Judge grants IBM’s request for summary judgement and orders parties to reach dismissal agreement by February 26.
Two SCO stories in a week? As Yogi Berra would say, it’s 2003 all over again. But this time with a big difference. It’s almost over.
I told you on Monday that Judge David Nuffer with the US District Court in Utah had shot down SCO’s attempts to bring an action for Unfair Competition against IBM because the issue is already covered by another breach of contract claim by SCO. On Tuesday, Judge Nuffer issued a ruling on a pair of interference claims which effectively takes whatever winds were left out of SCO’s sails.
Bankrupt SCO, of course, lost their big $1 billion case against IBM long ago when Novell, in a separate case, proved that it, and not SCO, owned the copyrights that SCO was suing over. But SCO’s been struggling to stay alive, hoping to at least win a few bucks from IBM as compensation for all it went through.
Christine Hall has been a journalist since 1971. In 2001, she began writing a weekly consumer computer column and started covering Linux and FOSS in 2002 after making the switch to GNU/Linux. Follow her on Twitter: @BrideOfLinux


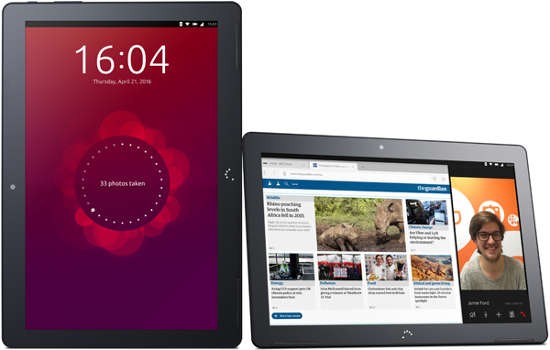


 The device will be the first fully functional mobile device running Ubuntu’s mobile platform available in the U.S. Although BQ has made Ubuntu phones available to U.S. customers for some time now, they’re not compatible with U.S. carriers’ systems and offer, at best, 2G capability. The tablet is a Wi-Fi device with no cellular conductivity and so won’t be hampered in any way when used in the U.S.
The device will be the first fully functional mobile device running Ubuntu’s mobile platform available in the U.S. Although BQ has made Ubuntu phones available to U.S. customers for some time now, they’re not compatible with U.S. carriers’ systems and offer, at best, 2G capability. The tablet is a Wi-Fi device with no cellular conductivity and so won’t be hampered in any way when used in the U.S.