Software. It’s been a thing that has fascinated me for decades. As a layman, the fact that lines of gibberish can be aligned to make a computer do the things wanted or needed is almost miraculous and resides in the shadows between magic and science. I am almost childlike when being shown how that gibberish makes devices do their stuff…stuff I want to do.
 What drives a person to do this? That whole “making my computer do what I want it to do” thing; how does a person even get their head around that in the first place? What was the specific moment in time when a person says, “I want to write software to make my computer do what I want it to do”?
What drives a person to do this? That whole “making my computer do what I want it to do” thing; how does a person even get their head around that in the first place? What was the specific moment in time when a person says, “I want to write software to make my computer do what I want it to do”?


 We learned of this on Friday through Tim Anderson at The Register, who supplied
We learned of this on Friday through Tim Anderson at The Register, who supplied 


 The trolls are still at it. In spite of the fact that the Supreme Court was busy ruling against them last year — between January and June it ruled against patent holders six times — the number of cases being brought by non-practicing entities (NPE), which is one measure of a troll, continues to rise. According to a report published in June by patent defense organization
The trolls are still at it. In spite of the fact that the Supreme Court was busy ruling against them last year — between January and June it ruled against patent holders six times — the number of cases being brought by non-practicing entities (NPE), which is one measure of a troll, continues to rise. According to a report published in June by patent defense organization 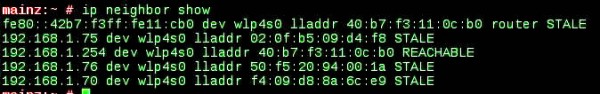

 None of them even approach usability for the everyday computer user. None. And you would think that of all these choices, one of them has to work…or provides documentation reasonable enough for everyone. You would think.
None of them even approach usability for the everyday computer user. None. And you would think that of all these choices, one of them has to work…or provides documentation reasonable enough for everyone. You would think.


 MS Writes a Check: Well, this was probably inevitable. With a generous donation, Microsoft has become a gold contributor to the OpenBSD project — the first gold contributor — in an effort to get OpenBSD’s help in porting OpenSSH to Windows. This comes from a
MS Writes a Check: Well, this was probably inevitable. With a generous donation, Microsoft has become a gold contributor to the OpenBSD project — the first gold contributor — in an effort to get OpenBSD’s help in porting OpenSSH to Windows. This comes from a 
