FOSS Week in Review
The big Linux conference down in the land of Oz just completed and there are no really big shows on the agenda until Atlanta’s Great Wide Open opens its great doors wide in March. Everybody here in North Carolina, which I call home, is on the road, hanging out in Baghdad-by-the-Bay waiting to see how well the Panthers play in fog and trying to pretend to be old hats at having a pro home team worth the effort of a root or two.
You’d think it would be quiet around here, but it’s not. As always, it’s one thing after another, and as a coworker often often says, I’m getting too old for this. I could tell you stories, but I’m not. What I am going to tell you is the high points of this week in FOSS…
If you’re a Windows user, which most of you reading FOSS Force aren’t, then Microsoft wants to hijack your machine. It seems that the company that’s been spending millions — and has been buying into every free and open source conference it can find and a few it can’t — to get the word out that “Microsoft has changed,” hasn’t. If you happen to be unlucky enough to be using Windows 7, 8 or 8.1, you’re probably beginning to realize this right about now.
Windows users might be well advised to think about unplugging their computers from the Internet when they’re not around to keep an eye on things or they’re likely to wake-up in the morning, or return home from work, to find they’re running Windows 10 instead of whatever version they know and love.
Christine Hall has been a journalist since 1971. In 2001, she began writing a weekly consumer computer column and started covering Linux and FOSS in 2002 after making the switch to GNU/Linux. Follow her on Twitter: @BrideOfLinux









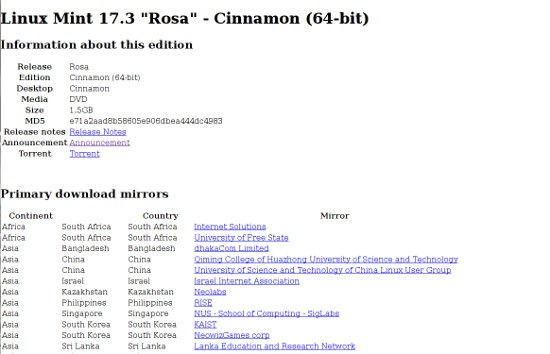
 The Great 2016 Linux Mint Hack: The hack at one of the crown jewels of Linux distros has undoubtedly been the biggest story this week. I’ll not bore you by repeating details which most of you have probably already read by now, but will direct those of you who don’t know to
The Great 2016 Linux Mint Hack: The hack at one of the crown jewels of Linux distros has undoubtedly been the biggest story this week. I’ll not bore you by repeating details which most of you have probably already read by now, but will direct those of you who don’t know to