Members of the popular Patreon crowdfunding site for makers and artists who had accounts that were open before the beginning of October are now receiving threatening emails demanding payment of one Bitcoin (about $325 U.S) or else personal information such as Social Security number, tax id, tax forms, name, address, and credit card details will be made public.
Members of the popular Patreon crowdfunding site for makers and artists who had accounts that were open before the beginning of October are now receiving threatening emails demanding payment of one Bitcoin (about $325 U.S) or else personal information such as Social Security number, tax id, tax forms, name, address, and credit card details will be made public.
These emails come a little over a month and a half after the site announced that hackers had successfully broken into the site and had absconded with “gigabytes of data.” The emails have the words “I will leak your identity” in the subject, and all seem to have been sent from an AOL server.
In all of the emails, the message is the same:
“Unfortunately your data was leaked in the recent hacking of the Patreon web site and I now have your information. I have your tax id, tax forms, SSN, DOB, Name, Address, Credit card details and more sensitive data. Now, I can go ahead and leak your details online which would damage your credit score like hell and would create a lot of problems for you.
If you would like to prevent me from doing this then you need to send 1 bitcoin to the following BTC address.
Bitcoin Address:
1QAQTyhCzAfvp8uLpneBNamWTNRR1hx9CpYou can buy bitcoins using online exchanges easily. The bitcoin address is unique to you. Sending bitcoin takes take, so you better get started right now, you have 48 hours in total.”
Although the message claims “[t]he bitcoin address is unique to you,” examples of the email posted on various forums on the web all contain the same address.
The email appears to be a scam. The perpetrators of the hack posted the stolen data online almost immediately after the breach, so the email addresses, which were evidently stored in plain text, have been available for some time. User passwords may or may not be vulnerable. They were encrypted using bcrypt password encryption, but because the source code was also taken in the hack, security experts have cautioned that flaws might be found that will enable them to be un-encrypted.
In any event, not all data claimed be held by the sender(s) of the emails was contained in the dump according to Patreon’s CEO and founder Jack Conte, who wrote immediately following the intrusion:
“There was unauthorized access to registered names, email addresses, posts, and some shipping addresses. Additionally, some billing addresses that were added prior to 2014 were also accessed. We do not store full credit card numbers on our servers and no credit card numbers were compromised. Although accessed, all passwords, social security numbers and tax form information remain safely encrypted with a 2048-bit RSA key. No specific action is required of our users, but as a precaution I recommend that all users update their passwords on Patreon.”
The people at Patreon evidently also consider the email to be a scam. Although FOSS Force has been unable to contact anyone at the site for a comment, a user named “adencraft2k” posted on the EEVblog forum that he’d received the following reply after notifying Patreon of the email:
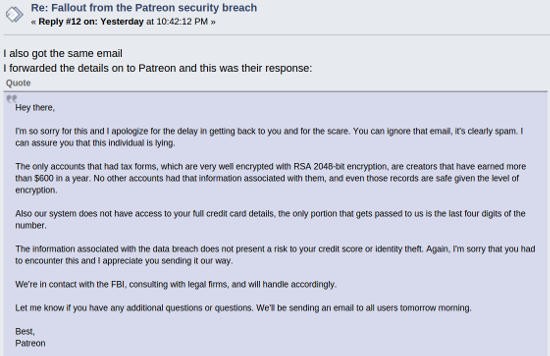
“Hey there,
I’m so sorry for this and I apologize for the delay in getting back to you and for the scare. You can ignore that email, it’s clearly spam. I can assure you that this individual is lying.
The only accounts that had tax forms, which are very well encrypted with RSA 2048-bit encryption, are creators that have earned more than $600 in a year. No other accounts had that information associated with them, and even those records are safe given the level of encryption.
Also our system does not have access to your full credit card details, the only portion that gets passed to us is the last four digits of the number.
The information associated with the data breach does not present a risk to your credit score or identity theft. Again, I’m sorry that you had to encounter this and I appreciate you sending it our way.
We’re in contact with the FBI, consulting with legal firms, and will handle accordingly.
Let me know if you have any additional questions. We’ll be sending an email to all users tomorrow morning.
Best,
Patreon”
And just moments after we initially posted this article, Patreon sent an email to all of its members affected by the hack, signed by CEO Conte:
“I learned yesterday evening that some Patreon users have been receiving a scam email. The sender claims to have the recipient’s SSN, credit card number and other personal information. I want to assure everyone that the claims in this email are false, and we are already working with federal law enforcement. Do not reply to the email—it is a scam. The tax forms we store are securely encrypted with RSA 2048-bit encryption, and we do not store full credit card numbers.
If you receive this email I suggest you flag it as spam and ignore any further emails. Do not reply.
Thanks.
Jack Conte, CEO/Co-founder, Patreon”
Early this evening, FOSS Force was contacted via email by Patreon’s Operations Manager, Chelsea Wagenbrenner, who basically agreed with what we’ve been hearing from the site all afternoon. She also answered a question we’d posed when we’d first contacted the site for a comment.
We’d asked about users who might have used a password they also use on other sites — a common but not advisable practice. “Is there any way for a user who is worried about the hack and who has forgotten their password to recover it for the purpose of knowing where else they might need to change passwords?” we asked.
“We hash the passwords with bcrypt using unique salts, so there is no way for us or anyone else to recover the passwords,” she answered, which was not unexpected since that’s the way bcrypt is designed. “As a general best practice we encourage users to not reuse passwords on multiple sites, and there is no evidence that anyone has managed to compromise the leaked passwords.”
Any Patreon member who received this email probably shouldn’t be alarmed. However, if before the breach your Patreon account used a password that you use on other sites, you would be advised to change all uses of that password, just to be on the safe side.
Editor’s note: This article was updated on November 21, 2015 at 3:59 p.m. EST to include email sent to members by Patreon CEO Jack Conte.
This article was again updated on November 21, 2015 at approximately 10:30 p.m. EST to include information we received by email from Patreon’s Operations Manager Chesea Wagenbrenner.
Help keep FOSS Force strong. If you like this article, become a subscriber.
Christine Hall has been a journalist since 1971. In 2001, she began writing a weekly consumer computer column and started covering Linux and FOSS in 2002 after making the switch to GNU/Linux. Follow her on Twitter: @BrideOfLinux