You might be excused for thinking that every tech company is out to get you, especially if you still use Windows, which we like to think of as “yesterday’s operating system.”
We’ll start with the poor Windows user.
News came out on Tuesday that since August Dell computers have been coming out-of-the-box with a root certificate preinstalled that is an “unintended security vulnerability.” The source of the quote, by the way, is Dell itself.
And you thought all you had to worry about was Superfish, the adware Lenovo installed on its computers that left users vulnerable to man-in the-middle attacks — even when running Linux. At least the latest dumb move by Dell seems to be Windows specific, meaning most readers of FOSS Force can breath easy and repeat the official Linux mantra rewritten from an old Dial soap campaign.
 Aren’t you glad you use Linux? Don’t you wish ever everybody did?
Aren’t you glad you use Linux? Don’t you wish ever everybody did?
This latest blunder by Dell revolves around eDellRoot, a self-signed certificate installed under the “Trusted Root Certification Authorities” in the Windows certificate store. With this in place, the Dell computer will trust any SSL/TLS or code-signing certificate that is signed using eDellRoot’s not-so-private key, which is publicly available online.
According to security expert Brian Krebs, this leaves users open to man-in-the-middle attacks: “A malicious hacker could exploit this flaw on open, public networks (think WiFi hotspots, coffee shops, airports) to impersonate any Web site to a Dell user, and to quietly intercept, read and modify all of a vulnerable Dell system’s Web traffic.”
In this case, “any website” might mean, say, a user’s bank’s website, if a user should be foolish enough to login to check a balance while visiting Starbucks or McDonalds. It’s been known to happen.
Maybe even more problematic: Using eDellRoot’s private key, attackers can generate certificates to sign malware files. “Those files would generate less scary User Account Control prompts on affected Dell systems when executed,” writer Lucian Constantin explains on InfoWorld, “because they would appear to the OS as if they were signed by a trusted software publisher. Malicious system drivers signed with such a rogue certificate would also bypass the driver signature verification in 64-bit versions of Windows.”
The good news is that since this was made public Dell has come to its senses about this particular problem and has issued an automatic removal tool, as well as posting information on the manual removal of eDellRoot on its website. Dell has also announced that it began pushing a software update on Tuesday “that will check for the certificate, and if detected remove it.”
If you’re a Dell owner, the bad news is that eDellRoot very well might not be the only root certificate on your machine. There’s also DSDTestProvider, which is installed by an application called DSD or Dell System Detect. Users who visit the Dell support website are prompted to install this tool when they click the “Detect Product” button. So far, there’s no word on how to remove this one.
If you’re not a Dell owner, don’t be too quick to breath a sigh of relief. There might be bad news for you too, as the tech industry is leaving few stones unturned.
It might not matter what you’ve removed, what brand computer you use or even what operating system you’re running if you’ve got “Intel Inside.” This is due to something called Active Management Technology (AMT), which is Intel’s proprietary remote management and control system for PCs. It’s been around for a while now, and there are a lot of not-so-cool things about it. Among other things, it can change your BIOS configuration, wipe your disk and even do a system re-installation — and it runs even when your computer is off as long as it has access to a power source. Because it’s proprietary and secret, no one but Intel knows its exact scope.
 Oh, by the way, if your computer is off, it can turn it on. Nice trick, eh?
Oh, by the way, if your computer is off, it can turn it on. Nice trick, eh?
Understandably, the Free Software Foundation finds a lot to not like about this, mostly revolving around security issues. Also: “There could be a deliberate backdoor built into the implementation,” they add. “This is problem number one.”
But wait, there’s more: Even your ISP, at least if it’s Comcast, is out to get you.
You’d think the most hated company in the world might try to be careful and not tick off any more of its customers than it has already, but that’s evidently not the Comcast way. It seems that if you’re a Comcast customer, and if it comes to the their attention that you might be the boogeyman — meaning an illegal downloader of music, movies, and especially, NBC TV shows — then they’re going to insert and display a “gotcha!” warning in your browser. Evidently, they also do similar insertions to warn users about bandwidth usage issues.
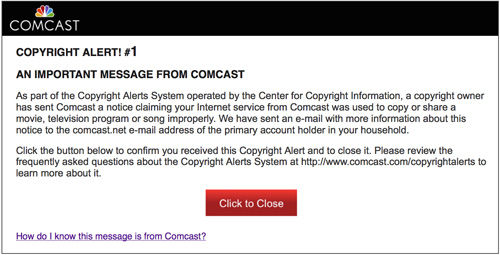
This makes the company a man-in-the-middle and should be a privacy and security concern for Comcast users, since it means they’re doing packet inspections on users’ traffic. It also means they can spoof a website’s ID and give a user the impression they’re on one site when they’re actually on another. And, as developer Jarred Sumner pointed out to ZDNet, “There are scarier scenarios where this could be used as a tool for censorship, surveillance, [or] selling personal information.”
I don’t know this for a fact, but it’s my guess that Comcast would say they’re doing none of these things; they’re just looking out for the poor content providers. After all, Sony’s been through some rough times recently.
Which brings us back to where we began: You might be excused for thinking that every tech company is out to get you.
That being said, happy Thanksgiving to those of you who reside in the U.S. If you live elsewhere…have a great Thursday.
Help keep FOSS Force strong. If you like this article, become a subscriber.
Christine Hall has been a journalist since 1971. In 2001, she began writing a weekly consumer computer column and started covering Linux and FOSS in 2002 after making the switch to GNU/Linux. Follow her on Twitter: @BrideOfLinux











So don’t use open networks. Use a wireless hotspot, such as your cell phone. But these stories exaggerate these risks; compute the probability that a hacker has your key and he is on your network, that is, he is in the same Starbucks you are in now, or very nearby, and he would have to be at that moment ready to somehow intercept your traffic and redirect it. I’m much more worried about real threats like Muslims attacking Times Square.
RE. R. Thornton:
“I’m much more worried about real threats like Muslims attacking Times Square”
Yes, that is a “real threat”, all be it a very tiny one, that would potentially effect a relatively small handful of people, compared to the millions of people that ‘are’ affected by the tactics/antics the article talks about.
Government surveillance is the biggest threat to our way of life today.
And I say this as a Brit’ that grew up under the constant threat of bombing by the Irish Republican Army. Britain managed without drastically undermining its’ democracy and the privacy of its’ citizens.
The surveillance measures in place today are only remotely about the threat of terror. And absolutely about every bad thing you can imagine a government would do to control its’ citizens given the means.
This goes far beyond intercepting wireless traffic, which is dead simple with these certs floating around. All you have to do is sit at any busy public wifi spot like an airport or hotel and wait for an affected machine to show up. You probably won’t wait long. Beyond the wireless issue is the certainty that malware providers will start providing digitally signed malware and rootkits via e-mail phishing, web site scripts, and more. Once you are infected, removing the cert will do you no good. You are already compromised at that point.
We need to take control of our machines from corporations that will trade our privacy and security for a thin dime of profit.
A friendly software tool to check installed security certs against a repository of well known ones that will report and backup/remove unknown ones would be a good start. Of course if you are on windows, this battle is already lost. Fun fact: A typical Windows machine comes preinstalled with several hundred certs that it trusts implicitly. Do you trust all those certs, or the companies issuing them?
I grew up in the 1930’s, when Nazi Germany became the enemy of the free world. Today I see much of the free world, led by the US, imposing the same surveillance in response to the same paranoia that we once hated and fought in Hitler’s day.
Is it only those who know something about IT who can see the problem? Is the general public still so blind? Or are they simply terrified that dissent will result in arrest?
Not yet, perhaps – but wait.
re surveillance: should your neighbor call the police if he sees someone snooping around your house, or not?
@Richard Thornton
False equivalency. Look it up.
Should you object to your neighbor peering in your second story window via a drone? How about if it is the government doing it becaus ethey are looking for “terrorists”, i.e. anyone that they don’t like.
Anyone concerned about surveillance and the bullshit agenda that the goverment is pushing should read the free e-book Little Brother, by Cory Doctorow:
http://craphound.com/littlebrother/download/
So what ya gonna do Mike? Live under a rock?
@Richard Thornton,
Hardly. I will continue to do what I do now. I run my own Linux distro that does absolutely nothing I don’t want it to. I encrypt everything and I don’t subscribe to services that slurp data. I also regularly use Tails and Tor for routine things to help keep Tor active to help provide anonymity for people using it. I am also currently experimenting with some new plugins that instead of preventing tracking, take the opposite approach and flood the data slurpers with garbage data, so their tracking and profiling become utterly useless. If lots of people start to use these new plugins, the data slurpers will literally be buried in a sea of useless data. That seems beautifully fitting.
I will also continue to speak out against the vile ignorance spewing from people like the director of the FBI regarding encryption. If necessary, I will use civil disobedience to defy any bans or laws against using encryption or other privacy and anonymity assisting technologies.
@Richard Thornton,
In other words, I will continue to use encryption regardless of any fiat from above. I will continue to assist others in doing so as well, spreading needed software as widely as possible, and even writing my own if need be.
Those fighting against encryption are going to lose. it is inevitable because reality will not oblige their dictatorial fantasies any more than it did those of the music or movie industries.
Mike maybe you’ll get lucky and join comrade Snowden in the muthaland.
The Sinatra family controls his catalog even dictating how many songs can be played each day on radio. In your perfect world, this would be disallowed?
@Richard Thornton
I honestly have no idea what you are talking about with regard to Sinatra’s music. Radio stations can only play music they are allowed to based on agreements with the people holding those copyrights, so…whatever.
If I bought a CD or a download of his songs, I could damn well play them whenever I like and no one has the right to know how many times, or even if I am listening to them at all.
…and Snowden did everyone in the U.S. a huge favor. Even those too stupid to realize it.
Mr Mike, does yur Linux distro handle uefi?
Please don’t feed the trolls.
Yes, please don’t feed those who dissent, after all, your freedom is at stake here. Show me how much $$$ you give monthly to FSF and the FreeBSD Foundation, and I will show you what I give. How many downloads of install CD’s have you actually paid a few bucks to the provider, such as Ubuntu, or OpenSUSE? My last copy of OpenBSD, version 5.8 was $50, or is it “money for nuthin’, chix for free”?
quote::I’m much more worried about real threats like Muslims attacking Times Square.::quote
Boy does you ignorance show.
Conflating Terror groups like ISIS with all Muslims is a definite sign of abject ignorance, and imagining the small possibility of Terrorists attacking Times square really shows your arrogance. Of course the fact that the Terrorism and manipulation of Middle Eastern politics carried out by the US government contributes to the danger all citizens of all Western countries face is something you probably never even consider.
Yes Tracy, please enlighten us on your understanding of muslim terror risks. Apparently in your view, there isn’t one? But if someone in the NSA has your metadata, is that like a violation of your body?
Enlighten me, as I am some stupid misogynist, white man.
quote::Yes Tracy, please enlighten us on your understanding of muslim terror risks.::quote
Muslims as a religious group are no more dangerous to the world than any other religious group. The very fact that you conflate Terrorism with Islam is a clear demonstration of your ignorance. The fact that those designated Terrorist are from Islamic countries currently, Islamic Countries where the US has waged or financed war upon war, in a effort to control access to oil, is not sufficient evidence to prove that ALL, or even a significant proportion of, Muslims are Terrorists. Not so long ago the great fear in the Western world was Communists under our beds, or more recently the Domino effect of South East Asian Countries falling to the Communist horde in black pajamas
The actions of the US government through out my lifetime (in South and Central and South America, Africa, South East Asia and the Middle East) deposing through direct and indirect actions, elected governments and helping to replace them with military dictatorships is Terrorist.
So too is the collection of Bulk data, which does nothing to stop the actions of Groups like ISIS/ISIL (And the protagonists in the Paris shootings didn’t even bother using encryption to hide their communications) or the killing of innocent civilians by home grown, predominantly Christian “madmen”.
I’m not actually sure what the bulk collection data does do, as all it seems to do is create bigger haystacks in which real terrorists can hide, other perhapd than create a chilling effect on free speech
“The actions of the US government through out my lifetime (in South and Central and South America, Africa, South East Asia and the Middle East) deposing through direct and indirect actions, elected governments and helping to replace them with military dictatorships is Terrorist.”
That’s not terrorism, that’s your opinion of various foreign policy decisions you don’t like.
Why yes, of course, if “we” do it it’s legal, above board, and merely a Foreign policy decision. But if someone else does it it’s Terrorism.
When the isis idiots start causing trouble in NYC or Philadelphia,
You’ll want some protection and suddenly your naive progressivism will take a backseat.
@Richard Thornton, richard witte, richie witte, or should we just call you dick?
>”Enlighten me, as I am some stupid misogynist, white man.”
First thing you’ve said that makes sense.
>”When the isis idiots start causing trouble in NYC or Philadelphia, You’ll want some protection and suddenly your naive progressivism will take a backseat.”
But wait, if we have all this collection of data and spying on citizens, then that can’t possibly happen, right? Ha ha, we all know the stuff the NSA is doing has pretty much zero effect on what ISIS does or does not do. There’s tons of surveillance right now and that didn’t stop the attacks in Paris. No, it’s a false tradeoff. The bulk spying and data collection keeps no one safe and destroys freedom in the process.
quote::You’ll want some protection and suddenly your naive progressivism will take a backseat.::quote
“naive progressivism” what an interesting and quaint choice of words.
But yes when the chickens come home to roost ie; “When the isis idiots start causing trouble in NYC or Philadelphia”. I will want protection.
Unfortunately for me, and you, incidentally, the bulk data collection brigade won’t be the ones providing it, as their record on stopping any sort of Terrorist “trouble” is a BIG FAT ZERO. Lets examine some of their notable failures.
Paris attacks, November 13, 2015: 129 dead. 400+ wounded. At least some of the attackers already known to police. They communicated via UNENCRYPTED SMS.
Thalys train attack, France: August 21, 2015. No deaths. Two wounded. Khazzani known to European authorities.
Curtis Culwell Center attack, Garland, Texas: May 3, 2015. One wounded. Elton Simpson on US no fly list, and had been convicted of a Terror related offense in 2011.
Shootings in Copenhagen, Denmark: February 14-15, 2015. Two dead. Five wounded. Omar Abdel Hamid El-Hussein was already known to Danish Security Agencies.
Shootings in Paris (Charlie Hebdo and Jewish supermarket): January 7-9, 2015. 17 dead. 20 wounded. Chérif Kouachi known to French Autorities.
Cafe seige, Sydney, Australia: December 15-16, 2014. Two dead. Four wounded. Man Haron Monis known to Australian Federal and State (NSW) Police and ASIO.
Canada attacks (Quebec car ramming and parliament shooting): October 20 and 22, 2014. Two dead. Four injured. Martin Couture-Rouleau known to Canadian Authorities.
Jewish Museum killings in Brussels: May 24, 2014. Four dead. Mehdi Nemmouche. Under surveillance by French counterterrorism police.
Beheading in Woolwich, London: May 22, 2013. One dead. Michael Adebolajo and Michael Adebowale known to British Authorities.
Boston Marathon bombing: April 15, 2013. Five dead. 260+ wounded. Tamerlan Tsarnaev was placed on two different U.S. government watchlists in late 2011.
Additionally, thanks to Ed Snowden we also know that Bulk Data Collection was being carried out well before September 11 2001, yet in spite of the fact that some of the hijackers were known to US Authorities, the attacks on the Trade Centre in NY was not stopped, nor was the attack on the Pentagon. The attack on the White house was foiled, not by the Bulk Collection Brigade, but by the heroism of the passengers aboard the plane.
Now while I have stated I would want protection, should said ISIS/ISIL chickens come home to roost, given the chances of actually being killed by terrorists is significantly lower than my chances of being killed by lightning or by a car while crossing the road, I’m not going to lose any sleep over the failures of the Bulk Collection Brigade. I will lose some sleep over the fact that Private communications with friends and family are being collected by people who exhibit such magnificent incomptence at performing what they claim to be their prime objective for collecting my private communications.
source https://theintercept.com/2015/11/18/terrorists-were-already-known-to-authorities/
As a side note to this conversation.
Those who, through ignorance or malice, or more likely both, conflate ALL Muslims with ISIS/ISIL or Terrorism in general play directly into ISIS/ISIL’s stated aims. Which is to drive a wedge between Islam and “The West”, thereby polarising the world into at least 2 waring camps.
In ISIS’s on line magazine Dabiq they have stated:
Muslims living in the West would soon no longer be welcome in their own societies. Treated with increasing suspicion, distrust and hostility by their fellow citizens as a result of the deadly shooting, Western Muslims would soon be forced to “either apostatize … or they [migrate] to the Islamic State, and thereby escape persecution from the crusader governments and citizens,” https://theintercept.com/2015/11/17/islamic-states-goal-eliminating-the-grayzone-of-coexistence-between-muslims-and-the-west/
Whether Terrorist Traitors use encryption or not, is somewhat irrelevant to the main point that this poison needs to be stopped,
because it could easily spiral out of control into a global conflagration. Snowden is safe in Moscow, and Putin will stop any Muslim terrorist activity with an iron fist. The USA & Europe cannot do this and this is a problem down the road, you will see that this situation is only going to get worse. But you know I love eating at Mamoun’s in Princeton, thus I don’t think that everything from Syria is a bad thing.
We all want a free society, but everyone has a different definition of what constitutes freedom – those who follow Stallman’s views 100% do not want any gov/corporate monitoring or metadata collection, no DRM, and I think patent protection for 10 years. Somewhere in the mix is the GPL and a venomous dislike of the BSD license, which I do not get at all. OpenBSD is much more “open” than any Linux OS.
But if you want no gov. intrusion on your email, why have any gov. intrusion in other ways such as pornography? If a private group wants to build Keystone, why not? If I want to pay only $5 per hour to my workers, why not? True freedom is to be who you want, when you want, and for as long as you want, and if that want is a small business, why should the government have any say in how this business is run? There is no congressional push to limit the profit rappers can make, but there is one at play to limit carried interest with hedge fund managers.
>”Somewhere in the mix is the GPL and a venomous dislike of the BSD license”
I don’t think there is so much a dislike of the BSD license as a feeling of it being inadequate to keep source free.
“Technically” there are fewer restrictions on a BSD license than a GPL one, but in practical use the only real restriction prevents someone from taking that free code, making a series of improvements to it and locking it all away behind a proprietary wall, as in Microsoft’s embrace, extend, extinguish philosophy.
I’ve heard developers rail against the GPL for “forcing” them to open source their code. That’s BS. If you are the author, you choose your own license. If you are building on someone else’s GPL code, then you are building on something its creators wanted to stay open and free. meaning: Either keep it free or build your own. The practical result is the GPL only restricts one type of person: The one who would take an existing free software project and lock it up. BSD provides no such protection.
>”True freedom is to be who you want, when you want, and for as long as you want, and if that want is a small business, why should the government have any say in how this business is run?”
Businesses aren’t people, counter to the prevailing attitudes in congress and the supreme court.
To clue you into the difference: Yes freedom is great, right up until your freedom damages mine. Thus building an environmental nightmare of an oil pipeline is not a matter of freedom, but rather a public issue.
Mike do you drive a car to work or burn oil in winter? If yes, guess you need oil right? You’d rather pay the wahhabis instead?
quote::Whether Terrorist Traitors use encryption or not, is somewhat irrelevant to the main point that this poison needs to be stopped,::quote
No one has argued against stopping terrorism. So Strawman.
quote::because it could easily spiral out of control into a global conflagration.::quote
There is already a danger of that due to the Terrorism of Major states, like the US performing via direct and indirect action “regime change” to replace, usually, democratically elected governments that won’t do things in a US corporation friendly way with, usually, military dictatorships that are very friendly the US corporations.
This creates the condition in which groups like ISIS/ISIL bread followers. So the existence of these “Terrorist Traitors” in inextricably bound to how the US, and the West in general, implements it’s foreign policy.
quote::Snowden is safe in Moscow,;;quote
No Snowden is not safe in Moscow. he is there at the pleasure of Putin.
1/ because he was not able to get to his intended destination… because the US government cancelled his passport while he was enroute to Moscow, which stranded him in Moscow.
2/ he is currently ensconced in Moscow, because it currently suits Putin to be able to flip the bird at the US.
quote::and Putin will stop any Muslim terrorist activity with an iron fist.::
No, like the West, he/Russia will retaliate, in largely ineffective ways, to attacks that his security forces failed to stop, because Russia, like the West, has bought into the Meme that collect every scrap of data possible will enable them to predict and stop terrorist actions. As we have already discussed… that doesn’t work.
The manner of Russia’s retaliation, will, like the manner in which the West retaliates, simply breed more terrorists.
quote::We all want a free society, but everyone has a different definition of what constitutes freedom – those who follow Stallman’s views 100% do not want any gov/corporate monitoring or metadata collection…::quote
This has nothing to do with Stallman. 1/ my private communications, regardless of the medium I’m using (whether it’s whispering in a friend’s ear or sending an email or any other form of electronic messaging that is supposed to be private) are no one’s business but that of the person I am communicating with and myself. 2/ Bulk data collection doesn’t work, it does not stop terrorist actions, as has already been discussed.
You claim that bulk collection does not stop terrorism, but you’ve offered me no proof, beyond various Web blogs which you prefer. None of your proof is court admissible, it’s all opinion.
Just like yours, opinion. The difference, my opinion is backed by verifiable facts, your’s no so much.
Each Terrorist attack I referred to was a verifiable failure of Bulk data collection, because the attacks are themselves verifiable as having occurred during a period of known Bulk data collection.
In addition almost all the terrorists were known to the police, that is a verifiable fact.
In addition it has been verified by various authorities that the Paris attackers did not use encryption, so their communications were in the clear, and easily readable by the bulk data collection agencies (no special decryption tools needed), even then they were not stopped.
So yes Bulk Data Collection does not work. Bulk Data Collection has not stopped a single Terrorist attack. Bulk Data Collection will never stop a terrorist attack.
The only thing Bulk Data Collection has ever achieved is hindsight, and given that the Terrorists don’t appear to care about escaping, hindsight won’t do us much good either, as the terrorist are either dead or captured, before the Bulk Data Collection Brigade begin searching for that elusive piece of Hindsight.
So what is Bulk Data Collection good for… the collection of every scrap of a citizens meta data that can be managed?
It doesn’t stop Terrorism, it doesn’t stop crime, it doesn’t make the world or the country, or my life more safe.
“They that can give up essential liberty to obtain a little temporary safety deserve neither liberty nor safety.”
Ben Franklin
Bulk Data Collection provides us with neither Liberty nor Safety, so in this case Ben Franklin nailed it, if any of us think that giving up our freedom to communicate privately will provide us with greater safety, they are wrong.
@Richard Thornton
quote::None of your proof is court admissible, it’s all opinion.::quote
Actually Richard you are correct I did not provide you with proof, Proof is something you find only in Mathematics.
What I did, however was show you evidence. Evidence of Bulk Data Collections failures.
Perhaps this is the sort of evidence that you prefer
Paris Massacre Mastermind Bragged About Infiltrating Europe in February Interview http://gawker.com/paris-massacre-mastermind-bragged-about-infiltrating-eu-1743509467
or perhaps this
Paris Attacks Plot Was Hatched in Plain Sight http://www.wsj.com/articles/paris-attacks-plot-was-hatched-in-plain-sight-1448587309
None of the Paris attacks are proof NSA bulk data collection failed – when it happens in NYC, then you will have a point, but clearly bulk data collection is not a panacea, no one ever implied it. And clearly Europe needs to figure out how its going to clean up its Muslim ghettos. I know what I would do, but I am not in charge. Since you have been very adept at stymieing any point I make, whats your plan? How are you going to stop/prevent another Hebdo attack? Getting out of Syria will not stop it, forcing all Jews out of Jerusalem will not stop it, kissing the backside of every Persian will not stop it, becoming a Muslim won’t stop it either, because you are still an infidel.
So Tracy, please tell me, what you would do, since you don’t seem to like any of my ideas or the Republicans. By the way, I am not a Republican.
@Richard Thornton
>”but clearly bulk data collection is not a panacea, no one ever implied it.”
A lot of people in the intelligence community and upper echelons of government certainly have. They still are…
Actually the Paris attacks are a valid example of how bulk data collection has failed to bring any measurable results. But fine, if you only care about attacks on U.S. soil, then how about the Boston Marathon bombing in 2013, or the 2009 shootings at Ft. Hood, TX for starters? Both of those took place in a culture of pervasive data collection. It did not help.
I’m sure someone could make an argument that it would help combat terrorism if the military and law enforcement were allowed to conduct searches of everyone’s homes without warning or warrant. I certainly wouldn’t agree that is a thing we should do no matter how compelling the argument. Bulk collection of private data and arguing against the availability of encryption for public communication is EXACTLY THE SAME. It is a step too far, even if it had benefits, which it doesn’t.
quote::None of the Paris attacks are proof NSA bulk data collection failed::quote
You are correct, they are NOT PROOF.
What they are is clear evidence that Bulk Data Collection does not work. You forget, in you myopic parochial world view, that The NSA isn’t the only agency that collects Bulk Data. The French Security services do it, The German Security Services do it. The British GCHQ Does it, Australia’s ASIO Does it, New Zealand’s Security services Do it, Canada does it, Russia Does it China Does it etc etc etc.
quote::but clearly bulk data collection is not a panacea, no one ever implied it.::quote
Actually many, many people in various governments have not only implied that Stopping Terrorism is the primary goal of Bulk Data Collection, They have outright stated it.
On the other hand I’m pleased to see that you finally recognise that Bulk Data Collection isn’t the answer.
quote:: How are you going to stop/prevent another Hebdo attack?::quote
Perhaps the Security agencies could go back to how they used to do it before Bulk Data Collection, just a thought, and actually do their jobs, and investigate those known to be likely terrorists.
They already knew most of the people in each of the attacks I posted earlier, but relied on a failed method… Bulk Data Collection.
quote:: Since you have been very adept at stymieing any point I make, whats your plan? ::quote
I “stymie” your points because you don’t have any facts to back them up, merely anger and ignorance and, as far as I can tell, xonophobia.
I don’t have a plan, but I seem to be in no better position there than my government, or any other Western Government. What I can see, looking back at recent history, a hell of lot of which I’ve lived through, is that the situation is as it is because “we”, the West, created it.
quote:: Getting out of Syria will not stop it, forcing all Jews out of Jerusalem will not stop it, kissing the backside of every Persian will not stop it, becoming a Muslim won’t stop it either, because you are still an infidel. ::quote
You are correct, none of those things will stop it, it’s too late, our chickens have come home to roost.
“For they have sown the wind, and they shall reap the whirlwind: it hath no stalk: the bud shall yield no meal: if so be it yield, the strangers shall swallow it up” Hosea 8:7
The West has sown the winds, by attempting to manipulate the politics of the Middle East, to their commercial advantage, and now they reap the whirlwind, as the angry and the ignorant are subsumed by evil men who use Religion (it’s always religion) to control and direct that anger.
quote::…since you don’t seem to like any of my ideas or the Republicans. By the way, I am not a Republican.::quote
I have not once mentioned any political party, either as liking or disliking, so you have no idea what I think of Republicans or Democrats or any other political party.
I don’t care what political party you favour, I’m not in the slightest interested.
I’m only interested in the conversation we’ve been having that centres on your ignorance.
You remind me a lot of the Fundamentalist Christians I used to debate, back in the late 90s and early 00s. No matter how much evidence one presented them with they always did 2 things.
1/ ignored the evidence, claiming it wasn’t proof.
2/ confused proof, a mathematical concept, with evidence.
You are rather conceited to assume that you convinced me of anything; I have never stated bulk collection will prevent anything – what I have stated is that I would back it politically; Beyond that, there is nothing else to discuss.
quote::You are rather conceited to assume that you convinced me of anything;::quote
Sadly you seem to be correct. I had hopes.
quote::I have never stated bulk collection will prevent anything – what I have stated is that I would back it politically;
I’m quite sure you said a lot more than that, in various posts, and you obviously still live in hope that it is useful for it’d stated purpose.
quote::Beyond that, there is nothing else to discuss.::quote
A pity I was enjoying our conversation.
Here’s a question you might like to ponder. If Bulk Data Collection doesn’t stop terrorism, what might it actually be useful for?
Re bulk collection : the intent obviously was post 9/11.
See ya around Ms. Kosa.
quote::Re bulk collection : the intent obviously was post 9/11. ::quote
As anyone paying attention should already know, and as I pointed out in an earlier post. Thanks to Ed Snowdon, we know that Bulk Data Collection was occurring prior to September 11, 2001.
Bulk Data Collection failed to stop the terrorist attack on The New Trade Centre, it also failed to stop the Terrorist attack on the Pentagon, and it failed to stop the Terrorist attack on the White House… That attack was foiled by the heroic actions of the passengers of that particular aircraft.
Bulk Data Collection Failed, even though the authorities were aware of some of the Terrorists involved, prior to the attacks.
All in all, Bulk Data Collection is a Fail, for the purpose it has been sold to us. So what is it useful for?
There were many traitors before 9.11, thus government monitoring was a necessity. It still is.
@richard thorton Here at FOSS Force we believe that fear doesn’t mean we drop our principles and throw away the rights we’ve fought for over two hundred years (in this country) to have and maintain. One of those rights is the right to free expression, which is why we give people to opportunity to post comments on FOSS Force that might be the exact opposite of what we believe.
However, Richard, you have more than made your point — especially given the fact that this article gives absolutely no mention of the NSA, Homeland Security or terrorism.
Give it a rest, Richard. We get it. You have monsters under your bed and you are fearful for the future. So do and are we all. Different monsters, perhaps, and different fears. Certainly different ways of handling them.
It’s time for this discussion to turn to the article above or for it to go silent.
@tracyanne Please don’t feed the trolls.
quote::There were many traitors before 9.11, thus government monitoring was a necessity. It still is.::quote
Finally someone with the balls to answer the question “if Bulk Data Collection isn’t for the purpose it has been sold to us (stopping Terrorism), what is it useful for?”
So in a free Society, with free speech protection, who decides who the traitors are? Or is all speech not approved by the government a thought crime, as it is in China?
@FOSS Force… Sorry, I had already written the above, but hadn’t posted it, as I was interrupted, and had to attend to some friends. It wasn’t until after I posted this riposte that I saw your message.
I will leave the troll alone.
By all means, end this thread, but look back to the top – I did not start this thread down a path of discussing bulk collection – your good friend Mike did. I said this: “So don’t use open networks. Use a wireless hotspot, such as your cell phone. But these stories exaggerate these risks; compute the probability that a hacker has your key and he is on your network, that is, he is in the same Starbucks you are in now, or very nearby, and he would have to be at that moment ready to somehow intercept your traffic and redirect it. I’m much more worried about real threats like Muslims attacking Times Square.”
So let me close by restating my position, which will never change – “Don’t want to be hacked? Then use your own controlled, relatively encrypted network, namely your own wireless account when you are at the mall, or wherever, and turn off bluetooth.”
I use a jetpack from Verizon – i find it very handy. By the way, I am not a troll, and I am not stupid. I have been a regular user of Linux & OpenBSD since 1998 and i am an active contributor financially to open source projects.
You people supported Ed Snowden – I didn’t – he was a traitor, and he violated his oath; So, go back to your world, and I will go back to mine, and I will never post here again, that’s a promise, other than a like of Linux, we have zero in common.
You can find me on Ubuntu – http://ubuntuforums.org/member.php?u=1842352
@Richard Thornton, aka Richard Erwin Thornton, aka Richie Witte, aka Richard Witte
>“Don’t want to be hacked? Then use your own controlled, relatively encrypted network, namely your own wireless account when you are at the mall, or wherever, and turn off bluetooth.”
Hilariously naive.
He’s not a troll, just impaired.
I’m sorry, but the pat characterization of Snowden as a garden-variety traitor is ridiculous and blinkered and puts a hell of a lot of faith in non-transparent power wielded by the state.
I took the same oath, signed the same NDAs, etc. as Snowden did when I had my clearance. He absolutely violated the letter of these items. Of that there is no doubt. However, he was privy to actual violations of private citizens’ rights, conducted by the agencies he worked for. Just as no soldier has an obligation to obey an illegal order, Snowden had no obligation to stay quiet about rampant illegal acts committed against us in our own names by our own government.
The fact that he had to go AROUND the whistleblower system is not an indictment of HIM, it’s an indictment of the SYSTEM. Just ask William Binney, Thomas Drake, and others.
FTR, I’m a libertarian and find much of the corporate bogeyman-speak espoused here to be repulsive as well, not to mention the blind faith in Net Neutrality and the mild hostility to individualism and free enterprise, so no need to go to the “liberal” well on this one.