No matter what you might have heard or read, it appears as if last week’s defacement of openSUSE’s news site didn’t affect download images of either openSUSE or SLES.
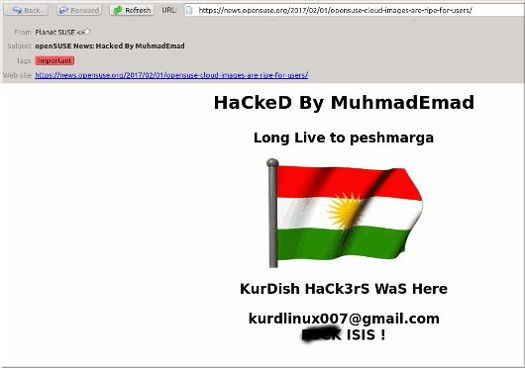
There’s a good chance you’ve already heard the news that a week ago today the openSUSE News site was defaced with an anti-ISIS message by a Kurdish group. Yup, that happened and was quickly fixed. You might also have heard that the hack went much deeper and that openSUSE, perhaps even SUSE, might have hosted hacked versions of their distros with a newly added backdoor. Nope. All indications are this never happened.
This all started when openSUSE’s news site began displaying the Kurdish flag along with the message “HaCkeD by MuhmadEmad; Long Live to peshmerga; KurDish HaCk3Rs Was Here,” followed by a Gmail address and a remark about ISIS that’s not not necessarily suitable for young eyes. Peshmerga, by the way, is the military of Iraqi Kurdistan.
The defacement wasn’t up long, and openSUSE chairman Richard Brown told Softpedia, “Yes, it got defaced. That server is isolated from the majority of openSUSE infrastructure by design, so there was no breach of any other of openSUSE’s infrastructure, especially our build, test & download systems. Our offered downloads remain safe and consistent and there was no breach of any openSUSE contributor data.”
That should’ve been the end of it, but on Thursday a popular free software blogger and web publisher was calling the incident a cover-up, and calling into question whether both openSUSE and SUSE binaries were compromised, while chastising IDG and Softpedia for giving “SUSE the benefit of the doubt” in their coverage. There was no proof offered — just a big how-do-we-know question mark and a call for the folks with openSUSE to prove they aren’t lying.
The claim was made because…well, Linux users have long memories and SUSE’s history still follows it around.
Many years ago, SUSE was purchased by Novell and under its ownership, Novell signed an agreement with Microsoft which freed SUSE users from having to worry about legal actions for infringing Microsoft patents that Redmond still claims Linux violates. While the agreement might or might not have been in violation of the GPL, it certainly violated the spirit of the license. Needless to say, the agreement wasn’t well received by open source supporters. It also appears that some aren’t ready to forget.
That was years ago, however. SUSE is no longer owned by Novell, and Novell doesn’t exist anymore, except as a division of Micro Focus. These days, SUSE operates as an autonomous business unit of Micro Focus, which it’s done since 2014. Also, openSUSE is not SUSE, although it would be fair to say that the community project is controlled by SUSE — in much the same way that Red Hat controls Fedora.
Some inconsequential remnants of SUSE’s old relationship with Novell remain, however; both the domain names and the IP addresses used by SUSE/openSUSE are still listed as being owned by Novell. If I were SUSE, I think I’d take care of that and have both transferred to my name. There’s no need to remind people of a history that’s better left forgotten.
All indications are that the defacer of the openSUSE News site, which operates as a subdomain of openSUSE.org, leveraged a widely reported vulnerability in WordPress that has recently been responsible for more than 2 million WordPress sites being hacked. The vulnerability was fixed in late January with the WordPress 4.7.2 update.
Nearly all versions of versions 4.7.x or 4.6.x would have had the patch automatically applied by WordPress (either to 4.7.2 or 4.6.2) in an automatic update. However, a number of websites either disable the auto-update feature or continue to use older versions, often due to abandoned plugins that won’t work with current versions of WordPress or site modifications that would be lost in an update. None of these are good reasons for not keeping a site up-to-date, however. Abandoned plugins and out-of-date versions of WordPress pose security risks — especially since the widespread use of the platform makes it a large target.
The main sites for both openSUSE and SUSE, where the downloadable binaries are available, don’t seem to be running WordPress. A look at the source code for both sites show no calls to WordPress directories and attempts to reach the default login page for WordPress (“/wp-admin/”) returns 404, “page not found,” errors. In addition, the website Built With doesn’t list WordPress as being part of either site’s infrastructure — although it does correctly identify the openSUSE News site — as well as FOSS Force — as using WordPress.
This makes it unlikely that those who defaced openSUSE News on Monday were able to leverage the vulnerability to damage either openSUSE’s or SUSE’s main sites.
Although it might be possible to gain server access to do cross-site damage, especially for sites using PHP injection plugins, there is no evidence that any of the black hats taking advantage of this security hole are doing anything other than simply defacing sites. A cross-site attack would also require that all sites be on the same server, and there’s no evidence one way or the other that this is the case.
Christine Hall has been a journalist since 1971. In 2001, she began writing a weekly consumer computer column and started covering Linux and FOSS in 2002 after making the switch to GNU/Linux. Follow her on Twitter: @BrideOfLinux








Wow! Talk about blowing them out of the water! Impressive Christine! Glad to see that there are still level-headed, logic-powered, minds that drew me to FOSS Force and Open Source software. I’ve seriously had enough of the people running around every time something happens in the world of open source claiming it’s worse than Windows orthat the “sky is falling”. If the person who had made those claims / demands had just done their homework?…you wouldn’t have had to turn their entire argument into a force-fed-fact-finding-feast!…Lol! Once again bravo and please keep up the good work!
P.S. On another note, I wuld love to become a “walking billboard” for you guys, is there any merchandise you guys have for sale to the general public?…(t-shirts, hats, coffee mugs etc.) I guess let me know and enjoy the day!!