Samba -- once considered essential for desktop Linux users and which is still an essential part of enterprise operations -- is getting a big security makeover.
Posts published in “Security”
One surprise in this year's Cost of a Data Breach Report is that generative AI is being successfully used not only to prevent data breaches, but to substantially lower the cost of a breach when one happens.
As Paris attracts crowds sports tourists for the 2024 games, mobile apps marketed to attendees are tracking them, collecting their private data, and then hawking it to advertisers and big tech.
AlmaLinux is turning into the RHEL clone with a difference, by patching RHEL security holes that are given a low priority by Red Hat.
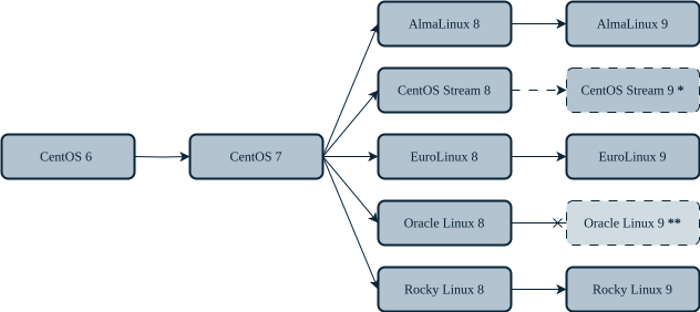
Although Sunday will be the last day that CentOS 7 will be officially supported, you don't have to move to something else right away. There are plenty of support services you can use to keep your workloads safe and secure until you're ready to migrate.
AlmaLinux can now develop and apply security patches and bug fixes ahead of RHEL, because it no longer seeks to be a line-by-line exact copy of Red Hat's operating system.
SJVN at ZDNet has all the ins and outs on what you can do (other than never reboot your computer) to protect yourself from LogoFAIL until a real fix comes along.
Are you afraid that someone's out to steal your passwords from your phone? Well, they might be, but they're probably not. Ars has published an article that explains it all.
On Tuesday, AlmaLinux announced that it has obtained FIPS 140-3 security certification for its Linux distro which is primarily used in data centers by enterprises.