The Heart of Linux
“You’ve got mail compromised mail!”
The emails started coming in slowly at first. Friends and colleagues were telling me that my Gmail address was pushing out spam.
“Spam? Really?”
My first inclination was to push those emails aside as a temporary albeit bothersome incident. Something similar had happened a few years earlier, but subsided quickly with no real or evident damage. I guessed that some bot did a drive by and picked up my email contacts and started pumping out spam and other messages.
 But this incident wasn’t to be pushed aside. The emails started coming in faster and faster, until I acknowledged that I had a real problem. Security hasn’t been and isn’t my strong suit. My passwords are almost an afterthought. After all, I am running Linux. What could go wrong?
But this incident wasn’t to be pushed aside. The emails started coming in faster and faster, until I acknowledged that I had a real problem. Security hasn’t been and isn’t my strong suit. My passwords are almost an afterthought. After all, I am running Linux. What could go wrong?
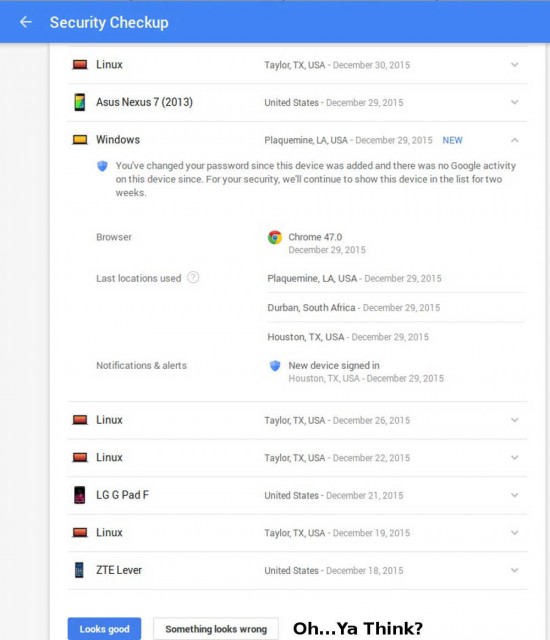
This can go wrong.
How it came to be, I don’t know. Someone had somehow gained full access to my fixedbylinux email account. Once I realized that this was indeed a serious problem, I immediately changed my Gmail passwords and kicked every Gmail add-on extension to the curb. I talked with my friends on Google+ in a conversation that was as enlightening as it was entertaining. The crux was clear. Maybe Linux is superior to other operating systems as far as viruses and malware are concerned, but if your browser is not properly up to date and patched, you share the malware playground with all the Windows users.
Luckily, the people in my G+ circles are some of the smartest, well-educated and helpful people I know. You cannot put a price on the kind of assistance they offered.
I am still trying to figure out the events that led to this intrusion. I’ve read almost everything there is to read on Google’s Gmail pages, without finding much. Google seems adamant about not giving-out one-on-one help, but maybe I just didn’t look long enough. On my own, I’ve evoked two step verification on my main email addresses, so that’s settled. But still…I’d like to figure out when and how this breach took place. What magic sequence of events happened to allow this?
Did I mention I’m a security idiot? Yeah…I thought I did.
It feels strange to again delve into antivirus and malware protection. I’ve been a smug, self-assured dummy when it comes to online threats and Linux in general. And while what happened can’t really be blamed on Linux per se, it happened in a Linux neighborhood, so I am going to arm myself against any and all malware comers
Although I’m not above paying for good software, trying to discern what software is good and which is shiny junk can be a daunting challenge, especially in the Linuxsphere. In the tests I’ve studied over the past four days, ClamAV seems to be an online favorite, but they lack the one thing I am going to need on our Reglue kid’s computers: a friendly, useful graphical interface. I’m not going to tell an 11-year-old to drop to the command line to do anything, even if they do need to learn that the blinking prompt can make magic things happen. In time, I will teach them, but for now…. ClamAV failed the initial tests.
I was initially happy with what ESET NOD32 had to offer. It does have an extremely attractive front end, but that’s where it stops. After installation, ESET ran its tests and upon finishing, it reported that it had detected one threat or virus. Okay, where is it? I spent 30 minutes digging around in the guts of ESET and on its forums, trying to find anything on this at all. Seems I am not alone in this quest. After I discovered the number of people who had this same problem, which was not being addressed, I used the removal tool and told it goodbye. It also fully screwed-up the refresh mode on Mint’s software update tool while it was installed. Once removed, updating was fixed as well.
Today I am going to look through your responses and ideas on the matter, because after all, most of you have forgotten more about Linux and security than I will ever know. So yeah, I do value what you have to say; I always have. The two-step verification is kind of a pain in the ass, given how often I am in and out of my email, on at least three devices a day, but I suppose that’s the world we live in now. The best we can do is stay one step ahead of the bad guys.
One step, at the least.
We’re currently in the midst of our 2016 Indiegogo fundraising drive. Your support is crucial. Won’t you please visit our fundraising page and make a contribution to support FOSS Force?
Ken Starks is the founder of the Helios Project and Reglue, which for 20 years provided refurbished older computers running Linux to disadvantaged school kids, as well as providing digital help for senior citizens, in the Austin, Texas area. He was a columnist for FOSS Force from 2013-2016, and remains part of our family. Follow him on Twitter: @Reglue







Have you thought about getting your own domain, and providing an email service to your kids. That way you can keep better tabs on what’s going on, and use ClamAV at the server end, along with a bunch of other anti spam, anti malware tools.
There are actually some very nice GUI frontends for ClamAV though they are not built into it – that’s become less common in Linux the last few years but it was a common thing not long ago – most software was commandline and other people would write GUI’s for it when it made sense to them.
KlamAV used to be the goto frontend (KDE based) but it looks like it hasn’t been updated in a while. Still a quick google found me a half dozen other options all worth having a look at.
So, what leads you to believe that it was something on your computer that potentially a virus scanner could detect? Because such things on Linux are so rare anyway, I don’t think the command line way to do it is such a bad way to go.
Here’s an attack I’ve heard about, it may be what happened to you, or something entirely different might have happened.
1) An ad runs some javascript that waits for the tab not to be interacted with for at least some minutes.
2) The script then replaces the page by one that looks exactly like a gmail login page, including the tab title and icon, and even the address bar looks (almost?) right.
3) The user wants to use gmail, sees an already open gmail tab that they believe they must have forgotten about, logs in… and gives away their password.
The problem is that we expect browsers to handle private data, while also expecting them run code from literally any source anywhere. For as long as that combination of expectations exists, there will be all sorts of exploits. By the way, loading data (images, videos…) that might trigger a bug somewhere in the browser or a library that it uses also counts as allowing to run code from a source. The problem is not limited to just javascript, java and flash.
Browsers really should be run in a sandbox without access to the file system (which is a pain when you want to download or upload files). Furthermore one should use a different looking browser and sandbox for banking and email and such, so evil from the rest of the web cannot get to that and cannot fool you.
Am I taking these precautions myself? No, I am not. Is this going to cause me trouble? Yes, probably, eventually, just like it’s going to cause trouble for everyone else.
(Fun fact: I have to disable the little bit of security I do have in place to make the captcha on this page work. Nice!)
My guess,
You configured a Windows PC and by happenstance chose to check your mail using it.
Solution: Set up two-factor authentication.
Use a local client (Evolution) to send your gmail and attach automatically add gpg signature to all correspondences.
The recipient need not do anything with the sig file, but you will be able to prove the authenticity of the email in the future.
I can’t speak to Firefox vulns, but Chromium on Linux has several layers of sandboxing. Use Chromium on Linux.
Anyone using Windows needs to have their head examined.
I got one of those emails from you btw. 🙂
Dietrich
Clarification to Ken on gpg signature use on gmail:
http://i.imgur.com/imtCR41.png
Years ago, I made the mistake of joining Adobe’s forum, with a question about Acrobat reader. (they dropped it and I used it for tax form filling under Linux) My big mistake was I used the same password for it as my email address, then didn’t change either.
They were hacked and shortly afterwards my email address began spamming. Once I checked the settings and changed my password, it stopped.
I think this was the site I used to check all my email addressed:
https://haveibeenpwned.com/
Only the one account was owned.
Don’t reuse passwords across sites.
Can’t remember them, have a master password for an encrypted file with your passwords and sites in a list.
Use capital letters and symbols and make them longer, example 2R3m3mb3rPa$$w0rds (substitution cyphers become second nature after you find what works for you).
Use a phrase, no spaces or a goal as a password.
Can’t think of more now (distracted), but I hope this will help you.
Hi,
Something similar has happened to me, all my PCs are Linux boxes and I access also my email from my Android phone. My email account is hosted by a French provider free.fr (and not Google).
The bad guys have clearly obtained access to my mailbox because the addresses to which the spam was being sent were clearly my contacts.
On some devices I had configured access to my malbox via IMAP/POP and not IMAPS/POPS. I guess that my password must have been sniffed. I’ve quickly changed my password and reconfigured all my email clients to use (more) secure protocols and things are getting more quiet.
Spam was being sent by waves. They are becoming smaller and less frequent (I see this by number of messages which come back to me).
Ken,
Are you sure the spam email is coming from your account?
It might be ‘spoofed on’ rather than ‘sent from’ your account.
This story was posted on LXer. I commented there with some hopefully helpful links and suggestions.
@dotmatrix,
The sender id in email can be forged. But an attached pgp signature file cannot. 😉
@Dietrich Schmitz:
You can verify if an email has been forged by checking the headers. I you got one of Ken’s spam mails — you can check it to see if it’s been spoofed.
I don’t think PGP is going to solve very much regarding SPAM email — whichever way you want to look at spam.
Going into an full analysis of email security from all sides is way too much to cover in a comment section.
@dotmatrix
RetroShare solves spam email.
I’ve been using it for secure communications for two years.
http://i.imgur.com/dYXqYS8.png
As I mentioned to Ken, using two-factor authentication will stop any man in the middle attack.
@DS:
I’m not sure running a P2P darknet client is going to help most people.
I haven’t looked too closely at RetroShare, but it seems unlikely to be used by my mother to send me a copy of that good ‘ol chocolate chip cookie recipe … you know, the one with 1/2 cup lard to make everything taste sooo delicious.
On another note: running a darknet client can be very dangerous if you are not precisely sure what you are doing.
Sadly… my recommendation for most people is to sign up for gmail. Sure, they and the NSA and probably Armenian 1337 hax0rs will now know that lard is yummy – but at least it’s likely that malware won’t be loaded onto your machine within 2 minutes and 5 seconds of connecting to gmail servers.
Lastly, 2factor works well – but it’s not perfect.
Lastly, lastly, if someone is using gmail for business… please… please… pretty please… setup SPF, DKIM, and DMARC… these three together prevent most spam mail through server to server to DNS to server checks.
The Internet is drowning in spam traffic. Do your part to clean it up a bit, and configure the tools that Google provides… they give you everything except pressing the buttons for you.
Sorry for the mini-rant, two things that boil my blood are spam and google — both are preventable with proper protection.
@DS:
I’m not sure running a P2P darknet client is going to help most people.
I haven’t looked too closely at RetroShare, but it seems unlikely to be used by my mother to send me a copy of that good ‘ol chocolate chip cookie recipe … you know, the one with 1/2 cup lard to make everything taste sooo delicious.
On another note: running a darknet client can be very dangerous if you are not precisely sure what you are doing.
Sadly… my recommendation for most people is to sign up for gmail. Sure, they and the NSA and probably Armenian 1337 hax0rs will now know that lard is yummy – but at least it’s likely that malware won’t be loaded onto your machine within 2 minutes and 5 seconds of connecting to gmail servers.
Lastly, 2factor works well – but it’s not perfect.
Lastly, lastly, if someone is using gmail for business… please… pretty please… setup SPF, DKIM, and DMARC… these three together prevent most spam mail through server to server to DNS to server checks.
The Internet is drowning in spam traffic. Do your part to clean it up a bit, and configure the tools that Google provides… they give you everything except pressing the buttons for you.
Sorry for the mini-rant, two things that boil my blood are spam and google — both are preventable with proper protection.
Hey!
Double post… how did that happen?
There was some sort of error message upon submission. I suppose the error did not prevent the post.
@dotmatrix
You’re repeating yourself. (kidding)
Well, I might have said that already, before, somewhere, sometime, or somehow, I already don’t know.
However, what I can remember is comment from one expert at the Davos who’s conclusion is that we need to be more aware of the things that are on the Internet.
My message is that we are more than aware of the Internet, what do we need is the Internet that is working properly, so that it is intended for people who are real people.
Yes, I know they have many global players with their points of view, but I need to say we know what is it about, so guys stop biting about bush and do right thing.
Well it is up to you guys!
Hey Scott. Hello from Austin and thank you.
I’m a command line commando…I don’t mind using it but I have a list of 1200+ Reglue Kids and Reglue Computers with that list growing weekly. Some of our kids are 11 years old so command line Foo isn’t often an option for us. The older kids, yep…we mentor them at the cursor, but the younger kids not so much. However, their time approaches. ;-))
Hey guys and gals, we’ve got the coolest perk ever for our Indiegogo campaign, and we’re sharing it with you here in the comments section before announcing it on our front page. We’ve heard from you that getting through the captcha when you’re making a comment can sometimes be a pain. Well, now you’ll be able to post comments to our articles simply by typing your comment and clicking “Post Comment.” No captcha or filling in the email text box when you want to make a comment — and you’ll be able to edit your comments after you post them as well, just in case you made a typo.
Our “Frequent Commenters Membership,” available through our Indiegogo fundraiser, gets you your own account on FOSS Force. You login to your account and all of your commenting is captcha free — and the post will automatically go up using the username you give us when we set-up your account. In addition, after we get ten or so of you signed up, each week we’ll offer a discussion topic which will only be available to logged-in members. And down the road, we have even more ideas we might implement.
The memberships are available for a $25 contribution to our Indiegogo fundraising campaign. This is just one way we’ve come up with to say thank you for your support. To claim your membership, just go to our Indiegogo page now and make your contribution!
http://igg.me/at/foss-force/x/10540979
Oh, and whether you make a contribution or not, thank you for being a part of FOSS Force. 🙂