Changes to Firefox's add-on policies that were announced on Wednesday, focus on privacy and security and will go into effect on December 1, 2021.
Posts tagged as “security”
After announcing in September that 500 million accounts had been compromised in a 2014 security breach, the company announces today that an additional billion accounts have been hacked in a separate incident.

Breaking News
If you’re a Yahoo user, you should strongly consider closing your account. If you decide to keep your account open, you might as well post your username and password to Facebook and send them out in a tweet, for all the good Yahoo’s security precautions will do for you.
Christine Hall has been a journalist since 1971. In 2001, she began writing a weekly consumer computer column and started covering Linux and FOSS in 2002 after making the switch to GNU/Linux. Follow her on Twitter: @BrideOfLinux
In the same week that we learned from W3Techs that the popular open source content management system (CMS) WordPress now powers a full 25 percent of all sites on the web, we learn that six popular WordPress plugins contain serious security vulnerabilities. The later news comes to us by way of security firm Wordfence, which specializes in WordPress security and develops the Wordfence security plugin for the platform.
![]() This news isn’t surprising, nor is it cause for alarm. Because WordPress is by far the most popular content management platform on the web, it’s an obvious target for hackers, and third party plugins are the most obvious way inside. However, the folks at Automattic, which develops the platform, have proven themselves to be diligent at finding vulnerabilities and keeping them patched.
This news isn’t surprising, nor is it cause for alarm. Because WordPress is by far the most popular content management platform on the web, it’s an obvious target for hackers, and third party plugins are the most obvious way inside. However, the folks at Automattic, which develops the platform, have proven themselves to be diligent at finding vulnerabilities and keeping them patched.
Christine Hall has been a journalist since 1971. In 2001, she began writing a weekly consumer computer column and started covering Linux and FOSS in 2002 after making the switch to GNU/Linux. Follow her on Twitter: @BrideOfLinux
It was in 2009. I possessed the best laptop that I had ever owned…to that point in time anyway. Small, but not cramped. A display that was beyond any adjective. “Dazzling” is what comes to mind, but many would probably categorize that as marketing hyperbole. That’s fine. That laptop lasted almost to the end of 2013 before the motherboard suffered catastrophic failure. I had received the machine already much used. I liked it so much I actually mourned my loss.
 I never found one that was even close to the quality of my Lenovo X60s…until recently.
I never found one that was even close to the quality of my Lenovo X60s…until recently.
Ken Starks is the founder of the Helios Project and Reglue, which for 20 years provided refurbished older computers running Linux to disadvantaged school kids, as well as providing digital help for senior citizens, in the Austin, Texas area. He was a columnist for FOSS Force from 2013-2016, and remains part of our family. Follow him on Twitter: @Reglue
It always happens to someone else. Right? I mean, what are the chances it will happen to me? Or you? Be it winning the lottery or developing a debilitating disease. We all know someone who knows someone who…well, you know how it goes. It will happen to someone else.
And it did, two days ago. Across the street from me.
 Claude and Jane are good folks. Both in their mid 70s. They live on their combined retirement funds and spend their time keeping busy with kids, grandkids, and from what I hear, a great-grandchild in a matter of months. They come over for coffee or tea at times, and we always see them at community center events. They are not well off by any standard, but they do okay…until last Saturday.
Claude and Jane are good folks. Both in their mid 70s. They live on their combined retirement funds and spend their time keeping busy with kids, grandkids, and from what I hear, a great-grandchild in a matter of months. They come over for coffee or tea at times, and we always see them at community center events. They are not well off by any standard, but they do okay…until last Saturday.
Ken Starks is the founder of the Helios Project and Reglue, which for 20 years provided refurbished older computers running Linux to disadvantaged school kids, as well as providing digital help for senior citizens, in the Austin, Texas area. He was a columnist for FOSS Force from 2013-2016, and remains part of our family. Follow him on Twitter: @Reglue
Your digital rights — do both your hardware and software respect them?
Because if they don’t, Purism might have the answer to this shortcoming.
At OSCON, Purism has on hand the Librem 13 and Librem 15 laptops – the numbers designating the screen size (13-inch and 15-inch, respectively) — which are both designed, chip-by-chip and line-by-line to respect your rights to privacy, security and freedom, which is Purism’s philosophy.
 “We developed Purism so that users can have access to the highest quality computers without compromising these beliefs,” the Purism website states. “The founder of Purism developed the Philosophical Contract, that we all abide by, which was adopted from the Free Software Foundation, and expanded to include hardware manufacturing as it relates to software.”
“We developed Purism so that users can have access to the highest quality computers without compromising these beliefs,” the Purism website states. “The founder of Purism developed the Philosophical Contract, that we all abide by, which was adopted from the Free Software Foundation, and expanded to include hardware manufacturing as it relates to software.”
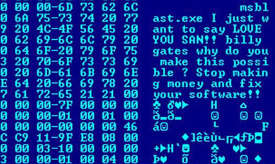
Don Parris wears a Facility Services cape by day, and transforms into LibreMan at night. He has written numerous articles about free tech, and hangs out with the Cha-Ha crowd, learning about computer security. He also enjoys making ceviche with his wife, and writing about his travels in Perú.
Today I spent some time looking at a white paper issued by the security firm Symantec called Website Security Threat Report, which is basically a catalog of malware threats for the non-techie suits who control the purse strings for web facing server deployments — sort of a “here boss, this is why we have to spend so much money on security” type of thing. Most of it’s old news to those of us who, for whatever reason, follow tech news, but some of the trends noted by the folks at Symantec are interesting enough.
As a matter of fact, there’s a bit of sobering news for sites like FOSS Force, as again in 2014, technology sites top the list of the type of sites most likely to be exploited by cracker hackers, with the number on the rise. According to Symantec, last year tech sites represented 21.5 percent of sites infected by malware, up from 9.9 percent in 2013. Even more disturbing is that number two on this list are hosting sites, up from the number three position in 2013, with 7.3 percent of malware infected sites.
Christine Hall has been a journalist since 1971. In 2001, she began writing a weekly consumer computer column and started covering Linux and FOSS in 2002 after making the switch to GNU/Linux. Follow her on Twitter: @BrideOfLinux




 Although some have been trying to sound the alarm, many of us have been lulled into complacency brought by a belief that Microsoft is no longer a real threat and that we are now free to concentrate all of our energies on growing Linux and FOSS, which is basically all we’ve wanted to do.
Although some have been trying to sound the alarm, many of us have been lulled into complacency brought by a belief that Microsoft is no longer a real threat and that we are now free to concentrate all of our energies on growing Linux and FOSS, which is basically all we’ve wanted to do.


 We learned of this on Friday through Tim Anderson at The Register, who supplied
We learned of this on Friday through Tim Anderson at The Register, who supplied 