The hackers who compromised the Linux Mint site on Saturday were evidently not the brightest stars in the dark web, but they managed to create a mess for the Mint crew to clear away.
Everybody understands that none of a stage magician’s tricks are real. The one thing that is real, and which a successful illusionist must practice to perfection, is the art of misdirection — which evidently turned out the be the trick under the sleeves of the cracker/hackers who were responsible for compromising ISO downloads of Linux Mint 17.3 Cinnamon on Saturday.
In the FOSS Force news article on the hack which ran Sunday, we said “the hackers modified the ISO of the Cinnamon edition of Linux Mint 17.3 (Rosa).” We now know that’s not quite true, or at least not in the way we meant. The hackers didn’t bust into the Mint server and modify the binaries waiting to be grabbed by the mirror sites for downloads. Instead, this was a case of misdirection.
The hackers had a copy of Mint with their malicious payload in place, packaged as an ISO image and sitting on a Bulgarian server they controlled, waiting to serve downloads of what is arguably the worlds most popular version of GNU/Linux. The intrusion at Mint was a quick in-and-out to change the URLs in the anchor tags on Mint’s download page for the 64-bit Cinnamon version of Linux Mint 17.3 “Rosa.” Afterwards, users who clicked on a link to download from, say, the Internet Solutions mirror in South Africa, were taken to the hackers’ server in Bulgaria. Let the download begin. Wham, bam, thank you mam.
“Basically, it affected Linux Mint 17.3 ‘Rosa’ — Cinnamon (64-bit) only,” Matt Hartley wrote in an email Sunday night. “32-bit and other spins and versions were left alone. Also Linux Mint 17.3 ‘Rosa’ — Cinnamon (64-bit) torrents were untouched.”
Hartley is the founder and a contributor at the Freedom Penguin website, and covers Linux and open source software for the popular tech news site Datamation. I contacted him after he reported in an article he penned for Freedom Penguin on the hack, that he had “saved a cached copy of the download page for Linux Mint 17.3 Cinnamon edition.”
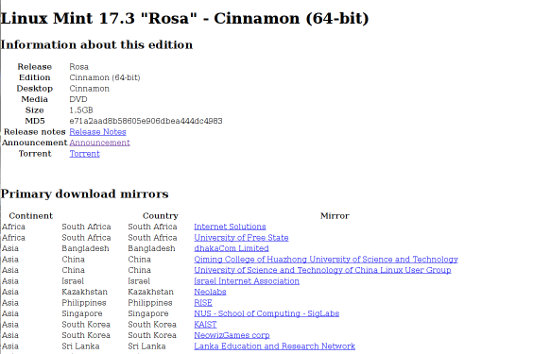
“Every single download for each country is pointing to the malicious IP address,” he wrote in the article. “Worse, the mere act of clicking on any of the download links instantly starts the download process — no browsing of the directory.”
Hartley was good enough to supply us with both a screenshot of the download page in question, and the underlying HTML source code. A look at the source code reveals that all of the links to mirror sites link to IP address 5.104.175.212, which was identified on Sunday by Linux Mint project leader Clem Lefebvre as the IP address hosting the hacked ISOs.
“This was a drive-by thing,” Hartley concludes in his email, “not aimed at the the various versions and spins.”
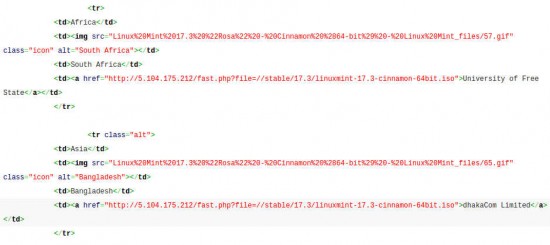
Click to enlarge.
The Mint server actually suffered back-to-back hits by the hackers. After the initial intrusion was detected and the Mint team had repaired the damage and officially announced the breach, the download page was hit again — leading the Mint crew to take the entire site down until they can determine how the group is getting into the server and plug the hole. The group initially gained server access through the distro’s WordPress blog.
During the breach, the hackers were also able to gain access to the sites forum database, the contents of which were offered for sale on the darknet website TheRealDeal for 0.1910 Bitcoin, or $85. Since then, the forum’s config file has appeared on a Hacker News discussions thread.
At Softpedia, Catalin Cimpanu speculates that, for a variety of reasons, the hack is not the work of seasoned professionals. One reason is the low price asked for the database contents. Another is the double hack on the Mint server. “With site access still working,” he writes, “and with the Linux Mint team failing to detect their true entry point, all the hackers had to do was to wait.”
Cimpanu also notes that the malicious payload, which he describes as “a simple IRC bot used for launching DDoS attacks,” wasn’t very sophisticated and wouldn’t maximize the financial potential of the hack.
We’re currently in the midst of our 2016 Indiegogo fundraising drive. Your support is crucial. Won’t you please visit our fundraising page and make a contribution to support FOSS Force?
Christine Hall has been a journalist since 1971. In 2001, she began writing a weekly consumer computer column and started covering Linux and FOSS in 2002 after making the switch to GNU/Linux. Follow her on Twitter: @BrideOfLinux








Good discussion of the internal flaws behind the success of the attack:
http://lwn.net/Articles/676613/
http://www.linuxmint.com is down
I just received my first spam, to the email address I use for Linux Mint’s forum.
Apparently an unnamed sender paid $2450 to ship me a package via USPS, and all I have to do is open the contained in voice on the Windows machine, I don’t have, in MS Word.
Isn’t that service.
@tracyanne I always knew you’re a lucky person. 😉
Lessons they should take away from this:
1) Don’t tie the site hosting binary downloads to any kind of forum, wordpress or other complicated and vulnerable software.
2) Don’t rely on MD5 hashing to validate binaries. While it wasn’t compromised in this case, it could have been. MD5 is weak and vulnerable to malicious tampering, yet it is still widely used. WHY? Switch to SHA-1 at least or even better: SHA-256.
3) Use public/private key pairs to digitally sign binaries. While hashes can indicate corruption and prevent tampering, they don’t provide any kind of guarantee of authorship. If intruders just change the hash on the web site users compare against, there is no way to tell. Signing against a public key that is widely available is much more useful to detect malicious behavior.
4) Have an off-site tool the periodically checks the site to ensure it isn’t serving modified files and alerts someone if a breach occurs.
I would also add my two cents worth, as I see it, criminals and script-kiddies, are evolving with the times, so maybe the security and prevention techniques should change as well. Lets get more aggressive, with access to and from the servers that we give access to and from. I guess there’s no real way to prevent certain things, but if we “double down” on certain areas, make those facets of the entire process even more impossible to get past, and this might mitigate the results of accessing other things / files / areas that we want to remain behind our “Iron Curtain”…..