 We might as well start with the moral of this story: Don’t protect Windows with Windows.
We might as well start with the moral of this story: Don’t protect Windows with Windows.
For at least a decade, Microsoft has been chanting the mantra, “at Microsoft security is job one,” over and over and over. During this time, it’s repeated this mantra often enough to convince a lot of people that Windows is much safer than it once was, which I suppose is true since it couldn’t have gotten much worse. However, a new report from AV-Test proves the company isn’t yet ready to move up to the next mantra level and begin chanting, “at Microsoft we do security right,” because clearly it doesn’t.
AV-Test is an independent German organization that evaluates and rates antivirus and security software for Windows and Android, and publishes the results of their tests every two months, offering certification to antivirus solutions that pass muster. Last Wednesday, the organization published some figures on the results of tests on various antivirus programs protecting Windows 7. Since then, the tech press has been having a heyday with the results — not because any particular antivirus solution emerged as a clear winner, but because Microsoft was the clear loser.
As I wrote a couple of weeks ago in another antivirus related story: Poor Microsoft can’t catch a break.
How poorly did Microsoft’s AV perform? So poorly that AV-Test wouldn’t recommend them. In a section of the report outlining why Windows 7 needs protection, the organization says this about Redmond’s own AV protection:
“An economical option for protecting a corporate network is the use of the endpoint module, bundled in the Microsoft Management Suite System Center 2012. The test revealed, however, that this is not to be recommended. The solution was awarded 0 points by the testers in terms of its protection function, and it achieved only 11 out of 18 possible points.”
Ouch! And the irony is, the Microsoft product wasn’t even being tested for certification, but as a comparative base.
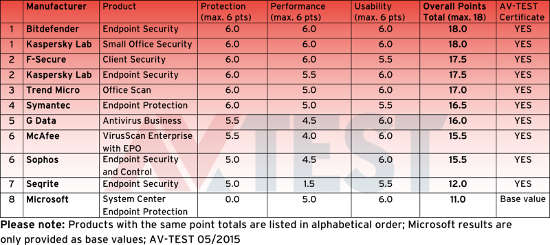
So let’s look at the comparison: Under the “Protection” heading, where Microsoft scored its zero, half of the apps tested received a rating of six, the maximum, and two companies’ products, Bitdefender and Kaspersky, received maximum scores across the board. Microsoft fared better in the other two sections, scoring five out of six points under “Performance,” which measures how much system resources a program uses, and six out of six points for “Usability.”
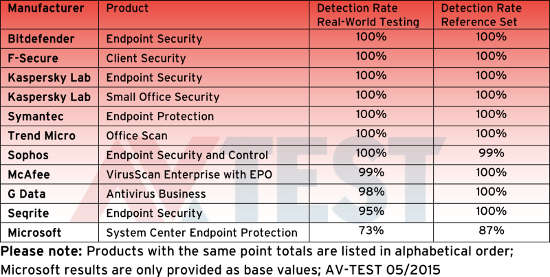
The failure came because the Microsoft product isn’t very good at recognizing threats — which is the whole purpose of AV programs. According to AV-Test. it failed at recognizing unknown threats by behavior and at recognizing known malware from it’s database of definitions:
“In this critical test area, a total of 6 products achieved a 100% detection rate, earning the maximum score of 6 points. This included Bitdefender, F-Secure, Trend Micro, Symantec, and both solutions from Kaspersky. Microsoft Security Essentials, tested for comparison, detected only 73 and 87 percent respectively in the test. This accounted for the rating of 0 points.”
I know what you’re thinking, especially those of you who defend Microsoft. You’re thinking that Microsoft’s anti-virus solution isn’t meant to be a last defense. Microsoft only expects its free AV to be used until a third party solution is implemented. Sounds good, but it’s wrong. Actually, Redmond pushes its AV on its website as all that’s really needed to keep a Windows machine safe and secure:
“Use Microsoft Security Essentials to help guard against viruses, spyware, and other malicious software. It provides real-time protection for your home or small business PCs.
“Microsoft Security Essentials is free and we designed it to be simple to install and easy to use. It runs quietly and efficiently in the background so you don’t have to worry about interruptions or making updates.”
I assume that most enterprise users of Microsoft products already know not to trust Redmond to handle Windows’ security. I worry, however, about the poor consumer who plops a thousand dollars down for a laptop, and thinks it’s just fine to stop in to use the free Wi-Fi at Mickey Dee’s for a quick check of the bank account while being protected by nothing more than the best Redmond has to offer.
Help keep FOSS Force strong. If you like this article, become a subscriber.
Christine Hall has been a journalist since 1971. In 2001, she began writing a weekly consumer computer column and started covering Linux and FOSS in 2002 after making the switch to GNU/Linux. Follow her on Twitter: @BrideOfLinux










This entire article is silly. If anyone anywhere still thinks that antivirus is actually effective at anything, they are delusional.
This is just an anti-microsoft fluff piece.
Boring.
Yes, the weakest link is the person. No AV product is 100% effective and you should always practice safe computing. MSE is an option that work without causing performance issues on some machines. Is it the best, no, is it fine for those that practice safe computing, absolutely. If you don’t trust the website or email, don’t go there or open it. Don’t allow preview pane either and make sure that scripting with emails (as well as web) is controlled.
@maestro, Andrew McGlashan
That’s why I no longer use Anti Virus on my computer, it’s a waste of time and money.
@maestro, Andrew McGlashan
This isn’t about MSE (Microsoft Security Essentials) or about protecting your home machine, this is about a product that is supposedly enterprise grade, to be used by businesses.
From Microsoft’s website:
“Microsoft System Center 2012 Endpoint Protection provides an antimalware and security solution for the Microsoft platform.”
Like in elementary school arithmetic, 2+2=5 is “a solution”, just not a good one.
Minority report: before I retired a few years ago, the university had some of the sharpest IT folks I knew of. Still do, as far as I know. Maybe I’m prejudiced because they let me set up a Linux box beside my required Windows box and gave me a network connection for it…
Anyhow, they had some flavor of enterprise-wide anti-virus and it caught a LOT of stuff AFTER it made it through a firewall that had some rules that were totally annoying, but did what they wanted. I knew they could watch where I went online and what I did while I was there when I used my university computer. If I were inclined to do anything “interesting,” it certainly wouldn’t have been on that network.
Ho-hum, don’t visit dodgy websites, don’t open emails from unknown sources, block javascript, etc. I was teaching all that (and practicing it) and telling my classes that something new was coming out each day that today’s catcher wouldn’t catch, but we’d hope that tomorrow’s catcher would. It was about this time that I began reading about malware that could infect a machine without user intervention–you didn’t need to open a file or preview a message.
And I showed’em it was true. One morning I went in and couldn’t get online. I went to our tech guy and asked if there were a problem with the network. He told me the IT people had notified him I was shut down because my computer had caught a “don’t have to do anything to get it” bug and it was irrevocable and immoral. (Wish I could remember the name.) It had been found in the wild and the update to catch it was pushed out to the campus computers in less than 18 hours. Apparently, another user and I got had during the hours before the update got to our computers. Oh, poo-poo.
The cure was (1) go grovel at the feet of the network lady (actually, she was very nice and quite helpful) and promise to do a (2) total wipe and reformat. Whatever it was infected the MBR and couldn’t be removed without a reformat. And the people in Computer Services were happy the other 2000 or so computers on campus didn’t get the bug I got.
One side of it is they knew me well enough to know I actually would do what they wanted, so they didn’t send me a tech to wipe the machine, install the “standard” load of software, and walk away. I booted off a Linux CD and backed up my data files to a USB hard drive, Then I spent the spent the spare moments and hours for the next three days reloading everything and getting it to running kind of like I needed for the classes I needed to support. Whew! Didn’t want to grade any papers or get ready for any classes or any of that for a few days, anyway.
Right now, this week, July 2015, I don’t worry much about malware because the only computers in the house run Linux. If I can make next year’s tax software run under WINE, I’ll really be happy.
But there are some people who have specific needs and can’t drop Windows entirely. They need to practice sanitary computing, of course. And based on my experience, I think they need the best anti-virus protection they can reasonably use, whether it’s for a home computer or a work computer.
FWIW, you might imagine a Computer Science professor who got his network access shut down would feel a little awkward. I did. However, the folks in Computer Services said I didn’t do anything and didn’t fail to do anything–that particular bug came through and until they got the updates pushed out, there wasn’t any stopping it.
FWIW-2, Ken Starkes likes this: I was the only Computer Science professor who ever had his network access shut down.
Twice.
From A Windows PC, create a bootable USB flash drive with just two downloads.
1) Rufus usb .ISO file burner/program to usb flash
http://rufus.akeo.ie/ a single .exe program file
2) puppylinux .iso file. Tahrpup 6.0.2 http://distro.ibiblio.org/puppylinux/puppy-tahr/iso/tahrpup%20-6.0-CE/ http://puppylinux.org/main/Download%20Latest%20Release.htm
3) insert usb flash drive to pc usb slot. Execute program. Rufus.exe. select proper usb flash drive, select puppylinux .I so file. Now burn .iso file to usb flash. Enjoy your new Linux usb flash drive.
4) reboot computer with usb flash drive inserted into slot. Puppylinux will now boot. If you have problems, check the BIOS settings for drive boot order. Select usb drive first, then removable media, CD or DVD disk, last in order, boot from hard drive
Other Tools:
Linux Live Usb burner application will ftp download 1of over 350 Linux distributions .Iso files and burn them in usb flash drive.
http://www.linuxliveusb.com/
10 minutes and you can test run Linux on your pc computer.
Goodbye virus problems. Hello secure online banking Fred
Great Article and posted comments.
Bsd anyone? http://www.pcbsd.org/ Try out version 10.1.2