One surprise in this year’s Cost of a Data Breach Report is that generative AI is being successfully used not only to prevent data breaches, but to substantially lower the cost of a breach when one happens.

One thing I didn’t expect when IBM released this year’s Cost of a Data Breach Report last week was news that some of the early work that’s being done developing generative AI software for data center security is already paying off big time. Another unexpected takeaway is that in the case of ransomware attacks with encrypted data, working with law enforcement will generally yield better results than attempting to payoff the attackers directly.
Otherwise, much of the news in this year’s report is what we’re used to hearing year after year. The cost of being breached continues to rise and this year’s breaches were more disruptive than they were last year. This is putting more demand on cyber teams during a time when data centers worldwide are in the midst of a staffing shortage, which the report says appears to be responsible for a number of breaches.
Breach costs went up 10% from last year, the largest yearly jump since the pandemic, and 70% of breached organizations reported that the breach caused significant or very significant disruption. Collateral damage from data breaches has also intensified, with lost business and post-breach and third-party response driving a cost spike.
“Businesses are caught in a continuous cycle of breaches, containment, and fallout response,” Kevin Skapinetz, VP of Strategy and Product Design at IBM Security said in a statement. “This cycle now often includes investments in strengthening security defenses and passing breach expenses on to consumers – making security the new cost of doing business.”
The Cost of a Data Breach Report has been published annually for 19 years, and during that time has studied more than 6,000 breaches. The 2024 report analyses 604 breaches that occurred worldwide between March 2023 and February 2024. The research was conducted by Ponemon Institute and then analyzed by IBM.
What’s Working for the Black Hats
The report identifies three key areas that black hats are exploiting get inside locked systems:
- Security staffing shortages: This report isn’t the only alarm that’s sounded recently about staffing issues at data centers. In its recently released Global Data Center Survey Results 2024 report, data center researcher Uptime Institute also identified ongoing staff shortages at data centers as an ongoing security risk factor.
Source: IBM
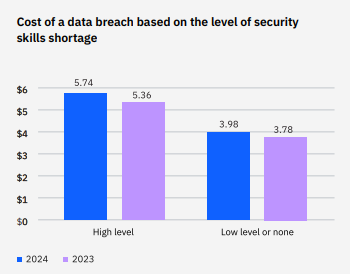
IBM’s Data Breach Report found there’s been a 26% increase in organizations facing severe staffing shortages this year compared to last year, with more than half of the organizations included in the study having severe or high-level staffing shortages. IBM also found a correlation between security staffing levels and the costs associated with a breach: $5.74 million for high level shortages vs. $3.98 million for low levels or none.A similar cost fluctuation was associated with employee training. Organizations with low levels of employee training experienced costs of $5.10 million per breach, compared to organizations with well trained employees, where the cost dropped to $4.15 million.
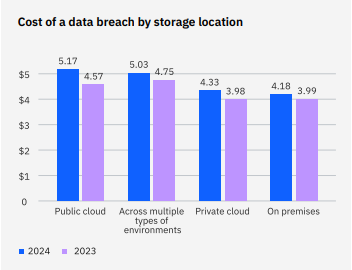
Source: IBM - Data visibility gaps: Forty percent of breaches involved data stored across multiple environments that included public cloud, private cloud, and on-premises. These breaches cost more than $5 million on average and took the longest to identify and contain, although they weren’t the most expensive. That distinction goes to data breaches solely involving public clouds, which cost $5.17 million on average. On-premises breaches were the least costly.
-
Stolen credentials: At 16%, stolen and/or compromised credentials was the most common initial attack vector. These breaches also took the longest to identity and contain at nearly 10 months. Compromised credential attacks are also expensive, costing an average of $4.81 million per breach. Phishing came in a close second and was actually more costly, at $4.88 million each. Malicious insider attacks cost the most, at $4.99 million.
The White Hats’ Arsenal
At least one of the methods that the goods guys are using to ward off data breaches, and to contain them quickly when they happen, is employing a technology that’s so new that many people think it hasn’t really been harnessed yet:
- AI-Powered Prevention: IBM says that two out of three organizations studied for the report are deploying security AI and automation across their security operation centers. That seems to be working, because organizations using these technologies incurred an average of $2.2 million less in breach costs than those that aren’t using the AI/automation combination, making this the largest cost savings method in the 2024 report.
The number of organizations extensively using security AI and automation grew to 31% in this year’s study from 28% last year, a 10.7% increase. The share of those using AI and automation on a limited basis also grew from 33% to 36%, a 9.1% increase.
Generative AI’s newfound usefulness as a legitimate tool for the white hats is somewhat ironic, given that the recent rise in LLM workloads is also a tempting target for the bad guys, and is partly responsible for the rapidly escalating costs associated with data breaches.
“As generative AI rapidly permeates businesses, expanding the attack surface, these expenses will soon become unsustainable, compelling business to reassess security measures and response strategies,” Skapinetz said. “To get ahead, businesses should invest in new AI-driven defenses and develop the skills needed to address the emerging risks and opportunities presented by generative AI.”
- Utilizing Law Enforcement: Ransomware victims who brought law enforcement into the equation saved an average of nearly $1 million in costs compared to those who didn’t. Although this figure excludes any ransom payment, most ransomware victims who involved law enforcement were also able to avoid paying a ransom.
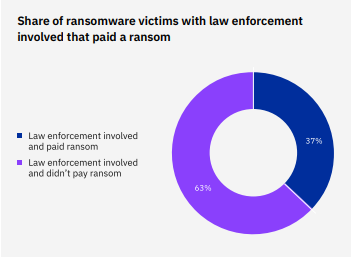
Source: IBM
For the report, three types of extortion attacks were examined: ransomware, where data is encrypted for the purpose of collecting a ransom; data exfiltration, where data is stolen, often for the purpose of extorting the company; and destructive, where attackers delete data and destroy systems. All three types of attacks required between 284 and 294 days to identify and contain.“Destructive attacks, or those attacks that are intended to cause lasting and expensive damage, reached an average of $5.68 million, and proved more costly than either ransomware attacks,” the report said.
Paying the Piper
The researchers behind the report also took a look at what industries had the highest breach costs, as well as who ends up footing the bill. Both cases were something of a roundup of the usual suspects:
- Critical infrastructure organizations see highest breach costs: Healthcare, financial services, industrial, technology, and energy organizations incurred the highest costs. For the 14th year in a row, healthcare participants saw the most expensive breaches, with average costs reaching $9.77 million per breach.
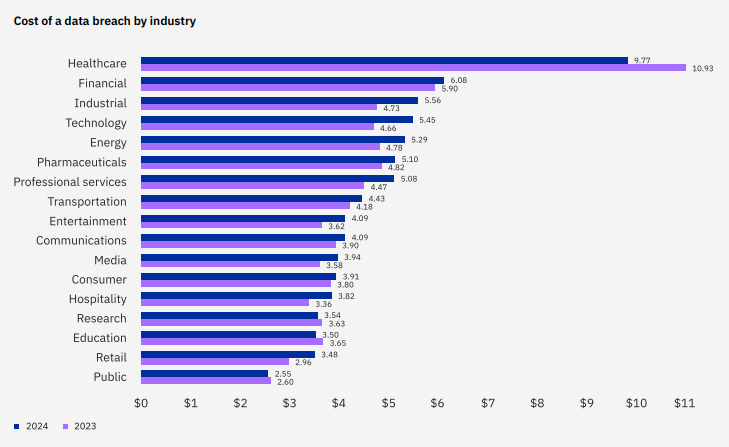
Source: IBM Although healthcare continued to have the highest cost, a distinction it’s held since 2011, the average breach cost for healthcare fell this year by 10.6%, to $9.77 million. IBM said that healthcare remains a target for attackers due to its dependence on technology, and because the nature of the business makes it vulnerable to disruptions that can put patient safety at risk.
- Breach costs passed to consumers: As is usual in the world of money and finance, it’s the consumer that ultimately foots the bill when a data breach happens. Of the companies that experienced breaches during the past year, 63% said they will or have already raised their prices to pay for this year’s breach. This represents a slight increase from last year when the number was 57%, and marks three years in a row in which the majority of organizations included in the study would take this action.
The Cost of Data Breach Report 2024 is available as a free download from IBM.
Christine Hall has been a journalist since 1971. In 2001, she began writing a weekly consumer computer column and started covering Linux and FOSS in 2002 after making the switch to GNU/Linux. Follow her on Twitter: @BrideOfLinux







