$47, Ronny K.
 $45 (7th donation), Lloyd H.
$45 (7th donation), Lloyd H.
 $44, WALLY J.
$44, WALLY J.
 $42 (12th donation), Pavel B.
$42 (12th donation), Pavel B.
 $42 (9th donation), Frank W.
$42 (9th donation), Frank W.
 $42 (7th donation), Mathias P.
$42 (7th donation), Mathias P.
 $42 (5th donation), Björn H.
$42 (5th donation), Björn H.
 $42 (2nd donation), Jörg W.
$42 (2nd donation), Jörg W.
 $42 (2nd donation), Steffen G.
$42 (2nd donation), Steffen G.
 $42 (2nd donation), Walter W.
$42 (2nd donation), Walter W.
 $42, Alexander B.
$42, Alexander B.
 $42, Alexander L. aka “Lexolas”
$42, Alexander L. aka “Lexolas”
 $42, Antonio B.
$42, Antonio B.
 $42, Elia V.
$42, Elia V.
 $42, Hannelore O.
$42, Hannelore O.
 $42, Hannes B.
$42, Hannes B.
 $42, Joerg F.
$42, Joerg F.
 $42, Julia S.
$42, Julia S.
 $42, Martin K.
$42, Martin K.
 $42, Uwe K.
$42, Uwe K.
 $41, Alfredo Cattaneo
$41, Alfredo Cattaneo
 $40 (3rd donation), Cecil H.
$40 (3rd donation), Cecil H.
 $40 (3rd donation), Charles W.
$40 (3rd donation), Charles W.
 $40, Jude M. M.
$40, Jude M. M.
 $40, Ryan S.
$40, Ryan S.
 $38 (2nd donation), Tommi AV aka “Tombie75”
$38 (2nd donation), Tommi AV aka “Tombie75”
 $37 (2nd donation), Karl A.
$37 (2nd donation), Karl A.
 $37 (2nd donation), Thomas K.
$37 (2nd donation), Thomas K.
 $37 (2nd donation), Walter G.
$37 (2nd donation), Walter G.
 $37, Lukas W.
$37, Lukas W.
 $37, Thomas K.
$37, Thomas K.
 $36 (2nd donation), tommy W.
$36 (2nd donation), tommy W.
 $36 (2nd donation), 何源
$36 (2nd donation), 何源
 $36, Sheldon B.
$36, Sheldon B.
 $35 (8th donation), Ricardo M.
$35 (8th donation), Ricardo M.
 $35 (8th donation), Thomas H.
$35 (8th donation), Thomas H.
 $35 (5th donation), Steven H.
$35 (5th donation), Steven H.
 $35 (4th donation), Keith P.
$35 (4th donation), Keith P.
 $35 (3rd donation), Carol B.
$35 (3rd donation), Carol B.
 $35 (3rd donation), Rodney M.
$35 (3rd donation), Rodney M.
 $35, Amarjit B.
$35, Amarjit B.
 $35, David J. C.
$35, David J. C.
 $35, Dennis B. O.
$35, Dennis B. O.
 $35, JAIME P. B.
$35, JAIME P. B.
 $35, Müller S.
$35, Müller S.
 $35, Steven L.
$35, Steven L.
 $32 (4th donation), Harry F.
$32 (4th donation), Harry F.
 $31 (15th donation), Bill Metzenthen
$31 (15th donation), Bill Metzenthen
 $31 (12th donation), Alexander M.
$31 (12th donation), Alexander M.
 $31 (11th donation), Peter aka “miesepeter”
$31 (11th donation), Peter aka “miesepeter”
 $31 (9th donation), Daniel K.
$31 (9th donation), Daniel K.
 $31 (8th donation), Alessio B.
$31 (8th donation), Alessio B.
 $31 (8th donation), Wolfgang S.
$31 (8th donation), Wolfgang S.
 $31 (6th donation), Gerard B. aka “Djé”
$31 (6th donation), Gerard B. aka “Djé”
 $31 (5th donation), Amir Perviz
$31 (5th donation), Amir Perviz
 $31 (5th donation), Johann K.
$31 (5th donation), Johann K.
 $31 (4th donation), Floris V.
$31 (4th donation), Floris V.
 $31 (4th donation), Marcus R.
$31 (4th donation), Marcus R.
 $31 (3rd donation), Boris B.
$31 (3rd donation), Boris B.
 $31 (3rd donation), Manfred S.
$31 (3rd donation), Manfred S.
 $31 (3rd donation), Stephen M.
$31 (3rd donation), Stephen M.
 $31 (2nd donation), Erwin T.
$31 (2nd donation), Erwin T.
 $31 (2nd donation), Jahn Baers
$31 (2nd donation), Jahn Baers
 $31 (2nd donation), Joseph D.
$31 (2nd donation), Joseph D.
 $31 (2nd donation), Klaus D. J.
$31 (2nd donation), Klaus D. J.
 $31 (2nd donation), Tony M.
$31 (2nd donation), Tony M.
 $31, Andreas L.
$31, Andreas L.
 $31, Antje K.
$31, Antje K.
 $31, DAVID M.
$31, DAVID M.
 $31, Florian N.
$31, Florian N.
 $31, Frank A.
$31, Frank A.
 $31, Gérard P.
$31, Gérard P.
 $31, Hans J. C.
$31, Hans J. C.
 $31, Joachim G.
$31, Joachim G.
 $31, Lars S.
$31, Lars S.
 $31, Olaf B.
$31, Olaf B.
 $31, Oliver H.
$31, Oliver H.
 $31, Paweł G.
$31, Paweł G.
 $31, Robert M.
$31, Robert M.
 $31, Thomas K.
$31, Thomas K.
 $31, Uwe B.
$31, Uwe B.
 $31, Wolfgang H.
$31, Wolfgang H.
 $30 (9th donation), Bob Tregilus
$30 (9th donation), Bob Tregilus
 $30 (4th donation), Bart L.
$30 (4th donation), Bart L.
 $30 (2nd donation), Christopher W.
$30 (2nd donation), Christopher W.
 $30 (2nd donation), Judy S.
$30 (2nd donation), Judy S.
 $30 (2nd donation), Paul G.
$30 (2nd donation), Paul G.
 $30 (2nd donation), Simon B.
$30 (2nd donation), Simon B.
 $30, Adrian R.
$30, Adrian R.
 $30, Jan W.
$30, Jan W.
 $30, Markus S.
$30, Markus S.
 $30, Russell S.
$30, Russell S.
 $29, Joel M.
$29, Joel M.
 $28, Peter H.
$28, Peter H.
 $27, Gordon S.
$27, Gordon S.
 $26 (16th donation), Roger aka “GNU/Linux werkgroep“
$26 (16th donation), Roger aka “GNU/Linux werkgroep“
 $26 (11th donation), Jürgen B.
$26 (11th donation), Jürgen B.
 $26 (10th donation), Juergen S.
$26 (10th donation), Juergen S.
 $26 (9th donation), Sebastian J.
$26 (9th donation), Sebastian J.
 $26 (5th donation), Fais T.
$26 (5th donation), Fais T.
 $26 (5th donation), Raimund L.
$26 (5th donation), Raimund L.
 $26 (5th donation), Sape S.
$26 (5th donation), Sape S.
 $26 (4th donation), Florian H.
$26 (4th donation), Florian H.
 $26 (4th donation), Mark
$26 (4th donation), Mark
 $26 (4th donation), Rainer G.
$26 (4th donation), Rainer G.
 $26 (4th donation), Robert L.
$26 (4th donation), Robert L.
 $26 (4th donation), Udo J.
$26 (4th donation), Udo J.
 $26 (3rd donation), Alexander B.
$26 (3rd donation), Alexander B.
 $26 (3rd donation), Matthias G.
$26 (3rd donation), Matthias G.
 $26 (2nd donation), Daniel S.
$26 (2nd donation), Daniel S.
 $26 (2nd donation), Daniil S.
$26 (2nd donation), Daniil S.
 $26 (2nd donation), Dirk D.
$26 (2nd donation), Dirk D.
 $26 (2nd donation), Douglas K.
$26 (2nd donation), Douglas K.
 $26 (2nd donation), Jacob S.
$26 (2nd donation), Jacob S.
 $26 (2nd donation), Marco A.
$26 (2nd donation), Marco A.
 $26 (2nd donation), Philipp H.
$26 (2nd donation), Philipp H.
 $26 (2nd donation), Sébastien T.
$26 (2nd donation), Sébastien T.
 $26 (2nd donation), Sven W.
$26 (2nd donation), Sven W.
 $26, A.B. H.
$26, A.B. H.
 $26, Andreas L.
$26, Andreas L.
 $26, Andreas W.
$26, Andreas W.
 $26, ANTONIO A. G.
$26, ANTONIO A. G.
 $26, Bernardus J. V. Z.
$26, Bernardus J. V. Z.
 $26, Bernhard S.
$26, Bernhard S.
 $26, Bernhard S.
$26, Bernhard S.
 $26, Christian-Marcel C.
$26, Christian-Marcel C.
 $26, Denis S.
$26, Denis S.
 $26, Dieter R.
$26, Dieter R.
 $26, Dr. D. R. N.
$26, Dr. D. R. N.
 $26, Florian G.
$26, Florian G.
 $26, GGK Managementsysteme
$26, GGK Managementsysteme
 $26, Jan Wameling
$26, Jan Wameling
 $26, Jochen G.
$26, Jochen G.
 $26, Lars K.
$26, Lars K.
 $26, Lise C-D
$26, Lise C-D
 $26, Luca S.
$26, Luca S.
 $26, Lynne P.
$26, Lynne P.
 $26, MACE B.
$26, MACE B.
 $26, Michael Z.
$26, Michael Z.
 $26, MR A. W. L.
$26, MR A. W. L.
 $26, Philipp K.
$26, Philipp K.
 $26, Philipp R.
$26, Philipp R.
 $26, Ralf K.
$26, Ralf K.
 $26, Thomas K.
$26, Thomas K.
 $26, Uwe S.
$26, Uwe S.
 $26, Winfried R.
$26, Winfried R.
 $25 (58th donation), Linux Mint Sverige
$25 (58th donation), Linux Mint Sverige
 $25 (22nd donation), Richard N.
$25 (22nd donation), Richard N.
 $25 (18th donation), John W.
$25 (18th donation), John W.
 $25 (18th donation), Vaughan Butler
$25 (18th donation), Vaughan Butler
 $25 (13th donation), Todd W.
$25 (13th donation), Todd W.
 $25 (11th donation), John N.
$25 (11th donation), John N.
 $25 (10th donation), Brian H. Y.
$25 (10th donation), Brian H. Y.
 $25 (10th donation), Edmond I.
$25 (10th donation), Edmond I.
 $25 (10th donation), Robert S.
$25 (10th donation), Robert S.
 $25 (6th donation), Edward C.
$25 (6th donation), Edward C.
 $25 (6th donation), William C.
$25 (6th donation), William C.
 $25 (5th donation), David P.
$25 (5th donation), David P.
 $25 (4th donation), Chris L.
$25 (4th donation), Chris L.
 $25 (4th donation), Thomas S.
$25 (4th donation), Thomas S.
 $25 (3rd donation), Andrew R.
$25 (3rd donation), Andrew R.
 $25 (2nd donation), Chris H.
$25 (2nd donation), Chris H.
 $25 (2nd donation), Daniel B.
$25 (2nd donation), Daniel B.
 $25 (2nd donation), Isahann Hanacleto aka “isahann, isaque, iso“
$25 (2nd donation), Isahann Hanacleto aka “isahann, isaque, iso“
 $25 (2nd donation), Paul G. A.
$25 (2nd donation), Paul G. A.
 $25 (2nd donation), Steven K.
$25 (2nd donation), Steven K.
 $25, Anthony E.
$25, Anthony E.
 $25, Christopher K.
$25, Christopher K.
 $25, Emilie H.
$25, Emilie H.
 $25, Fabricio M. D. S.
$25, Fabricio M. D. S.
 $25, Geoffry B. S.
$25, Geoffry B. S.
 $25, James T.
$25, James T.
 $25, James W.
$25, James W.
 $25, Keshav A.
$25, Keshav A.
 $25, Lincoln R.
$25, Lincoln R.
 $25, Raghu M.
$25, Raghu M.
 $25, Sarah E.
$25, Sarah E.
 $25, wijtske I. R.
$25, wijtske I. R.
 $24 (2nd donation), Ansgar M.
$24 (2nd donation), Ansgar M.
 $24, Roland S.
$24, Roland S.
 $23 (13th donation), Alessandro S.
$23 (13th donation), Alessandro S.
 $23, David L.
$23, David L.
 $22 (13th donation), Malte J.
$22 (13th donation), Malte J.
 $22, Robert H.
$22, Robert H.
 $21 (75th donation), Michael R.
$21 (75th donation), Michael R.
 $21 (66th donation), Peter E.
$21 (66th donation), Peter E.
 $21 (33rd donation), Stefan W.
$21 (33rd donation), Stefan W.
 $21 (31st donation), Doriano G. M.
$21 (31st donation), Doriano G. M.
 $21 (28th donation), Benjamin W. aka “UncleBens”
$21 (28th donation), Benjamin W. aka “UncleBens”
 $21 (19th donation), Janne S.
$21 (19th donation), Janne S.
 $21 (13th donation), Rob B.
$21 (13th donation), Rob B.
 $21 (13th donation), Wolfgang N.
$21 (13th donation), Wolfgang N.
 $21 (12th donation), Anne-christine U.
$21 (12th donation), Anne-christine U.
 $21 (12th donation), Frank V.
$21 (12th donation), Frank V.
 $21 (11th donation), Andreas M.
$21 (11th donation), Andreas M.
 $21 (10th donation), Jaime aka “¡Fuera los gringos de Venezuela! Trump, keep out of Venezuela!”
$21 (10th donation), Jaime aka “¡Fuera los gringos de Venezuela! Trump, keep out of Venezuela!”
 $21 (9th donation), Gerhard A.
$21 (9th donation), Gerhard A.
 $21 (9th donation), Richard L. F.
$21 (9th donation), Richard L. F.
 $21 (9th donation), Vidal Santos
$21 (9th donation), Vidal Santos
 $21 (7th donation), Jim W.
$21 (7th donation), Jim W.
 $21 (7th donation), Juri N.
$21 (7th donation), Juri N.
 $21 (7th donation), M.B.
$21 (7th donation), M.B.
 $21 (7th donation), RobH
$21 (7th donation), RobH
 $21 (7th donation), youme
$21 (7th donation), youme
 $21 (6th donation), Andreas F.
$21 (6th donation), Andreas F.
 $21 (6th donation), Andreas F.
$21 (6th donation), Andreas F.
 $21 (6th donation), Bernd R.
$21 (6th donation), Bernd R.
 $21 (6th donation), Frank R.
$21 (6th donation), Frank R.
 $21 (6th donation), Jaume T.
$21 (6th donation), Jaume T.
 $21 (6th donation), Jens F.
$21 (6th donation), Jens F.
 $21 (5th donation), Andreas Z.
$21 (5th donation), Andreas Z.
 $21 (5th donation), Curt S.
$21 (5th donation), Curt S.
 $21 (5th donation), Daniel K.
$21 (5th donation), Daniel K.
 $21 (5th donation), Daniel S.
$21 (5th donation), Daniel S.
 $21 (5th donation), Helgi J.
$21 (5th donation), Helgi J.
 $21 (5th donation), Hendricus P. D. V.
$21 (5th donation), Hendricus P. D. V.
 $21 (5th donation), Matthias Versen aka “Matti”
$21 (5th donation), Matthias Versen aka “Matti”
 $21 (5th donation), Mili D.
$21 (5th donation), Mili D.
 $21 (5th donation), Nils D. aka “Akron“
$21 (5th donation), Nils D. aka “Akron“
 $21 (5th donation), Olaf K.
$21 (5th donation), Olaf K.
 $21 (4th donation), Andrew G.
$21 (4th donation), Andrew G.
 $21 (4th donation), Benjamin aka “bglamadrid”
$21 (4th donation), Benjamin aka “bglamadrid”
 $21 (4th donation), Daniel L.
$21 (4th donation), Daniel L.
 $21 (4th donation), Heiko K.
$21 (4th donation), Heiko K.
 $21 (4th donation), Ilija C.
$21 (4th donation), Ilija C.
 $21 (4th donation), Luca V.
$21 (4th donation), Luca V.
 $21 (4th donation), Marc R.
$21 (4th donation), Marc R.
 $21 (4th donation), Sean M.
$21 (4th donation), Sean M.
 $21 (4th donation), Stefan Korn – Webentwicklung
$21 (4th donation), Stefan Korn – Webentwicklung
 $21 (4th donation), Volker S.
$21 (4th donation), Volker S.
 $21 (3rd donation), Albert P.
$21 (3rd donation), Albert P.
 $21 (3rd donation), Christian W.
$21 (3rd donation), Christian W.
 $21 (3rd donation), Eero V.
$21 (3rd donation), Eero V.
 $21 (3rd donation), Hristo B.
$21 (3rd donation), Hristo B.
 $21 (3rd donation), Jean-yves D.
$21 (3rd donation), Jean-yves D.
 $21 (3rd donation), Jennifer S.
$21 (3rd donation), Jennifer S.
 $21 (3rd donation), Lucian U.
$21 (3rd donation), Lucian U.
 $21 (3rd donation), Martin M.
$21 (3rd donation), Martin M.
 $21 (3rd donation), Régis P.
$21 (3rd donation), Régis P.
 $21 (3rd donation), Rolf N.
$21 (3rd donation), Rolf N.
 $21 (3rd donation), Thomas O.
$21 (3rd donation), Thomas O.
 $21 (3rd donation), Weinand S.
$21 (3rd donation), Weinand S.
 $21 (2nd donation), André G.
$21 (2nd donation), André G.
 $21 (2nd donation), Andre V.
$21 (2nd donation), Andre V.
 $21 (2nd donation), Andrea K.
$21 (2nd donation), Andrea K.
 $21 (2nd donation), Axel T.
$21 (2nd donation), Axel T.
 $21 (2nd donation), Bernhard S.
$21 (2nd donation), Bernhard S.
 $21 (2nd donation), Bruno L.
$21 (2nd donation), Bruno L.
 $21 (2nd donation), Dieter B.
$21 (2nd donation), Dieter B.
 $21 (2nd donation), E D. M.
$21 (2nd donation), E D. M.
 $21 (2nd donation), Eugene G.
$21 (2nd donation), Eugene G.
 $21 (2nd donation), Fabio R.
$21 (2nd donation), Fabio R.
 $21 (2nd donation), Florian S.
$21 (2nd donation), Florian S.
 $21 (2nd donation), Georg T.
$21 (2nd donation), Georg T.
 $21 (2nd donation), Giampaolo N.
$21 (2nd donation), Giampaolo N.
 $21 (2nd donation), Gojko M.
$21 (2nd donation), Gojko M.
 $21 (2nd donation), Henrik N.
$21 (2nd donation), Henrik N.
 $21 (2nd donation), Hermann C.
$21 (2nd donation), Hermann C.
 $21 (2nd donation), Jean C.
$21 (2nd donation), Jean C.
 $21 (2nd donation), Jens K.
$21 (2nd donation), Jens K.
 $21 (2nd donation), Jörg M.
$21 (2nd donation), Jörg M.
 $21 (2nd donation), Klaus D.
$21 (2nd donation), Klaus D.
 $21 (2nd donation), Letizia C.
$21 (2nd donation), Letizia C.
 $21 (2nd donation), Marc G.
$21 (2nd donation), Marc G.
 $21 (2nd donation), Marc W.
$21 (2nd donation), Marc W.
 $21 (2nd donation), Markus G.
$21 (2nd donation), Markus G.
 $21 (2nd donation), Matthias W.
$21 (2nd donation), Matthias W.
 $21 (2nd donation), Maximilian M.
$21 (2nd donation), Maximilian M.
 $21 (2nd donation), Mike H.
$21 (2nd donation), Mike H.
 $21 (2nd donation), Oliver A.
$21 (2nd donation), Oliver A.
 $21 (2nd donation), Pius Alfred V.
$21 (2nd donation), Pius Alfred V.
 $21 (2nd donation), Sergio C.
$21 (2nd donation), Sergio C.
 $21 (2nd donation), Thomas W.
$21 (2nd donation), Thomas W.
 $21 (2nd donation), Trevor A.
$21 (2nd donation), Trevor A.
 $21 (2nd donation), Yoann P.
$21 (2nd donation), Yoann P.
 $21,
$21,
 $21,
$21,
 $21, aka “Ram”
$21, aka “Ram”
 $21, Abdus S.
$21, Abdus S.
 $21, Adéla P.
$21, Adéla P.
 $21, Albrecht S.
$21, Albrecht S.
 $21, Alejandro M.
$21, Alejandro M.
 $21, Alistair W.
$21, Alistair W.
 $21, Anastasiia Sakharova
$21, Anastasiia Sakharova
 $21, Andrew B.
$21, Andrew B.
 $21, Andrew C.
$21, Andrew C.
 $21, Andrew H.
$21, Andrew H.
 $21, Andy H.
$21, Andy H.
 $21, Barry H.
$21, Barry H.
 $21, Birger V.
$21, Birger V.
 $21, BUITENDIJK J. M.
$21, BUITENDIJK J. M.
 $21, Christian B.
$21, Christian B.
 $21, Christian S.
$21, Christian S.
 $21, Christian S.
$21, Christian S.
 $21, Christoph K.
$21, Christoph K.
 $21, Christophe T.
$21, Christophe T.
 $21, Cristi M. aka “TCristi”
$21, Cristi M. aka “TCristi”
 $21, Damien D.
$21, Damien D.
 $21, Daniel S.
$21, Daniel S.
 $21, Daniele Z.
$21, Daniele Z.
 $21, Darina Z.
$21, Darina Z.
 $21, Dylan O.
$21, Dylan O.
 $21, Felix K.
$21, Felix K.
 $21, Filip K.
$21, Filip K.
 $21, Florian S.
$21, Florian S.
 $21, Frank H.
$21, Frank H.
 $21, Frank K.
$21, Frank K.
 $21, Gildas H.
$21, Gildas H.
 $21, Giovanni G.
$21, Giovanni G.
 $21, Graham G.
$21, Graham G.
 $21, Gregor H.
$21, Gregor H.
 $21, Gregory W.
$21, Gregory W.
 $21, Hans P.
$21, Hans P.
 $21, HARMANNUS J.
$21, HARMANNUS J.
 $21, Harry G.
$21, Harry G.
 $21, Heribert F.
$21, Heribert F.
 $21, Horst R.
$21, Horst R.
 $21, Ian W.
$21, Ian W.
 $21, Jan H.
$21, Jan H.
 $21, Jari K.
$21, Jari K.
 $21, Jaroslaw G.
$21, Jaroslaw G.
 $21, Javier G. M.
$21, Javier G. M.
 $21, JB
$21, JB
 $21, Jean-michel V.
$21, Jean-michel V.
 $21, Jens D.
$21, Jens D.
 $21, Jens K.
$21, Jens K.
 $21, Joern G.
$21, Joern G.
 $21, John H.
$21, John H.
 $21, Johnny S. 3rd aka “John Blaze”
$21, Johnny S. 3rd aka “John Blaze”
 $21, Jörg M.
$21, Jörg M.
 $21, Jose R. S. T.
$21, Jose R. S. T.
 $21, Julien K.
$21, Julien K.
 $21, Junchao Z.
$21, Junchao Z.
 $21, Jürgen F.
$21, Jürgen F.
 $21, Kari S.
$21, Kari S.
 $21, Kevin L aka “Kevin”
$21, Kevin L aka “Kevin”
 $21, LARS H. E.
$21, LARS H. E.
 $21, Lars R.
$21, Lars R.
 $21, Laszlo U.
$21, Laszlo U.
 $21, Leigh H.
$21, Leigh H.
 $21, Leopoldo S.
$21, Leopoldo S.
 $21, Luca O.
$21, Luca O.
 $21, Maik E.
$21, Maik E.
 $21, Manuel A.
$21, Manuel A.
 $21, Marc G.
$21, Marc G.
 $21, Marcel D.
$21, Marcel D.
 $21, Marcin Ś.
$21, Marcin Ś.
 $21, Marco F.
$21, Marco F.
 $21, Marco L.
$21, Marco L.
 $21, MARCO P.
$21, MARCO P.
 $21, Marco T.
$21, Marco T.
 $21, Marcus J.
$21, Marcus J.
 $21, Matthias D.
$21, Matthias D.
 $21, mauro P.
$21, mauro P.
 $21, MelanX
$21, MelanX
 $21, Mihai D. S.
$21, Mihai D. S.
 $21, Milan J.
$21, Milan J.
 $21, Mirko S.
$21, Mirko S.
 $21, Morten M. L.
$21, Morten M. L.
 $21, Mr A. W.
$21, Mr A. W.
 $21, NH-Trading
$21, NH-Trading
 $21, Nico D. G.
$21, Nico D. G.
 $21, pedro T.
$21, pedro T.
 $21, Peter D.
$21, Peter D.
 $21, Peter F.
$21, Peter F.
 $21, Peter T. N.
$21, Peter T. N.
 $21, philippe G.
$21, philippe G.
 $21, Piermarcello P.
$21, Piermarcello P.
 $21, Pierre H.
$21, Pierre H.
 $21, Privato
$21, Privato
 $21, Raúl S. T. aka “UlturCat”
$21, Raúl S. T. aka “UlturCat”
 $21, Renato D. P.
$21, Renato D. P.
 $21, robert B.
$21, robert B.
 $21, Rolf K.
$21, Rolf K.
 $21, Sebastian J.
$21, Sebastian J.
 $21, Sebastian S.
$21, Sebastian S.
 $21, Simon H.
$21, Simon H.
 $21, Simon L.
$21, Simon L.
 $21, SLOWorks Ky
$21, SLOWorks Ky
 $21, Sorin S.
$21, Sorin S.
 $21, Stefan H.
$21, Stefan H.
 $21, Stephan B.
$21, Stephan B.
 $21, Thibaut C.
$21, Thibaut C.
 $21, Thomas A.
$21, Thomas A.
 $21, Thomas P.
$21, Thomas P.
 $21, Thomas T.
$21, Thomas T.
 $21, Thomas V.
$21, Thomas V.
 $21, Tim B.
$21, Tim B.
 $21, Timo S.
$21, Timo S.
 $21, Tiziano C.
$21, Tiziano C.
 $21, Tobias K.
$21, Tobias K.
 $21, Tomos C.
$21, Tomos C.
 $21, Uwe F.
$21, Uwe F.
 $20 (74th donation), Bryan F.
$20 (74th donation), Bryan F.
 $20 (50th donation), John D.
$20 (50th donation), John D.
 $20 (35th donation), vagrantcow
$20 (35th donation), vagrantcow
 $20 (34th donation), Hemant Patel
$20 (34th donation), Hemant Patel
 $20 (30th donation), Aimee W.
$20 (30th donation), Aimee W.
 $20 (26th donation), Nigel B.
$20 (26th donation), Nigel B.
 $20 (21st donation), Arvis Lācis aka “arvislacis“
$20 (21st donation), Arvis Lācis aka “arvislacis“
 $20 (16th donation), Fred B.
$20 (16th donation), Fred B.
 $20 (9th donation), Dean P @ DT
$20 (9th donation), Dean P @ DT
 $20 (8th donation), Bezantnet, L.
$20 (8th donation), Bezantnet, L.
 $20 (8th donation), Colin S.
$20 (8th donation), Colin S.
 $20 (7th donation), Cuauhtemoc M.
$20 (7th donation), Cuauhtemoc M.
 $20 (7th donation), Daniel Greg aka “006.5”
$20 (7th donation), Daniel Greg aka “006.5”
 $20 (7th donation), Dismas S. aka “Dismas”
$20 (7th donation), Dismas S. aka “Dismas”
 $20 (7th donation), Eric H.
$20 (7th donation), Eric H.
 $20 (7th donation), Jerry L.
$20 (7th donation), Jerry L.
 $20 (7th donation), Leela A.
$20 (7th donation), Leela A.
 $20 (6th donation), Michael P.
$20 (6th donation), Michael P.
 $20 (6th donation), Randall W.
$20 (6th donation), Randall W.
 $20 (6th donation), Richard W.
$20 (6th donation), Richard W.
 $20 (5th donation), Ian M.
$20 (5th donation), Ian M.
 $20 (5th donation), Michael B.
$20 (5th donation), Michael B.
 $20 (5th donation), Patrick H.
$20 (5th donation), Patrick H.
 $20 (5th donation), Steve K.
$20 (5th donation), Steve K.
 $20 (5th donation), Yoichi N.
$20 (5th donation), Yoichi N.
 $20 (4th donation), Andrew P.
$20 (4th donation), Andrew P.
 $20 (4th donation), Bede W.
$20 (4th donation), Bede W.
 $20 (4th donation), Jutta S.
$20 (4th donation), Jutta S.
 $20 (4th donation), Raymond R.
$20 (4th donation), Raymond R.
 $20 (4th donation), Rent A Handyman aka “Cardoso”
$20 (4th donation), Rent A Handyman aka “Cardoso”
 $20 (4th donation), Roger S.
$20 (4th donation), Roger S.
 $20 (3rd donation), Brian W.
$20 (3rd donation), Brian W.
 $20 (3rd donation), Christopher F.
$20 (3rd donation), Christopher F.
 $20 (3rd donation), Esteemed Ape
$20 (3rd donation), Esteemed Ape
 $20 (3rd donation), GB
$20 (3rd donation), GB
 $20 (3rd donation), Gordon W.
$20 (3rd donation), Gordon W.
 $20 (3rd donation), Ian K.
$20 (3rd donation), Ian K.
 $20 (3rd donation), John W. G.
$20 (3rd donation), John W. G.
 $20 (3rd donation), Robert H.
$20 (3rd donation), Robert H.
 $20 (3rd donation), Samuel F.
$20 (3rd donation), Samuel F.
 $20 (3rd donation), Stephen W.
$20 (3rd donation), Stephen W.
 $20 (3rd donation), Veronique K.
$20 (3rd donation), Veronique K.
 $20 (3rd donation), Zsolnay I.
$20 (3rd donation), Zsolnay I.
 $20 (2nd donation), Aloysius R.
$20 (2nd donation), Aloysius R.
 $20 (2nd donation), Anonymous
$20 (2nd donation), Anonymous
 $20 (2nd donation), anonymous
$20 (2nd donation), anonymous
 $20 (2nd donation), Brandon H.
$20 (2nd donation), Brandon H.
 $20 (2nd donation), Brian H.
$20 (2nd donation), Brian H.
 $20 (2nd donation), Bryan C.
$20 (2nd donation), Bryan C.
 $20 (2nd donation), Clement D.
$20 (2nd donation), Clement D.
 $20 (2nd donation), D L.
$20 (2nd donation), D L.
 $20 (2nd donation), Dirk S.
$20 (2nd donation), Dirk S.
 $20 (2nd donation), Gaurav R.
$20 (2nd donation), Gaurav R.
 $20 (2nd donation), George Quentin aka “QuintinP”
$20 (2nd donation), George Quentin aka “QuintinP”
 $20 (2nd donation), Harry B.
$20 (2nd donation), Harry B.
 $20 (2nd donation), Jill M.
$20 (2nd donation), Jill M.
 $20 (2nd donation), Jon M.
$20 (2nd donation), Jon M.
 $20 (2nd donation), Leonhard R.
$20 (2nd donation), Leonhard R.
 $20 (2nd donation), Luther P.
$20 (2nd donation), Luther P.
 $20 (2nd donation), Manuel D. S.
$20 (2nd donation), Manuel D. S.
 $20 (2nd donation), Mitchel H.
$20 (2nd donation), Mitchel H.
 $20 (2nd donation), Oleksandr N.
$20 (2nd donation), Oleksandr N.
 $20 (2nd donation), Orlando O.
$20 (2nd donation), Orlando O.
 $20 (2nd donation), Randall J.
$20 (2nd donation), Randall J.
 $20 (2nd donation), Robert F.
$20 (2nd donation), Robert F.
 $20 (2nd donation), William I.
$20 (2nd donation), William I.
 $20, Andreas M.
$20, Andreas M.
 $20, Ashton B.
$20, Ashton B.
 $20, B and D Carpet Cleaners
$20, B and D Carpet Cleaners
 $20, BenFragged
$20, BenFragged
 $20, Bjoern L.
$20, Bjoern L.
 $20, Brian L. S.
$20, Brian L. S.
 $20, Brian M.
$20, Brian M.
 $20, Bruno G.
$20, Bruno G.
 $20, Capture Light
$20, Capture Light
 $20, Carrie B.
$20, Carrie B.
 $20, Charles E. P. J.
$20, Charles E. P. J.
 $20, colin C.
$20, colin C.
 $20, Daniel R.
$20, Daniel R.
 $20, Dario N. D.
$20, Dario N. D.
 $20, David G.
$20, David G.
 $20, edward B.
$20, edward B.
 $20, Eric K.
$20, Eric K.
 $20, FEDERICO S.
$20, FEDERICO S.
 $20, Harold W.
$20, Harold W.
 $20, Harvey M.
$20, Harvey M.
 $20, Hugh S.
$20, Hugh S.
 $20, Isaac R.
$20, Isaac R.
 $20, James B.
$20, James B.
 $20, James B.
$20, James B.
 $20, James V.
$20, James V.
 $20, James W.
$20, James W.
 $20, Janusz K.
$20, Janusz K.
 $20, Jerome K.
$20, Jerome K.
 $20, John K.
$20, John K.
 $20, John L aka “wakkoism”
$20, John L aka “wakkoism”
 $20, Jonathan H.
$20, Jonathan H.
 $20, Jordi-TEC
$20, Jordi-TEC
 $20, Joseph P.
$20, Joseph P.
 $20, Joseph V.
$20, Joseph V.
 $20, Joshua L.
$20, Joshua L.
 $20, Justin J.
$20, Justin J.
 $20, Keith C.
$20, Keith C.
 $20, Kenneth B.
$20, Kenneth B.
 $20, larry T.
$20, larry T.
 $20, Louis D.
$20, Louis D.
 $20, Louis J.
$20, Louis J.
 $20, M K
$20, M K
 $20, Marie L.
$20, Marie L.
 $20, Mario T.
$20, Mario T.
 $20, Michael M.
$20, Michael M.
 $20, Mikel N.
$20, Mikel N.
 $20, mohammed T.
$20, mohammed T.
 $20, Mr G. T.
$20, Mr G. T.
 $20, nick C.
$20, nick C.
 $20, Paul D.
$20, Paul D.
 $20, PREM S.
$20, PREM S.
 $20, ran B. L.
$20, ran B. L.
 $20, Rob C.
$20, Rob C.
 $20, Robert B.
$20, Robert B.
 $20, Robert L. H. J.
$20, Robert L. H. J.
 $20, Robert R.
$20, Robert R.
 $20, Srinivasa K.
$20, Srinivasa K.
 $20, Stephen M.
$20, Stephen M.
 $20, Steve H.
$20, Steve H.
 $20, Ted M.
$20, Ted M.
 $20, Thomas D.
$20, Thomas D.
 $20, TOMMY B.
$20, TOMMY B.
 $20, Trevor S.
$20, Trevor S.
 $20, Tyson V.
$20, Tyson V.
 $20, Vincent A.
$20, Vincent A.
 $20, |I|I|I|I|I|I|
$20, |I|I|I|I|I|I|
 $19 (3rd donation), Terry R.
$19 (3rd donation), Terry R.
 $18, Li Y.
$18, Li Y.
 $16 (4th donation), Abihail N.
$16 (4th donation), Abihail N.
 $15 (113rd donation), Johann J.
$15 (113rd donation), Johann J.
 $15 (8th donation), Marcin A.
$15 (8th donation), Marcin A.
 $15 (7th donation), Elias B.
$15 (7th donation), Elias B.
 $15 (7th donation), mitch K.
$15 (7th donation), mitch K.
 $15 (6th donation), Gorazd B.
$15 (6th donation), Gorazd B.
 $15 (6th donation), Luke B.
$15 (6th donation), Luke B.
 $15 (5th donation), Philippe F.
$15 (5th donation), Philippe F.
 $15 (4th donation), Christoph D.
$15 (4th donation), Christoph D.
 $15 (3rd donation), Agustín P.
$15 (3rd donation), Agustín P.
 $15 (3rd donation), Vlad I.
$15 (3rd donation), Vlad I.
 $15 (3rd donation), zilfe
$15 (3rd donation), zilfe
 $15 (2nd donation), Duy N.
$15 (2nd donation), Duy N.
 $15 (2nd donation), Philipp H.
$15 (2nd donation), Philipp H.
 $15,
$15,
 $15, Aaron D.
$15, Aaron D.
 $15, Anantha P.
$15, Anantha P.
 $15, Andreas K.
$15, Andreas K.
 $15, Antoine D.
$15, Antoine D.
 $15, Benoit R.
$15, Benoit R.
 $15, Carsten L.
$15, Carsten L.
 $15, Donald C.
$15, Donald C.
 $15, Erik S.
$15, Erik S.
 $15, JOHN F.
$15, JOHN F.
 $15, Loufute
$15, Loufute
 $15, Mark H.
$15, Mark H.
 $15, Maxime C.
$15, Maxime C.
 $15, Olaf S.
$15, Olaf S.
 $15, Pero P.
$15, Pero P.
 $15, PETR C.
$15, PETR C.
 $15, Philippe D.
$15, Philippe D.
 $15, Rui C.
$15, Rui C.
 $15, Thomas T.
$15, Thomas T.
 $14 (6th donation), Laszlo F.
$14 (6th donation), Laszlo F.
 $14 (2nd donation), Daniël P. aka “Frutiger Aero MATE”
$14 (2nd donation), Daniël P. aka “Frutiger Aero MATE”
 $14 (2nd donation), Pierre F.
$14 (2nd donation), Pierre F.
 $14, Bill M.
$14, Bill M.
 $13 (5th donation), Denis A. W.
$13 (5th donation), Denis A. W.
 $13,
$13, 
 $13, Andrew A.
$13, Andrew A.
 $12 (41st donation), Sami Mannila
$12 (41st donation), Sami Mannila
 $12 (10th donation), Theofanis-Emmanouil T.
$12 (10th donation), Theofanis-Emmanouil T.
 $12 (4th donation), Steven H.
$12 (4th donation), Steven H.
 $12 (2nd donation), David B.
$12 (2nd donation), David B.
 $12, Andreas H.
$12, Andreas H.
 $12, Jon G.
$12, Jon G.
 $12, OKAN D.
$12, OKAN D.
 $12, Ronald B.
$12, Ronald B.
 $11 (3rd donation), Shane B.
$11 (3rd donation), Shane B.
 $11 (2nd donation), Raymond M. (retired)
$11 (2nd donation), Raymond M. (retired)
 $11 (2nd donation), Rooter
$11 (2nd donation), Rooter
 $11, Alain G.
$11, Alain G.
 $11, Kris_8 aka “Kristian J.“
$11, Kris_8 aka “Kristian J.“
 $11, Nicola F.
$11, Nicola F.
 $10 (117th donation), Thomas C.
$10 (117th donation), Thomas C.
 $10 (44th donation), Tugaleres.com
$10 (44th donation), Tugaleres.com
 $10 (41st donation), Denys G. aka “GD Next“
$10 (41st donation), Denys G. aka “GD Next“
 $10 (22nd donation), Adian K.
$10 (22nd donation), Adian K.
 $10 (19th donation), José G. aka “picaso”
$10 (19th donation), José G. aka “picaso”
 $10 (17th donation), Ronald S.
$10 (17th donation), Ronald S.
 $10 (14th donation), Attila T.
$10 (14th donation), Attila T.
 $10 (14th donation), Dimitar S.
$10 (14th donation), Dimitar S.
 $10 (14th donation), Michael P.
$10 (14th donation), Michael P.
 $10 (12th donation), Abe Z.
$10 (12th donation), Abe Z.
 $10 (11th donation), Artem Ignatyev aka “ZaZooBred”
$10 (11th donation), Artem Ignatyev aka “ZaZooBred”
 $10 (11th donation), Douglas W.
$10 (11th donation), Douglas W.
 $10 (10th donation), Ian C.
$10 (10th donation), Ian C.
 $10 (9th donation), Eric L.
$10 (9th donation), Eric L.
 $10 (9th donation), Guillaume O. aka “Gandalf81”
$10 (9th donation), Guillaume O. aka “Gandalf81”
 $10 (8th donation), K. T. .
$10 (8th donation), K. T. .
 $10 (8th donation), Christoph B.
$10 (8th donation), Christoph B.
 $10 (8th donation), Jerry G.
$10 (8th donation), Jerry G.
 $10 (8th donation), Mariusz B.
$10 (8th donation), Mariusz B.
 $10 (8th donation), Paolo C.
$10 (8th donation), Paolo C.
 $10 (7th donation), aka “Max”
$10 (7th donation), aka “Max”
 $10 (7th donation), Patryk H.
$10 (7th donation), Patryk H.
 $10 (7th donation), Sebastian S.
$10 (7th donation), Sebastian S.
 $10 (7th donation), Ulrich P.
$10 (7th donation), Ulrich P.
 $10 (7th donation), vacances scolaires
$10 (7th donation), vacances scolaires
 $10 (6th donation), Andreas Agoumis aka “IntCon”
$10 (6th donation), Andreas Agoumis aka “IntCon”
 $10 (6th donation), Franz Z.
$10 (6th donation), Franz Z.
 $10 (6th donation), Jan V.
$10 (6th donation), Jan V.
 $10 (6th donation), Kostas K. aka “ELeoZz”
$10 (6th donation), Kostas K. aka “ELeoZz”
 $10 (6th donation), Matthias H.
$10 (6th donation), Matthias H.
 $10 (6th donation), Michael T.
$10 (6th donation), Michael T.
 $10 (6th donation), Sergei Petrov
$10 (6th donation), Sergei Petrov
 $10 (6th donation), Stefan V. B. aka “stefanvb”
$10 (6th donation), Stefan V. B. aka “stefanvb”
 $10 (6th donation), Tristan V.
$10 (6th donation), Tristan V.
 $10 (5th donation), Davide M.
$10 (5th donation), Davide M.
 $10 (5th donation), Digvijay C.
$10 (5th donation), Digvijay C.
 $10 (5th donation), Elmar V.
$10 (5th donation), Elmar V.
 $10 (5th donation), Iker L.
$10 (5th donation), Iker L.
 $10 (5th donation), Jean-francois L.
$10 (5th donation), Jean-francois L.
 $10 (5th donation), Kiril P.
$10 (5th donation), Kiril P.
 $10 (5th donation), Mario M. aka “xvs03”
$10 (5th donation), Mario M. aka “xvs03”
 $10 (5th donation), T.H.
$10 (5th donation), T.H.
 $10 (5th donation), Trygve S.
$10 (5th donation), Trygve S.
 $10 (4th donation), Alexander B.
$10 (4th donation), Alexander B.
 $10 (4th donation), Andreas Z.
$10 (4th donation), Andreas Z.
 $10 (4th donation), David P.
$10 (4th donation), David P.
 $10 (4th donation), Emmanuel T.
$10 (4th donation), Emmanuel T.
 $10 (4th donation), Henry B.
$10 (4th donation), Henry B.
 $10 (4th donation), James P.
$10 (4th donation), James P.
 $10 (4th donation), Jivko R.
$10 (4th donation), Jivko R.
 $10 (4th donation), Korora Solutions
$10 (4th donation), Korora Solutions
 $10 (4th donation), Lars K. aka “laku3008”
$10 (4th donation), Lars K. aka “laku3008”
 $10 (4th donation), Marijn V.
$10 (4th donation), Marijn V.
 $10 (4th donation), Marko U.
$10 (4th donation), Marko U.
 $10 (4th donation), Michael W.
$10 (4th donation), Michael W.
 $10 (4th donation), Natanael Cruz
$10 (4th donation), Natanael Cruz
 $10 (4th donation), Noriaki M.
$10 (4th donation), Noriaki M.
 $10 (4th donation), Pedro Antonio U.
$10 (4th donation), Pedro Antonio U.
 $10 (4th donation), Roland H.
$10 (4th donation), Roland H.
 $10 (4th donation), Stefan E.
$10 (4th donation), Stefan E.
 $10 (4th donation), Ted H.
$10 (4th donation), Ted H.
 $10 (3rd donation), Alba P. R.
$10 (3rd donation), Alba P. R.
 $10 (3rd donation), Albin L.
$10 (3rd donation), Albin L.
 $10 (3rd donation), Alex
$10 (3rd donation), Alex
 $10 (3rd donation), Alvaro D. A.
$10 (3rd donation), Alvaro D. A.
 $10 (3rd donation), Carlos V M.
$10 (3rd donation), Carlos V M.
 $10 (3rd donation), Chris D.
$10 (3rd donation), Chris D.
 $10 (3rd donation), Daniel P.
$10 (3rd donation), Daniel P.
 $10 (3rd donation), Elia P.
$10 (3rd donation), Elia P.
 $10 (3rd donation), Ernest J.
$10 (3rd donation), Ernest J.
 $10 (3rd donation), Gerhard K.
$10 (3rd donation), Gerhard K.
 $10 (3rd donation), Gerold H.
$10 (3rd donation), Gerold H.
 $10 (3rd donation), Giuseppe Francesco Aldo R.
$10 (3rd donation), Giuseppe Francesco Aldo R.
 $10 (3rd donation), K. M.
$10 (3rd donation), K. M.
 $10 (3rd donation), Lowell T.
$10 (3rd donation), Lowell T.
 $10 (3rd donation), Marcelo A. Maito
$10 (3rd donation), Marcelo A. Maito
 $10 (3rd donation), Markus Z.
$10 (3rd donation), Markus Z.
 $10 (3rd donation), Michael F.
$10 (3rd donation), Michael F.
 $10 (3rd donation), Michael O.
$10 (3rd donation), Michael O.
 $10 (3rd donation), Michael V.
$10 (3rd donation), Michael V.
 $10 (3rd donation), Pablo J. E.
$10 (3rd donation), Pablo J. E.
 $10 (3rd donation), Philip B.
$10 (3rd donation), Philip B.
 $10 (3rd donation), Rainer B.
$10 (3rd donation), Rainer B.
 $10 (3rd donation), Raphael C.
$10 (3rd donation), Raphael C.
 $10 (3rd donation), Renaud A.
$10 (3rd donation), Renaud A.
 $10 (3rd donation), Rolf S.
$10 (3rd donation), Rolf S.
 $10 (3rd donation), ronald H.
$10 (3rd donation), ronald H.
 $10 (3rd donation), Stonewall C.
$10 (3rd donation), Stonewall C.
 $10 (3rd donation), Urszula S.
$10 (3rd donation), Urszula S.
 $10 (2nd donation), 6AM Films
$10 (2nd donation), 6AM Films
 $10 (2nd donation), André M.
$10 (2nd donation), André M.
 $10 (2nd donation), Andreas T.
$10 (2nd donation), Andreas T.
 $10 (2nd donation), Andrii
$10 (2nd donation), Andrii
 $10 (2nd donation), Anton V.
$10 (2nd donation), Anton V.
 $10 (2nd donation), Christian M.
$10 (2nd donation), Christian M.
 $10 (2nd donation), Claude M.
$10 (2nd donation), Claude M.
 $10 (2nd donation), Csrl Richard S.
$10 (2nd donation), Csrl Richard S.
 $10 (2nd donation), Dane P.
$10 (2nd donation), Dane P.
 $10 (2nd donation), Daniel A.
$10 (2nd donation), Daniel A.
 $10 (2nd donation), David K.
$10 (2nd donation), David K.
 $10 (2nd donation), David K.
$10 (2nd donation), David K.
 $10 (2nd donation), Denis G.
$10 (2nd donation), Denis G.
 $10 (2nd donation), Gianluigi D.
$10 (2nd donation), Gianluigi D.
 $10 (2nd donation), Gordon O.
$10 (2nd donation), Gordon O.
 $10 (2nd donation), Ian T.
$10 (2nd donation), Ian T.
 $10 (2nd donation), Ines G.
$10 (2nd donation), Ines G.
 $10 (2nd donation), Ismail K.
$10 (2nd donation), Ismail K.
 $10 (2nd donation), Jambalak
$10 (2nd donation), Jambalak
 $10 (2nd donation), Joel R.
$10 (2nd donation), Joel R.
 $10 (2nd donation), John Howard Jones
$10 (2nd donation), John Howard Jones
 $10 (2nd donation), Kai S.
$10 (2nd donation), Kai S.
 $10 (2nd donation), Klaus B.
$10 (2nd donation), Klaus B.
 $10 (2nd donation), László B. aka “Lighthunter“
$10 (2nd donation), László B. aka “Lighthunter“
 $10 (2nd donation), LEVENTE V.
$10 (2nd donation), LEVENTE V.
 $10 (2nd donation), Magnus P.
$10 (2nd donation), Magnus P.
 $10 (2nd donation), Maris K.
$10 (2nd donation), Maris K.
 $10 (2nd donation), Maroš Ď.
$10 (2nd donation), Maroš Ď.
 $10 (2nd donation), Michael E.
$10 (2nd donation), Michael E.
 $10 (2nd donation), Michael W.
$10 (2nd donation), Michael W.
 $10 (2nd donation), Mike G.
$10 (2nd donation), Mike G.
 $10 (2nd donation), Mois C.
$10 (2nd donation), Mois C.
 $10 (2nd donation), Monsieur F.
$10 (2nd donation), Monsieur F.
 $10 (2nd donation), Nevin M.
$10 (2nd donation), Nevin M.
 $10 (2nd donation), Paul A.
$10 (2nd donation), Paul A.
 $10 (2nd donation), Paweł
$10 (2nd donation), Paweł
 $10 (2nd donation), Raymond S.
$10 (2nd donation), Raymond S.
 $10 (2nd donation), Rodrigo S.
$10 (2nd donation), Rodrigo S.
 $10 (2nd donation), Simon P.
$10 (2nd donation), Simon P.
 $10 (2nd donation), Thomas H.
$10 (2nd donation), Thomas H.
 $10 (2nd donation), Thorsten K.
$10 (2nd donation), Thorsten K.
 $10 (2nd donation), Wolfgang Z.
$10 (2nd donation), Wolfgang Z.
 $10,
$10,
 $10, 8-BitPlus
$10, 8-BitPlus
 $10, Abdullah E.
$10, Abdullah E.
 $10, Afonso C.
$10, Afonso C.
 $10, Ahmed A.
$10, Ahmed A.
 $10, Alatalo I. O.
$10, Alatalo I. O.
 $10, Alexander S.
$10, Alexander S.
 $10, Anastasios V.
$10, Anastasios V.
 $10, Andre W.
$10, Andre W.
 $10, Andrea S.
$10, Andrea S.
 $10, Andreas K.
$10, Andreas K.
 $10, Andreas N.
$10, Andreas N.
 $10, Andries B.
$10, Andries B.
 $10, Aneta S.
$10, Aneta S.
 $10, Angelo T.
$10, Angelo T.
 $10, Arda L.
$10, Arda L.
 $10, ArVel.
$10, ArVel.
 $10, Austin G.
$10, Austin G.
 $10, Back 2 Homesteading Off Grid
$10, Back 2 Homesteading Off Grid
 $10, Barna K.
$10, Barna K.
 $10, Barry M.
$10, Barry M.
 $10, Bellal H.
$10, Bellal H.
 $10, Bruno L.
$10, Bruno L.
 $10, Carlos R. V.
$10, Carlos R. V.
 $10, chandler J.
$10, chandler J.
 $10, Christian H.
$10, Christian H.
 $10, Christoph S.
$10, Christoph S.
 $10, Clinton B.
$10, Clinton B.
 $10, Construction Aldo
$10, Construction Aldo
 $10, Daniel H.
$10, Daniel H.
 $10, Daniel M.
$10, Daniel M.
 $10, David D.
$10, David D.
 $10, Denzel A.
$10, Denzel A.
 $10, Derek D.
$10, Derek D.
 $10, Dmitry m_IDEX
$10, Dmitry m_IDEX
 $10, Dominik S.
$10, Dominik S.
 $10, Dorin H.
$10, Dorin H.
 $10, Fahad
$10, Fahad
 $10, Florian K.
$10, Florian K.
 $10, Franco R.
$10, Franco R.
 $10, Frode H.
$10, Frode H.
 $10, Gabriel G. S.
$10, Gabriel G. S.
 $10, Gabriel L. S.
$10, Gabriel L. S.
 $10, Gabriele U.
$10, Gabriele U.
 $10, Giancarlo N.
$10, Giancarlo N.
 $10, Giuseppe F. aka “Pepster”
$10, Giuseppe F. aka “Pepster”
 $10, Goran M.
$10, Goran M.
 $10, Greg Z.
$10, Greg Z.
 $10, Gregory H.
$10, Gregory H.
 $10, Grzegorz J.
$10, Grzegorz J.
 $10, Hans-Jochen H.
$10, Hans-Jochen H.
 $10, Hansjörg G.
$10, Hansjörg G.
 $10, Helio C.
$10, Helio C.
 $10, Henning L.
$10, Henning L.
 $10, Iain D.
$10, Iain D.
 $10, Istvan G.
$10, Istvan G.
 $10, iWINDs
$10, iWINDs
 $10, JACINTO L.
$10, JACINTO L.
 $10, Jeevaratnam A.
$10, Jeevaratnam A.
 $10, JIM C.
$10, JIM C.
 $10, Jimmy N. B.
$10, Jimmy N. B.
 $10, Joachim B.
$10, Joachim B.
 $10, Joachim T.
$10, Joachim T.
 $10, Joakim S.
$10, Joakim S.
 $10, Joel C. T.
$10, Joel C. T.
 $10, Johannes D.
$10, Johannes D.
 $10, John G.
$10, John G.
 $10, Jonas M.
$10, Jonas M.
 $10, Jörg S.
$10, Jörg S.
 $10, Joshua M.
$10, Joshua M.
 $10, Julian S.
$10, Julian S.
 $10, Jvan D.
$10, Jvan D.
 $10, Kaj J.
$10, Kaj J.
 $10, Karl H.
$10, Karl H.
 $10, KAZUO S.
$10, KAZUO S.
 $10, Kim Conter
$10, Kim Conter
 $10, Klaus W.
$10, Klaus W.
 $10, Laurent F.
$10, Laurent F.
 $10, Leopold M.
$10, Leopold M.
 $10, Lily S. aka “Kes”
$10, Lily S. aka “Kes”
 $10, Linux Mint User
$10, Linux Mint User
 $10, Lou F.
$10, Lou F.
 $10, Luis A. C. L. C.
$10, Luis A. C. L. C.
 $10, Luis O. B.
$10, Luis O. B.
 $10, M O. L.
$10, M O. L.
 $10, makeup
$10, makeup
 $10, Marc L.
$10, Marc L.
 $10, Marc L.
$10, Marc L.
 $10, marcus W.
$10, marcus W.
 $10, Mario B. M.
$10, Mario B. M.
 $10, mario.q59
$10, mario.q59
 $10, Markus K.
$10, Markus K.
 $10, Martin S.
$10, Martin S.
 $10, MASAYASU T.
$10, MASAYASU T.
 $10, Mastercard
$10, Mastercard
 $10, Mateusz S.
$10, Mateusz S.
 $10, Mathias P.
$10, Mathias P.
 $10, Matija P.
$10, Matija P.
 $10, MATTHEW L. F.
$10, MATTHEW L. F.
 $10, Màtto AD aka “T MaAD”
$10, Màtto AD aka “T MaAD”
 $10, mauri H.
$10, mauri H.
 $10, Mauro B.
$10, Mauro B.
 $10, Merry Christmas!
$10, Merry Christmas!
 $10, Michael C.
$10, Michael C.
 $10, Michael G.
$10, Michael G.
 $10, Miguel I. B. aka “Ameritron”
$10, Miguel I. B. aka “Ameritron”
 $10, Muhammad K.
$10, Muhammad K.
 $10, Myne
$10, Myne
 $10, narghilea
$10, narghilea
 $10, Nehva
$10, Nehva
 $10, Niko G.
$10, Niko G.
 $10, notar public
$10, notar public
 $10, Olaf K.
$10, Olaf K.
 $10, Oleksandr F.
$10, Oleksandr F.
 $10, Paolo G.
$10, Paolo G.
 $10, Pasquale C.
$10, Pasquale C.
 $10, Patryk N.
$10, Patryk N.
 $10, Paul G.
$10, Paul G.
 $10, Penny F.
$10, Penny F.
 $10, Petar C.
$10, Petar C.
 $10, Peter C.
$10, Peter C.
 $10, Peter H.
$10, Peter H.
 $10, Peter S.
$10, Peter S.
 $10, Philipp S.
$10, Philipp S.
 $10, R L.
$10, R L.
 $10, Radek M.
$10, Radek M.
 $10, Ralf G.
$10, Ralf G.
 $10, Raymond L. M.
$10, Raymond L. M.
 $10, Raymond N.
$10, Raymond N.
 $10, Reagan U.
$10, Reagan U.
 $10, Reinhard E.
$10, Reinhard E.
 $10, René H.
$10, René H.
 $10, RICCARDO B.
$10, RICCARDO B.
 $10, RitaMay56
$10, RitaMay56
 $10, Robert J.
$10, Robert J.
 $10, Roberto S.
$10, Roberto S.
 $10, Robin K.
$10, Robin K.
 $10, Roger S.
$10, Roger S.
 $10, Roman
$10, Roman
 $10, Samuel P.
$10, Samuel P.
 $10, Sandra W.
$10, Sandra W.
 $10, Santos M. C.
$10, Santos M. C.
 $10, Saurabh K.
$10, Saurabh K.
 $10, Sean T.
$10, Sean T.
 $10, Semih A.
$10, Semih A.
 $10, Shawn K.
$10, Shawn K.
 $10, Sönke S.
$10, Sönke S.
 $10, Stefan R.
$10, Stefan R.
 $10, Stefan S.
$10, Stefan S.
 $10, Stefano B.
$10, Stefano B.
 $10, Steve H.
$10, Steve H.
 $10, Steven S.
$10, Steven S.
 $10, stiri pozitive
$10, stiri pozitive
 $10, Timo V.
$10, Timo V.
 $10, Tobias Kahl
$10, Tobias Kahl
 $10, Todor T.
$10, Todor T.
 $10, Tomasz K.
$10, Tomasz K.
 $10, Tony F.
$10, Tony F.
 $10, Torsten H.
$10, Torsten H.
 $10, Travis G.
$10, Travis G.
 $10, Truong N.
$10, Truong N.
 $10, Valter B.
$10, Valter B.
 $10, Valter L.
$10, Valter L.
 $10, VJ
$10, VJ
 $10, Volkan G. aka “VgA”
$10, Volkan G. aka “VgA”
 $10, Volkhard Z.
$10, Volkhard Z.
 $10, willie R.
$10, willie R.
 $10, Wojciech J.
$10, Wojciech J.
 $10, X F.
$10, X F.
 $10, Youri S.
$10, Youri S.
 $9, Niccolò
$9, Niccolò
 $9, SILVESTER M.
$9, SILVESTER M.
 $9, Vojtěch S.
$9, Vojtěch S.
 $8 (4th donation), Ion Daniel G.
$8 (4th donation), Ion Daniel G.
 $8 (3rd donation), Lukasz M.
$8 (3rd donation), Lukasz M.
 $8, Jean-Luc V.
$8, Jean-Luc V.
 $7, a
$7, a
 $7, Athanasios F.
$7, Athanasios F.
 $7, Richard B.
$7, Richard B.
 $428 from 102 smaller donations
$428 from 102 smaller donations
If you want to help Linux Mint with a donation, please visit https://www.linuxmint.com/donors.php
Patrons:
Linux Mint is proudly supported by 2,017 patrons, for a sum of $4,900 per month.
To become a Linux Mint patron, please visit https://www.patreon.com/linux_mint
]]>
 When I first heard about the RISC-V Unified Database project, I was immediately drawn to its ambition: to become a single, machine-readable source of truth for the RISC-V Instruction Set Architecture (ISA). Once complete, the project would power a broad ecosystem of downstream tools such as assemblers, disassemblers, simulators, debuggers and more.
When I first heard about the RISC-V Unified Database project, I was immediately drawn to its ambition: to become a single, machine-readable source of truth for the RISC-V Instruction Set Architecture (ISA). Once complete, the project would power a broad ecosystem of downstream tools such as assemblers, disassemblers, simulators, debuggers and more.
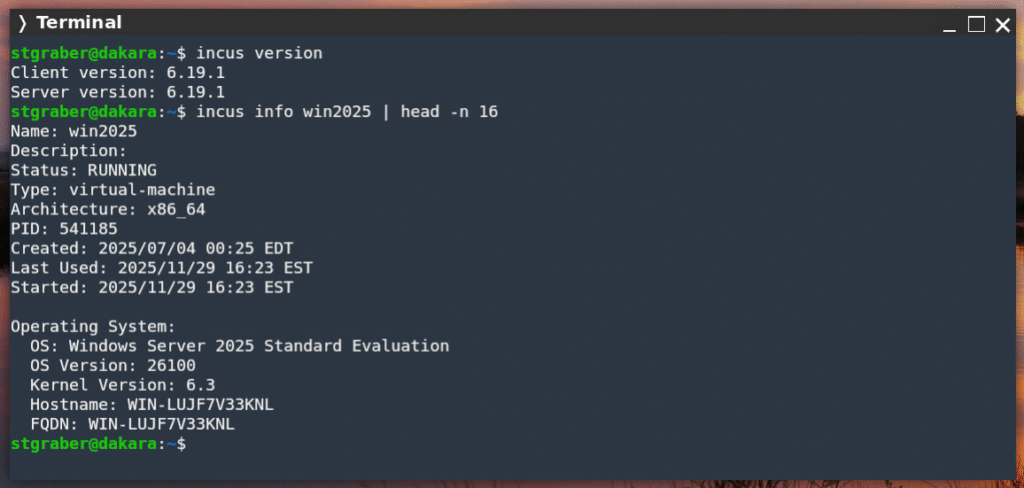
































 Linux doesn’t hide the system behind guardrails. Here’s why its freedom, flexibility, and control still outclass the mainstream desktop OSes. The post Linux: The Real Operating System appeared first on LinuxInsider.]]>
Linux doesn’t hide the system behind guardrails. Here’s why its freedom, flexibility, and control still outclass the mainstream desktop OSes. The post Linux: The Real Operating System appeared first on LinuxInsider.]]>
 Token Security’s open-source AI Privilege Guardian is designed to help CISOs right-size agent permissions and reduce machine-speed attack risk. The post Over-Privileged AI Agents Are the Next Enterprise Blind Spot appeared first on LinuxInsider.]]>
Token Security’s open-source AI Privilege Guardian is designed to help CISOs right-size agent permissions and reduce machine-speed attack risk. The post Over-Privileged AI Agents Are the Next Enterprise Blind Spot appeared first on LinuxInsider.]]>


 Two malware campaigns weaponize open-source software to target executives and cloud systems, combining social engineering with fileless and kernel-level attack techniques. The post Weaponized Python and Linux Malware Target Executives and Cloud Systems appeared first on LinuxInsider.]]>
Two malware campaigns weaponize open-source software to target executives and cloud systems, combining social engineering with fileless and kernel-level attack techniques. The post Weaponized Python and Linux Malware Target Executives and Cloud Systems appeared first on LinuxInsider.]]>


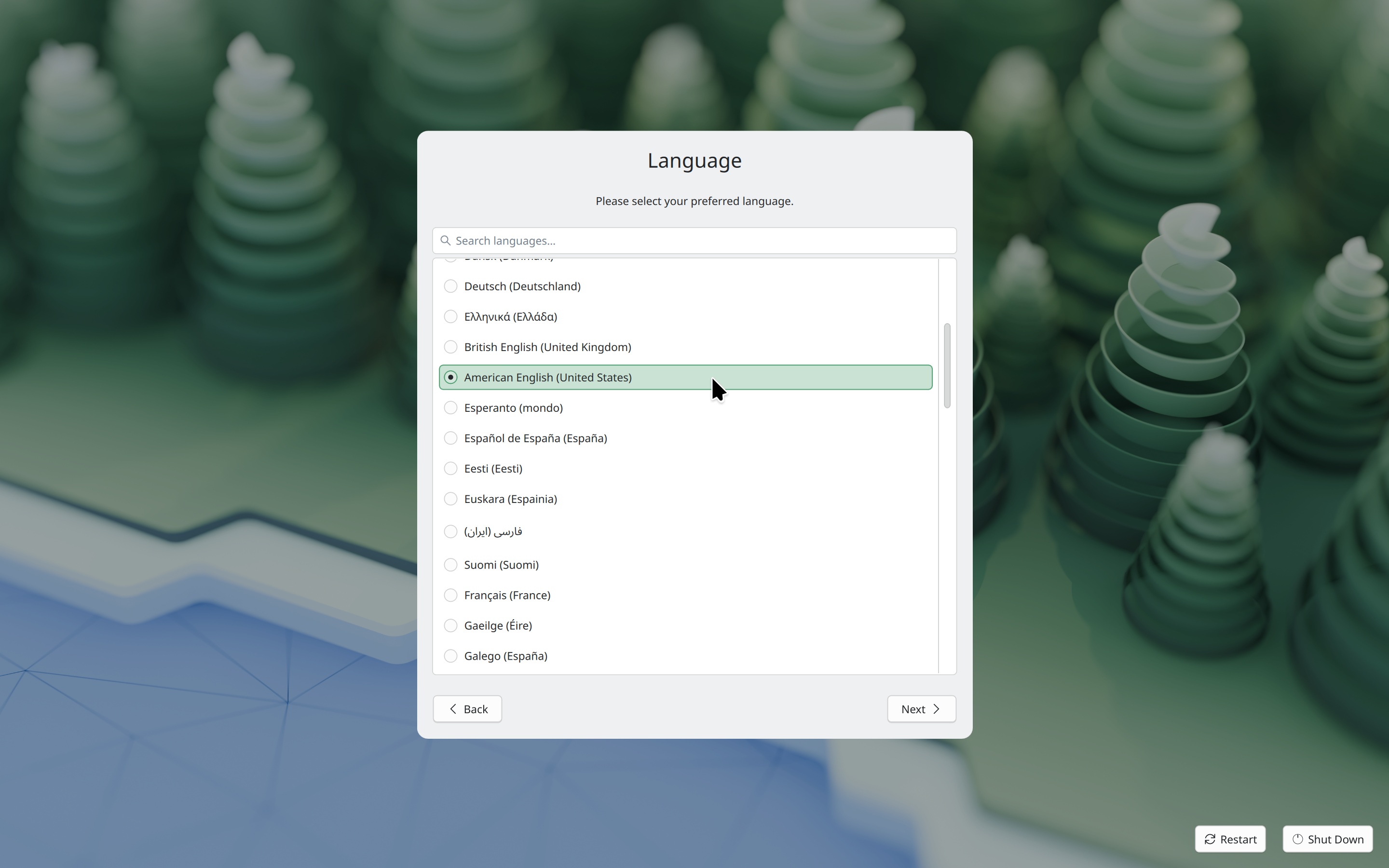
 This step-by-step guide shows Linux users how to secure cloud-stored files with VeraCrypt by encrypting data locally, keeping encryption keys out of cloud providers' hands. The post How to Secure Cloud Storage on Linux With VeraCrypt appeared first on LinuxInsider.]]>
This step-by-step guide shows Linux users how to secure cloud-stored files with VeraCrypt by encrypting data locally, keeping encryption keys out of cloud providers' hands. The post How to Secure Cloud Storage on Linux With VeraCrypt appeared first on LinuxInsider.]]>





















 I am happy to share that as of 10 February 2026, Fedora is now available in Syria. Last week, the Fedora Infrastructure Team
I am happy to share that as of 10 February 2026, Fedora is now available in Syria. Last week, the Fedora Infrastructure Team 









































































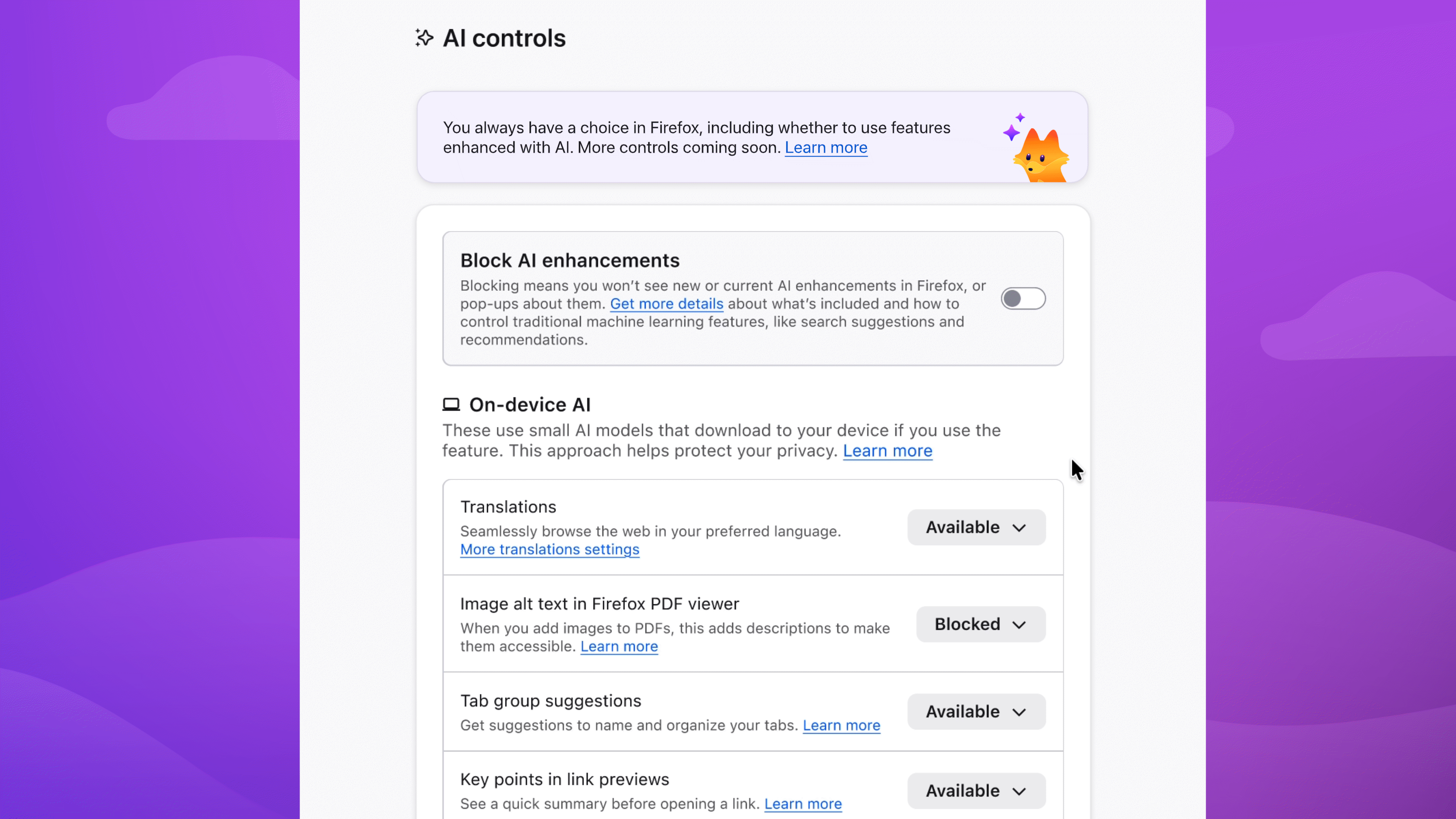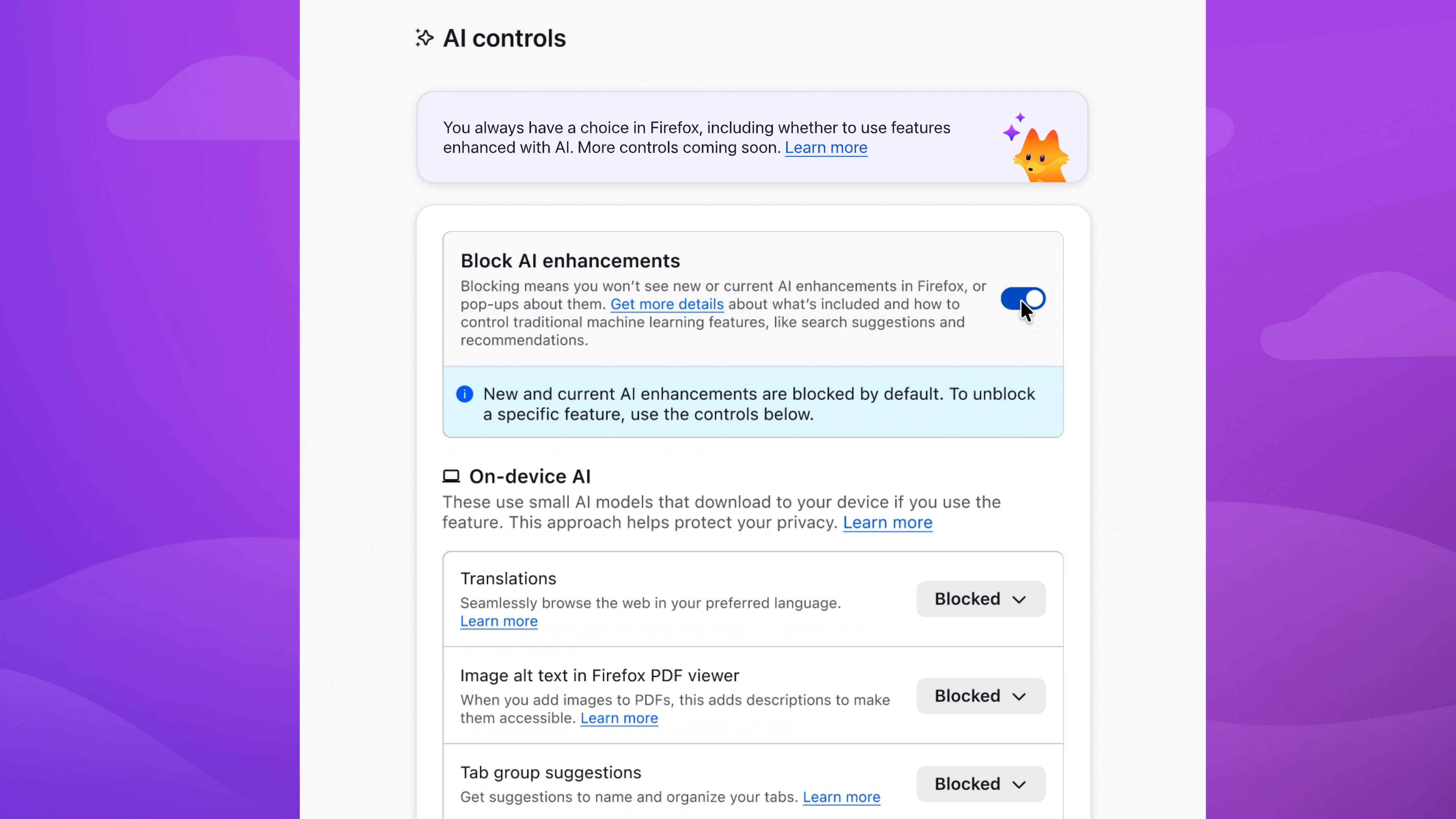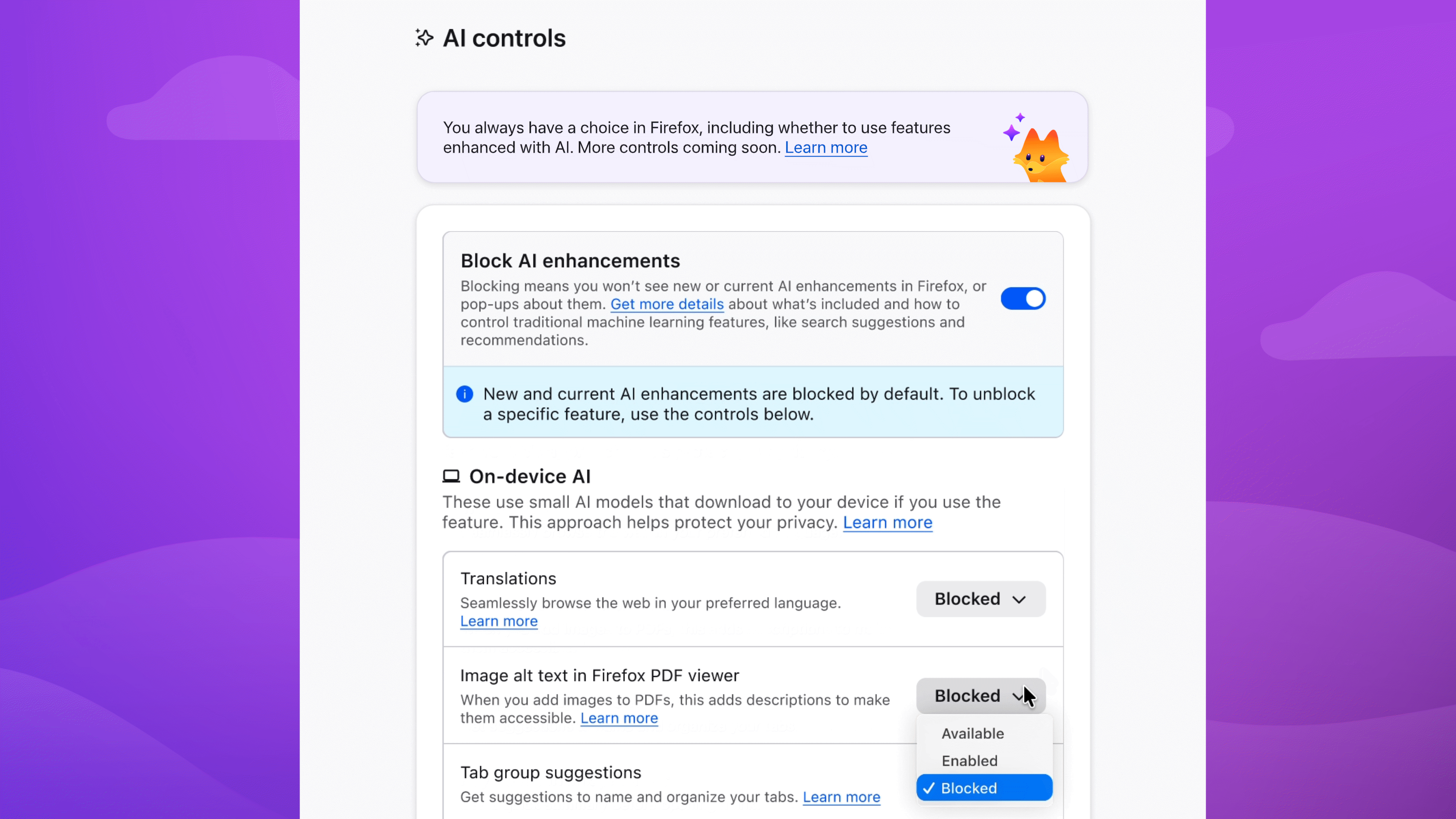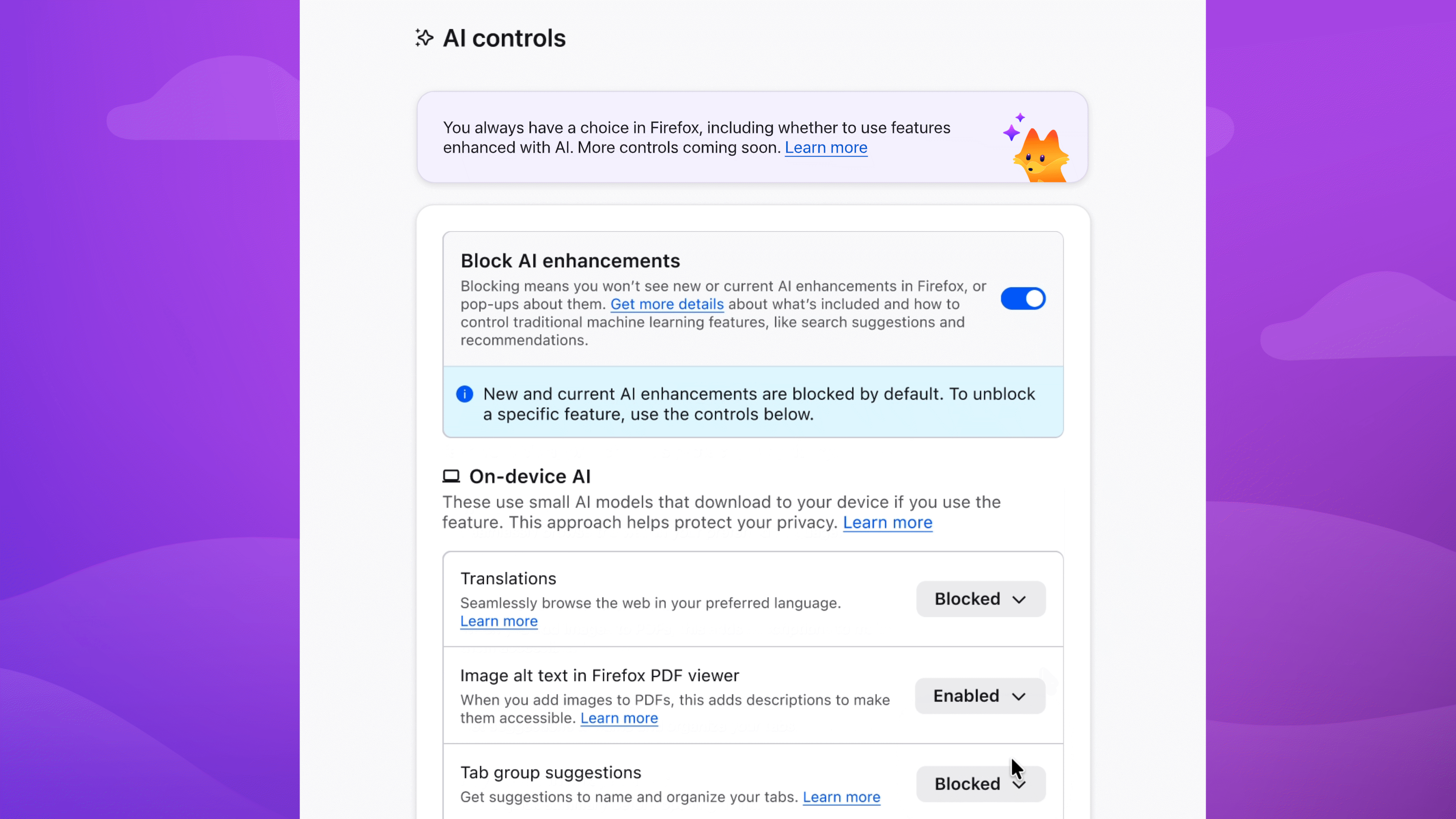
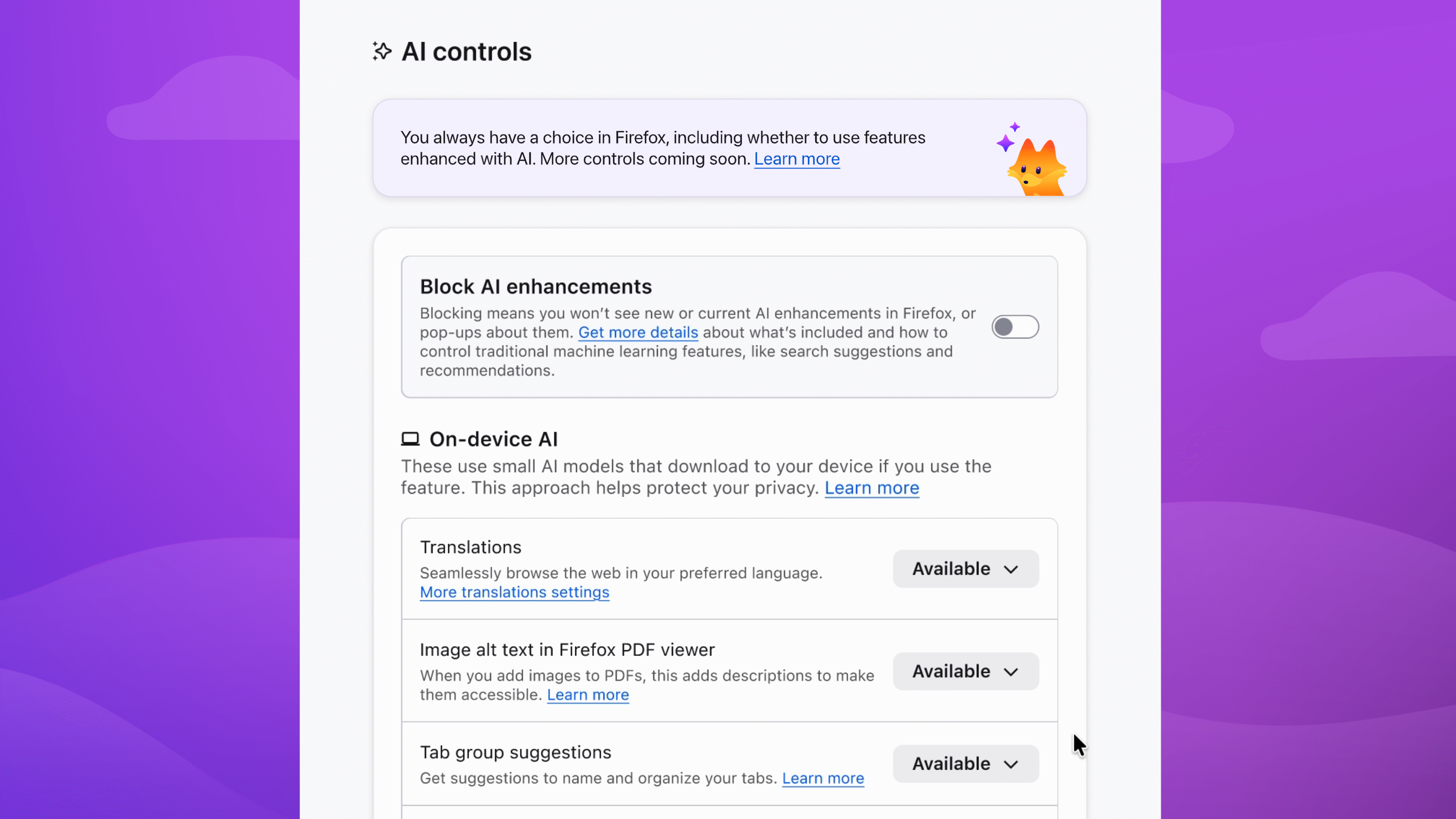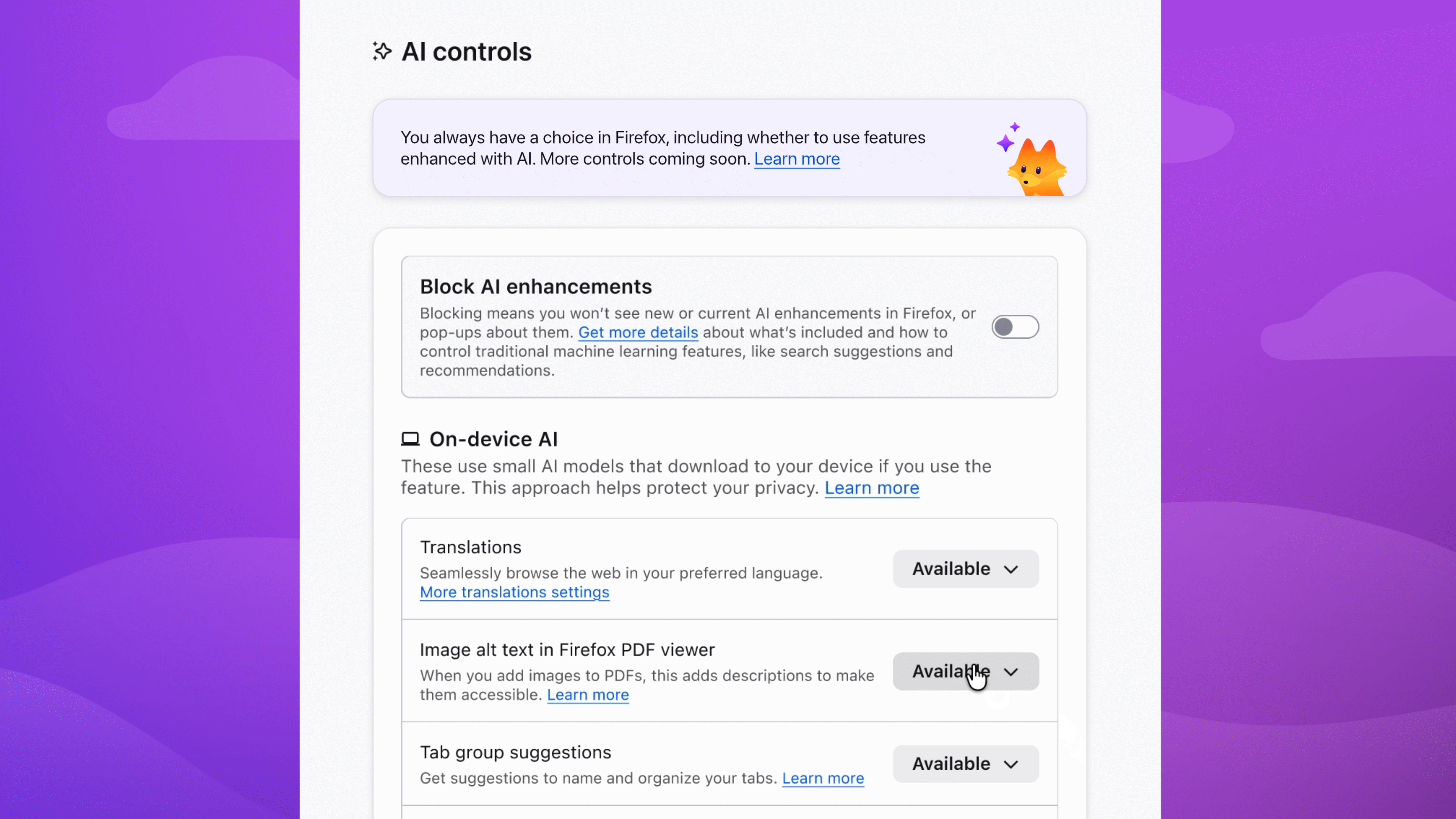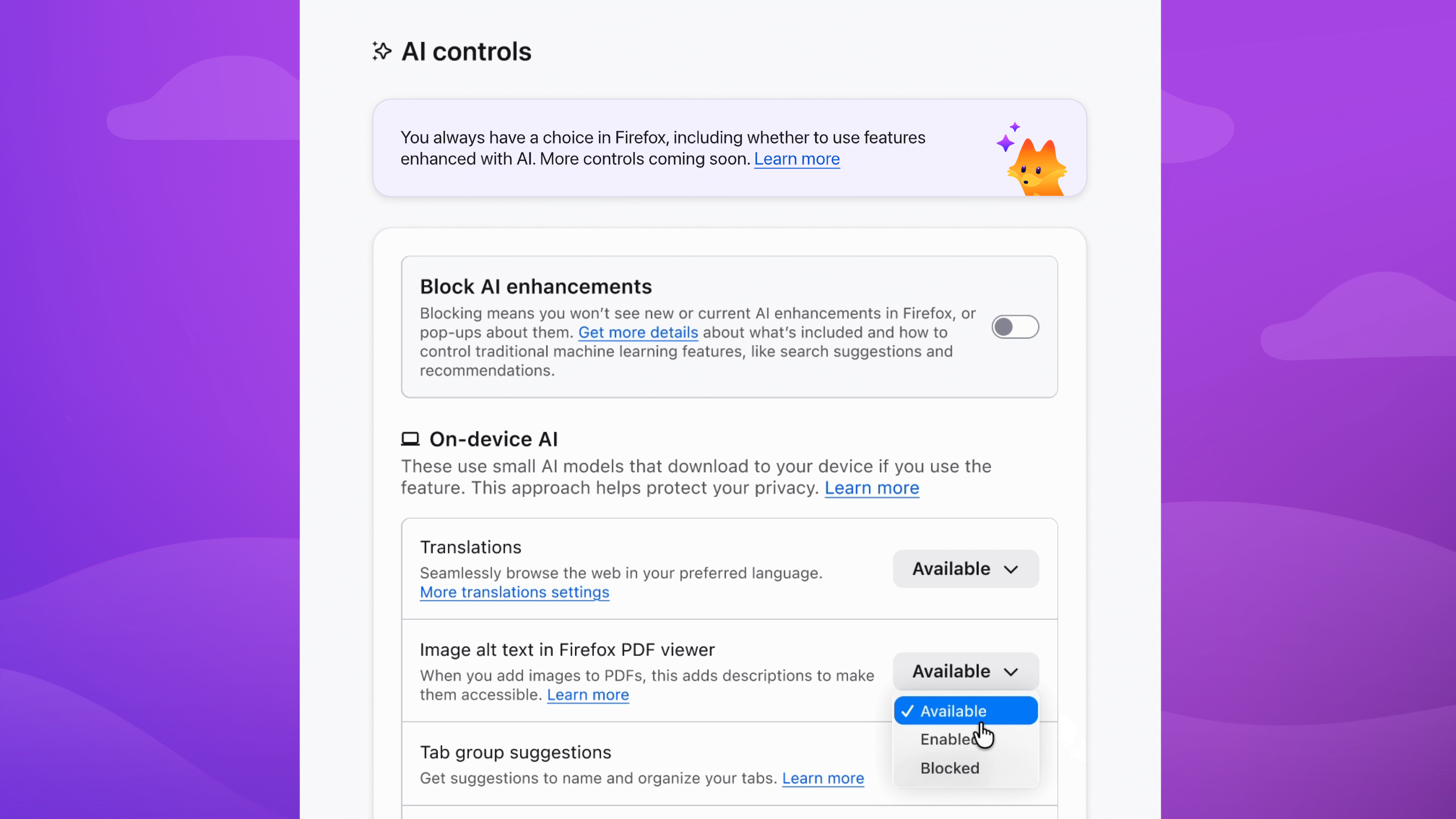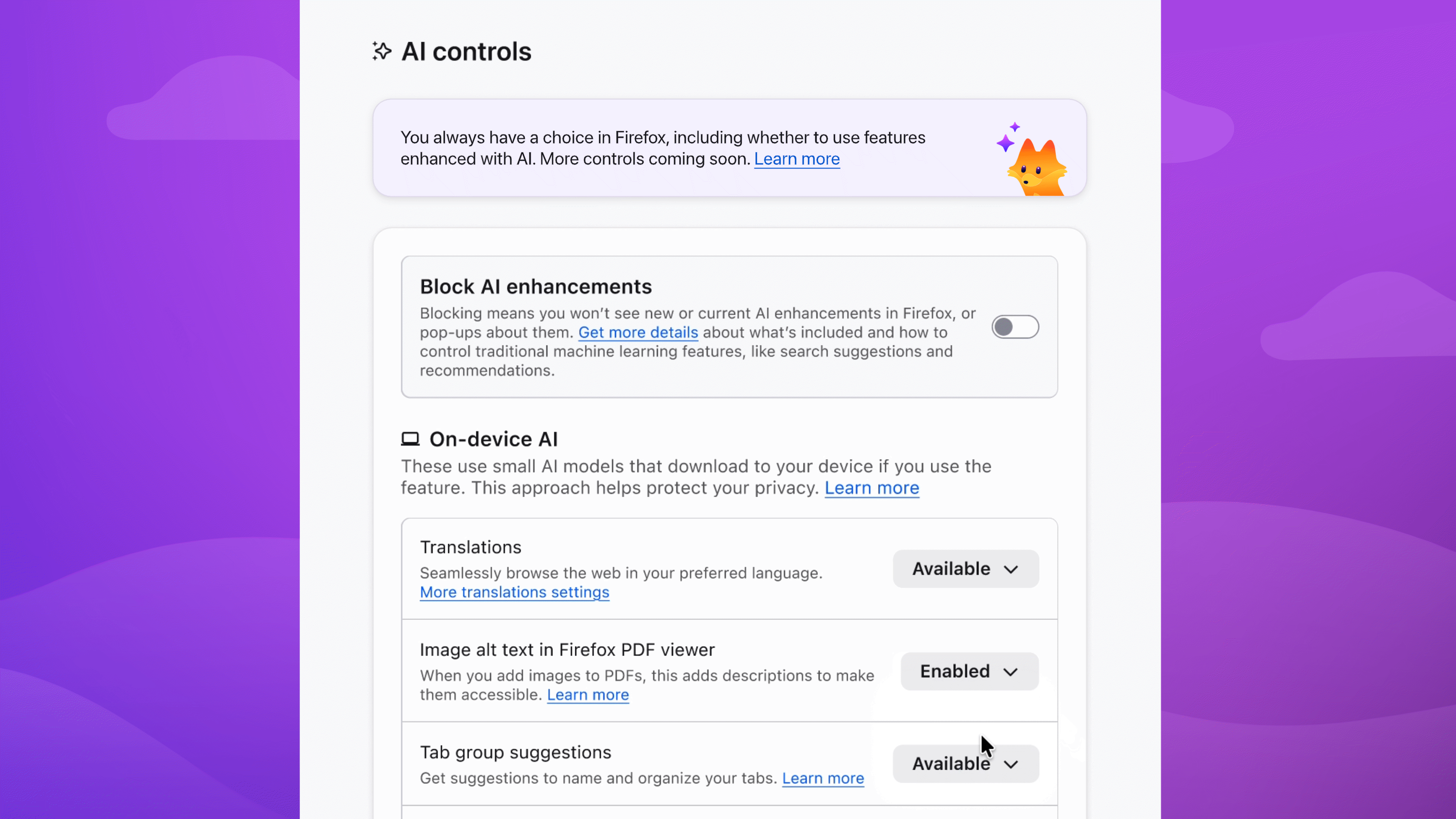





 As AI-assisted coding accelerates software development, security teams are facing a growing challenge managing expanding open-source dependencies and the vulnerabilities they introduce across enterprise environments. The post Open-Source Vulnerabilities Double as AI Coding Grows appeared first on LinuxInsider.]]>
As AI-assisted coding accelerates software development, security teams are facing a growing challenge managing expanding open-source dependencies and the vulnerabilities they introduce across enterprise environments. The post Open-Source Vulnerabilities Double as AI Coding Grows appeared first on LinuxInsider.]]>












 Tails 7.5, a privacy-focused Linux distro, upgrades Tor Browser to 15.0.7, updates the Tor client to 0.4.9.5, and improves Thunderbird security.]]>
Tails 7.5, a privacy-focused Linux distro, upgrades Tor Browser to 15.0.7, updates the Tor client to 0.4.9.5, and improves Thunderbird security.]]>
 Fwupd 2.0.20 introduces AMD UMA carveout configuration, fixes fastboot and USB issues, and adds support for new HP, Framework, and Jabra hardware.]]>
Fwupd 2.0.20 introduces AMD UMA carveout configuration, fixes fastboot and USB issues, and adds support for new HP, Framework, and Jabra hardware.]]>
 The Document Foundation releases LibreOffice 26.2.1, delivering extensive bug fixes and stability improvements for the 26.2 productivity suite.]]>
The Document Foundation releases LibreOffice 26.2.1, delivering extensive bug fixes and stability improvements for the 26.2 productivity suite.]]>
 ONLYOFFICE Docs 9.3 adds multipage document view, enhanced PDF signatures, and a new Solver tool for spreadsheets, alongside performance fixes and improvements.]]>
ONLYOFFICE Docs 9.3 adds multipage document view, enhanced PDF signatures, and a new Solver tool for spreadsheets, alongside performance fixes and improvements.]]>

 Arch-based Omarchy 3.4 introduces default Tmux integration, hibernation on new installs, refined Hyprland workflows, and multiple new desktop themes.]]>
Arch-based Omarchy 3.4 introduces default Tmux integration, hibernation on new installs, refined Hyprland workflows, and multiple new desktop themes.]]>
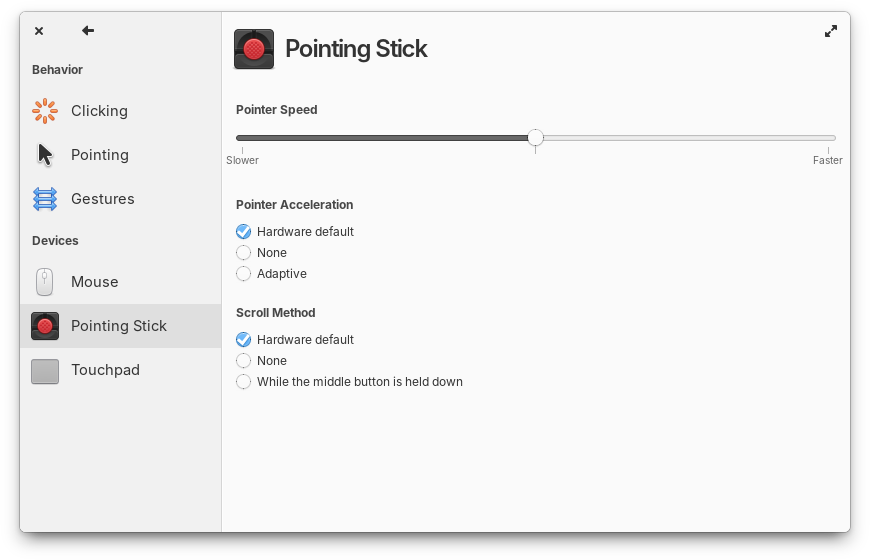





 Calibre 9.4 introduces reading progress stats in the e-book viewer, UI refinements, and DOCX and ODT fixes.]]>
Calibre 9.4 introduces reading progress stats in the e-book viewer, UI refinements, and DOCX and ODT fixes.]]>
 LXD 6.7 adds AMD GPU CDI support and enhances VM GPU passthrough with updated QEMU and EDK2 versions, improving virtualization performance.]]>
LXD 6.7 adds AMD GPU CDI support and enhances VM GPU passthrough with updated QEMU and EDK2 versions, improving virtualization performance.]]>