Heading into risky online territory? Consider running Tails 7.0, which now offers faster startup and a smoother setup for safer browsing.
About three weeks ago, the Linux distribution Tails — or The Amnesic Incognito Live System — released version 7.0, its first major point release in about 1 1/2 years.
Tails isn’t just any Linux distribution. It’s designed to allow you to travel safely on the internet, no matter what your destination.
In today’s world of constant cybersecurity attacks and third parties using our data against us, any chance we can take to obfuscate our information should be considered a win, and Tails nails it — and has been doing so for more than 16 years. These days it’s nailing it more than ever, thanks to its merger last year with the Tor Project, the organization behind The Onion Router — or Tor browser — which has always been at Tails’s core.
If you’re a Linux user, you know how important privacy and security are. If you’re only now considering making the jump to Linux, you might be doing so because you’re tired of Microsoft, Google, or Apple spying on you. Or maybe you travel a lot and don’t want to trust your data to random coffee shop networks.
Either way, with Linux, there are always tools to help keep your privacy safe and prevent censorship, and Tails is a constantly evolving one of those tools.
What is Tails?
Tails is a portable Linux distribution, meaning it can be easily run from a USB flash drive. It includes tools to assist you in your journey towards privacy and security. To run it, all you have to do is burn it to a USB flash drive, insert it into a computer, and boot the machine to the flash drive, much like you do with any “live” OS.
You can then use Tails for whatever purpose you need, and when you’re finished reboot the computer — removing the flash drive when you see the black screen. Nothing on your computer will have changed; Tails didn’t so much as bother one byte on the drive; the installed OS is intact and ready to use. In other words, Tails leaves no trace behind. You don’t have to worry that whoever uses the computer next can see what you did or where you went with Tails.
Tails uses the Tor network to not only encrypt your data but also to mask your IP address. On top of that, you’ll find applications that you can use to work on sensitive documents, along with the ability to communicate securely. Every component within Tails has been configured to be safe, right out of the box.
What’s new in Tails 7.0
The latest version of Tails includes some important updates that users should appreciate. These include:
- Faster Boot Times: In the latest iteration of Tails 7.0, the boot time gets a boost, thanks to zstd compression for its USB and ISO images. By doing this, the boot time has been reduced by up to 10–15 seconds.
- Updated Base: Tails 7.0 is now based on Debian 13 with a desktop of GNOME 48.
- Improved Hardware Support: Thanks to the latest kernel (6.12.43), which brings with it better hardware support for the likes of GPUs and Wi-Fi adapters.
- Application Updates: Tails 7.0 brings with it several core application updates, such as Tor Browser (version 14.5.7), and the latest versions of Thunderbird, GIMP, and Audacity.
- GNOME Core Applications: GNOME 48 includes a new terminal app (replacing GNOME Terminal) and a new image viewer, GNOME Loupe.
- GNOME Desktop Environment: GNOME 48 brings with it several improvements, such as a redesigned Settings, and introduces a dynamic workspace indicator instead of the old Activities button.
- Increased minimum requirements: Tails 7.0 introduces higher RAM requirements, going from 2GB to 3GB.
You’ll also find two small changes within the UI, which are:
- The Places menu has been removed, but it’s still possible to access the same shortcuts from within the Files browser (in the sidebar).
- Kleopatra (the open source certificate manager) has been removed from the Favorites menu but is still accessible from the Apps menu.
How Tails Works
Tails can be installed on any USB flash drive that is 8GB or larger, and it works on nearly any machine that was built within the last decade, so you don’t have to worry about purchasing a new computer.
Tails always starts in a state of amnesia, so it does not remember what it was previously used for. As already mentioned, Tails leaves no trace for:
- Websites viewed
- Files opened
- Passwords
- Devices and wireless networks for which you’ve connected
You can even install Tails with persistent and encrypted storage, so you can save files and configurations. It’s not necessary to set it up with persistent storage, but if you think you’ll want to save some data between sessions, you’ll want to set this up. Persistent storage saves documents, Wi-Fi passwords, browser bookmarks, and more.
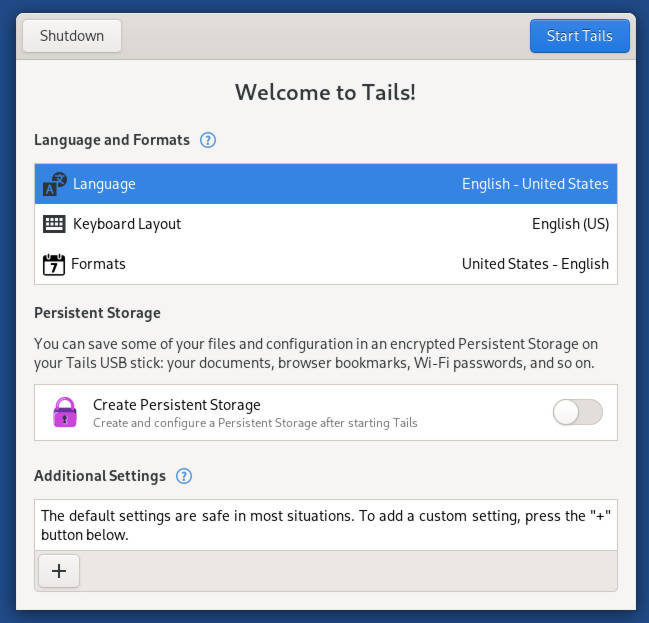
You’ll be given the option to install persistent storage when Tails boots (Figure 1). This will create a directory on your USB flash drive that will house the data you save. You will then be asked if you want to connect to Tor automatically or hide the network you use. I would suggest enabling Connect to Tor automatically.
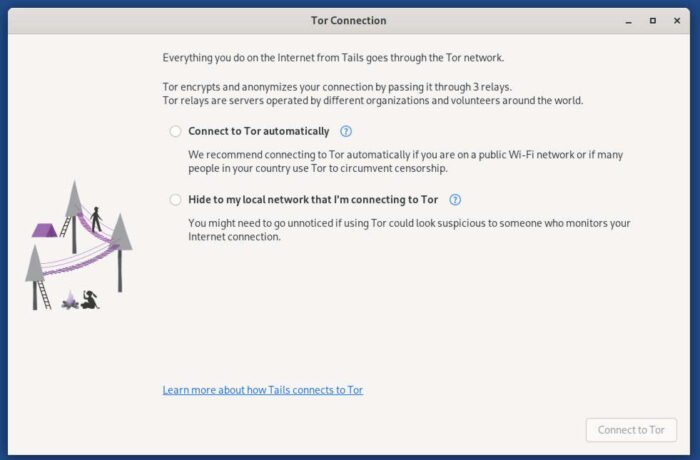
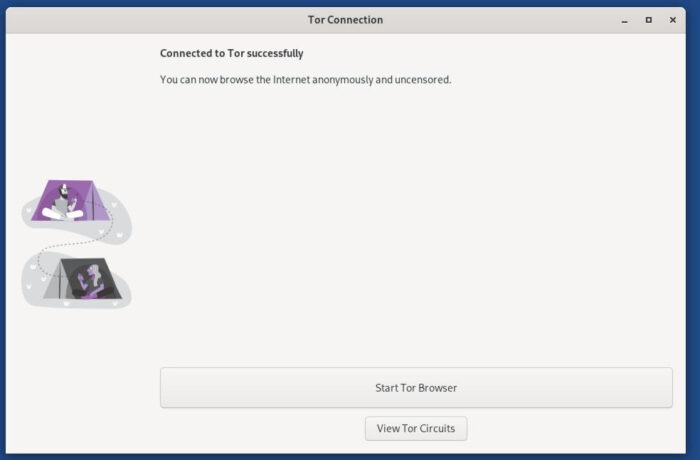
Click Connect to Tor, and the process will begin and end with another window asking if you want to start Tor Browser.
Tails Tools
Tails offers plenty of applications, geared toward or configured for security. Those apps include:
- Tor Browser
- Tor Connection
- Thunderbird
- KeePassXC
- LibreOffice
- OnionShare
- Metadata Cleaner
On top of all that, any application that attempts to bypass Tor for internet connections is automatically blocked.
You’ll also find plenty of other apps preinstalled for productivity, communication, multimedia, graphics, and more.
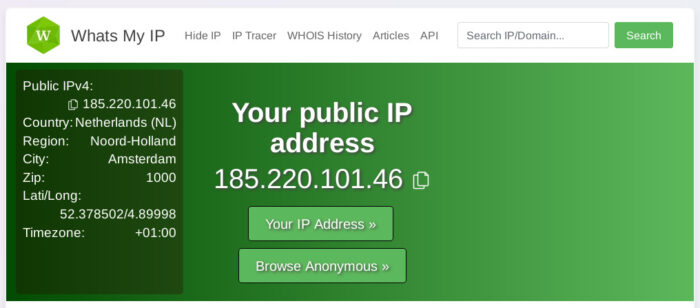
A quick way to ensure Tor is working would be to go to http://whatsmyip.com. You should see that both your IP address and your location have been obfuscated.
Keep in mind that any time you use Tor, your connectivity speeds will be slower than usual. This is normal, so don’t panic or start troubleshooting.
One thing I really appreciate about Tails is that it doesn’t just route Tor Browser traffic through the Tor Network; instead, all of your internet traffic goes through Tor, so every app is safer than it would be otherwise.
When you’re done using Tails, simply click the power button in the top right corner and shut the PC down. You can then remove the USB flash drive and boot the computer into the original OS.

Jack Wallen is an award-winning writer for TechRepublic, ZDNET, The New Stack, and Linux New Media. He’s covered a variety of topics for over twenty years and is an avid promoter of open source. Jack is also a novelist with over 50 published works of fiction. For more news about Jack Wallen, visit his website.