The hackers who compromised the Linux Mint site on Saturday were evidently not the brightest stars in the dark web, but they managed to create a mess for the Mint crew to clear away.
Everybody understands that none of a stage magician’s tricks are real. The one thing that is real, and which a successful illusionist must practice to perfection, is the art of misdirection — which evidently turned out the be the trick under the sleeves of the cracker/hackers who were responsible for compromising ISO downloads of Linux Mint 17.3 Cinnamon on Saturday.
In the FOSS Force news article on the hack which ran Sunday, we said “the hackers modified the ISO of the Cinnamon edition of Linux Mint 17.3 (Rosa).” We now know that’s not quite true, or at least not in the way we meant. The hackers didn’t bust into the Mint server and modify the binaries waiting to be grabbed by the mirror sites for downloads. Instead, this was a case of misdirection.
**
If you value this kind of coverage, please consider supporting our work through our FOSS Force Independence 2026 fundraiser.
**
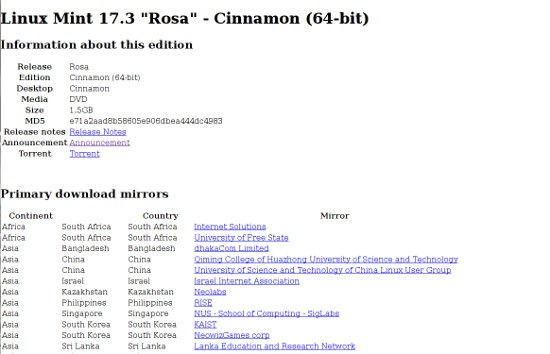
The hackers had a copy of Mint with their malicious payload in place, packaged as an ISO image and sitting on a Bulgarian server they controlled, waiting to serve downloads of what is arguably the worlds most popular version of GNU/Linux. The intrusion at Mint was a quick in-and-out to change the URLs in the anchor tags on Mint’s download page for the 64-bit Cinnamon version of Linux Mint 17.3 “Rosa.” Afterwards, users who clicked on a link to download from, say, the Internet Solutions mirror in South Africa, were taken to the hackers’ server in Bulgaria. Let the download begin. Wham, bam, thank you mam.
Christine Hall has been a journalist since 1971. In 2001, she began writing a weekly consumer computer column and started covering Linux and FOSS in 2002 after making the switch to GNU/Linux. Follow her on Twitter: @BrideOfLinux


 However, the German online publication Pro-Linux.de this week reported (in German, but Google Translate works wonders) that
However, the German online publication Pro-Linux.de this week reported (in German, but Google Translate works wonders) that 
 I wholeheartedly agree. However, there are entities like Microsoft whose open source endeavors are based solely on greed and who don’t deserve to wear the mantle of open source citizenship. They’re players, pure and simple. Microsoft only “loves” Linux because it has figured out a way to sell it. Maybe one day…but not today.
I wholeheartedly agree. However, there are entities like Microsoft whose open source endeavors are based solely on greed and who don’t deserve to wear the mantle of open source citizenship. They’re players, pure and simple. Microsoft only “loves” Linux because it has figured out a way to sell it. Maybe one day…but not today.

 More distros to choose from – February marked the arrivial of several new distros that Raspberry Pi users can now install.
More distros to choose from – February marked the arrivial of several new distros that Raspberry Pi users can now install.